360 Total Security 2016 suffers from a dll hijacking vulnerability.
Monthly Archives: July 2016
Hackers Can Steal Your ATM PIN from Your Smartwatch Or Fitness Tracker
As your day-to-day apparel and accessories are turning into networked mobile electronic devices that attach to your body like smartwatch or fitness band, the threat to our personal data these devices collect has risen exponentially.
A recent study from Binghamton University also suggests your smartwatch or fitness tracker is not as secure as you think – and it could be used to steal your ATM
![]()
The Blue Screen of Death Gets a New Look
What a terrible feeling we have when the blue screen of death pops up. Dotted with white letters, this uh oh screen can show up unexpectedly on any old Windows-using computer. Seeing this screen will make anyone think, did my computer just DIE?
To fix the problem, the infamous screen of death reads that we should close all programs that could have provoked the issue or restart the computer altogether (using Ctrl+Alt+Supr). If we are lucky, the issue will go away after following these steps, but most of the time it won’t be that easy.
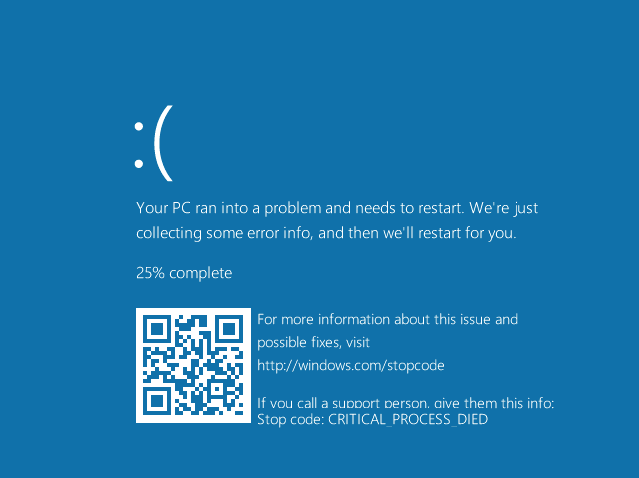
Now, this oh-so-hated blue screen of Windows has had a face-lift, making it just as terrible but a little nicer to look at. The newest version on Windows 10 (out this summer) will display a sad emoticon and a QR code that will send you to a help area once it is scanned.
The bad news is that these two-dimensional codes, or more precisely the links they contain, can be very powerful tools for cybercriminals.
First, a cybercriminal could simulate that your computer has an error, and send your computer a fake “blue screen of death”. Then the criminal could add a QR code with a link that will take you to an unexpected and malicious website that will install drive-by malware on your computer.
If the cybercriminal wants to be very sly, they could design an entire website that looks like an official Microsoft one and use it to phish for log-in information and personal data. Uneducated computer users are the easiest victims for this type of trap.
The QR code that appears on the Screen of Death can be used for phishing or downloading malware onto your computer
But using QR codes to camouflage links is nothing new. The best way to protect yourself from this type of attack is to keep your guard up. Don’t scan a two-dimensional code without knowing where it will take you and if that website is a safe place.
To defend yourself against these kind of attacks, it is essential to have a good antivirus that will detect any kind of phishing or malware that is attempting to download on your computer.
The post The Blue Screen of Death Gets a New Look appeared first on Panda Security Mediacenter.
Dropping Elephant: Cyber-espionage Group Hunts High Profile Targets with Low Profile Tools
Kaspersky Lab announced today its researchers investigated a threat actor that was undertaking aggressive cyber-espionage activity in the Asian region
BMW ConnectedDrive – (Update) VIN Session Vulnerability
Posted by Vulnerability Lab on Jul 08
Document Title:
===============
BMW ConnectedDrive – (Update) VIN Session Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1736
Release Date:
=============
2016-07-07
Vulnerability Laboratory ID (VL-ID):
====================================
1736
Common Vulnerability Scoring System:
====================================
6
Product & Service Introduction:…
BMW – (Token) Client Side Cross Site Scripting Vulnerability
Posted by Vulnerability Lab on Jul 08
Document Title:
===============
BMW – (Token) Client Side Cross Site Scripting Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1737
Release Date:
=============
2016-07-06
Vulnerability Laboratory ID (VL-ID):
====================================
1737
Common Vulnerability Scoring System:
====================================
3.6
Product & Service Introduction:…
Bugtraq: [slackware-security] samba (SSA:2016-189-01)
[slackware-security] samba (SSA:2016-189-01)
Bugtraq: [security bulletin] HPSBGN03628 rev.1 – HPE IceWall Federation Agent using libXML2 library, Remote Denial of Service (DoS), Unauthorized Modification, Unauthorized Disclosure of Information
[security bulletin] HPSBGN03628 rev.1 – HPE IceWall Federation Agent using libXML2 library, Remote Denial of Service (DoS), Unauthorized Modification, Unauthorized Disclosure of Information
Bugtraq: Microsoft WinDbg logviewer.exe Buffer Overflow DOS
Microsoft WinDbg logviewer.exe Buffer Overflow DOS
Bugtraq: Microsoft Process Kill Utility "kill.exe" Buffer Overflow
Microsoft Process Kill Utility “kill.exe” Buffer Overflow