Red Hat Enterprise Linux: A new oci-register-machine package is available for Red Hat Enterprise Linux 7
Extras.
Monthly Archives: August 2016
USN-3047-1: QEMU vulnerabilities
Ubuntu Security Notice USN-3047-1
4th August, 2016
qemu, qemu-kvm vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 16.04 LTS
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
Summary
Several security issues were fixed in QEMU.
Software description
- qemu
– Machine emulator and virtualizer - qemu-kvm
– Machine emulator and virtualizer
Details
Li Qiang discovered that QEMU incorrectly handled 53C9X Fast SCSI
controller emulation. A privileged attacker inside the guest could use this
issue to cause QEMU to crash, resulting in a denial of service, or possibly
execute arbitrary code on the host. In the default installation, when QEMU
is used with libvirt, attackers would be isolated by the libvirt AppArmor
profile. This issue only applied to Ubuntu 14.04 LTS and Ubuntu 16.04 LTS.
(CVE-2016-4439, CVE-2016-4441, CVE-2016-5238, CVE-2016-5338, CVE-2016-6351)
Li Qiang and Qinghao Tang discovered that QEMU incorrectly handled the
VMWare VGA module. A privileged attacker inside the guest could use this
issue to cause QEMU to crash, resulting in a denial of service, or possibly
to obtain sensitive host memory. (CVE-2016-4453, CVE-2016-4454)
Li Qiang discovered that QEMU incorrectly handled VMWARE PVSCSI paravirtual
SCSI bus emulation support. A privileged attacker inside the guest could
use this issue to cause QEMU to crash, resulting in a denial of service.
This issue only applied to Ubuntu 14.04 LTS and Ubuntu 16.04 LTS.
(CVE-2016-4952)
Li Qiang discovered that QEMU incorrectly handled MegaRAID SAS 8708EM2 Host
Bus Adapter emulation support. A privileged attacker inside the guest could
use this issue to cause QEMU to crash, resulting in a denial of service, or
possibly to obtain sensitive host memory. This issue only applied to Ubuntu
14.04 LTS and Ubuntu 16.04 LTS. (CVE-2016-5105, CVE-2016-5106,
CVE-2016-5107, CVE-2016-5337)
It was discovered that QEMU incorrectly handled certain iSCSI asynchronous
I/O ioctl calls. An attacker inside the guest could use this issue to cause
QEMU to crash, resulting in a denial of service, or possibly execute
arbitrary code on the host. In the default installation, when QEMU is used
with libvirt, attackers would be isolated by the libvirt AppArmor profile.
This issue only applied to Ubuntu 14.04 LTS and Ubuntu 16.04 LTS.
(CVE-2016-5126)
Zhenhao Hong discovered that QEMU incorrectly handled the Virtio module. A
privileged attacker inside the guest could use this issue to cause QEMU to
crash, resulting in a denial of service. (CVE-2016-5403)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 16.04 LTS:
-
qemu-system-misc
1:2.5+dfsg-5ubuntu10.3
-
qemu-system-s390x
1:2.5+dfsg-5ubuntu10.3
-
qemu-system
1:2.5+dfsg-5ubuntu10.3
-
qemu-system-aarch64
1:2.5+dfsg-5ubuntu10.3
-
qemu-system-x86
1:2.5+dfsg-5ubuntu10.3
-
qemu-system-sparc
1:2.5+dfsg-5ubuntu10.3
-
qemu-system-arm
1:2.5+dfsg-5ubuntu10.3
-
qemu-system-ppc
1:2.5+dfsg-5ubuntu10.3
-
qemu-system-mips
1:2.5+dfsg-5ubuntu10.3
- Ubuntu 14.04 LTS:
-
qemu-system-misc
2.0.0+dfsg-2ubuntu1.26
-
qemu-system
2.0.0+dfsg-2ubuntu1.26
-
qemu-system-aarch64
2.0.0+dfsg-2ubuntu1.26
-
qemu-system-x86
2.0.0+dfsg-2ubuntu1.26
-
qemu-system-sparc
2.0.0+dfsg-2ubuntu1.26
-
qemu-system-arm
2.0.0+dfsg-2ubuntu1.26
-
qemu-system-ppc
2.0.0+dfsg-2ubuntu1.26
-
qemu-system-mips
2.0.0+dfsg-2ubuntu1.26
- Ubuntu 12.04 LTS:
-
qemu-kvm
1.0+noroms-0ubuntu14.29
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
After a standard system update you need to restart all QEMU virtual
machines to make all the necessary changes.
References
USN-3044-1: Firefox vulnerabilities
Ubuntu Security Notice USN-3044-1
5th August, 2016
firefox vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 16.04 LTS
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
Summary
Firefox could be made to crash or run programs as your login if it
opened a malicious website.
Software description
- firefox
– Mozilla Open Source web browser
Details
Gustavo Grieco discovered an out-of-bounds read during XML parsing in
some circumstances. If a user were tricked in to opening a specially
crafted website, an attacker could potentially exploit this to cause a
denial of service via application crash, or obtain sensitive information.
(CVE-2016-0718)
Toni Huttunen discovered that once a favicon is requested from a site,
the remote server can keep the network connection open even after the page
is closed. A remote attacked could potentially exploit this to track
users, resulting in information disclosure. (CVE-2016-2830)
Christian Holler, Tyson Smith, Boris Zbarsky, Byron Campen, Julian Seward,
Carsten Book, Gary Kwong, Jesse Ruderman, Andrew McCreight, and Phil
Ringnalda discovered multiple memory safety issues in Firefox. If a user
were tricked in to opening a specially crafted website, an attacker could
potentially exploit these to cause a denial of service via application
crash, or execute arbitrary code. (CVE-2016-2835, CVE-2016-2836)
A buffer overflow was discovered in the ClearKey Content Decryption
Module (CDM) during video playback. If a user were tricked in to opening
a specially crafted website, an attacker could potentially exploit this to
cause a denial of service via plugin process crash, or, in combination
with another vulnerability to escape the GMP sandbox, execute arbitrary
code. (CVE-2016-2837)
Atte Kettunen discovered a buffer overflow when rendering SVG content in
some circumstances. If a user were tricked in to opening a specially
crafted website, an attacker could potentially exploit this to cause a
denial of service via application crash, or execute arbitrary code.
(CVE-2016-2838)
Bert Massop discovered a crash in Cairo with version 0.10 of FFmpeg. If a
user were tricked in to opening a specially crafted website, an attacker
could potentially exploit this to execute arbitrary code. (CVE-2016-2839)
Catalin Dumitru discovered that URLs of resources loaded after a
navigation start could be leaked to the following page via the Resource
Timing API. An attacker could potentially exploit this to obtain sensitive
information. (CVE-2016-5250)
Firas Salem discovered an issue with non-ASCII and emoji characters in
data: URLs. An attacker could potentially exploit this to spoof the
addressbar contents. (CVE-2016-5251)
Georg Koppen discovered a stack buffer underflow during 2D graphics
rendering in some circumstances. If a user were tricked in to opening a
specially crafted website, an attacker could potentially exploit this to
cause a denial of service via application crash, or execute arbitrary
code. (CVE-2016-5252)
Abhishek Arya discovered a use-after-free when the alt key is used with
top-level menus. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to cause a denial of
service via application crash, or execute arbitrary code. (CVE-2016-5254)
Jukka Jylänki discovered a crash during garbage collection. If a user
were tricked in to opening a specially crafted website, an attacker could
potentially exploit this to execute arbitrary code. (CVE-2016-5255)
Looben Yang discovered a use-after-free in WebRTC. If a user were tricked
in to opening a specially crafted website, an attacker could potentially
exploit this to cause a denial of service via application crash, or
execute arbitrary code. (CVE-2016-5258)
Looben Yang discovered a use-after-free when working with nested sync
events in service workers. If a user were tricked in to opening a
specially crafted website, an attacker could potentially exploit this to
cause a denial of service via application crash, or execute arbitrary
code. (CVE-2016-5259)
Mike Kaply discovered that plain-text passwords can be stored in session
restore if an input field type is changed from “password” to “text” during
a session, leading to information disclosure. (CVE-2016-5260)
Samuel Groß discovered an integer overflow in WebSockets during data
buffering in some circumstances. If a user were tricked in to opening a
specially crafted website, an attacker could potentially exploit this to
cause a denial of service via application crash, or execute arbitrary
code. (CVE-2016-5261)
Nikita Arykov discovered that JavaScript event handlers on a <marquee>
element can execute in a sandboxed iframe without the allow-scripts flag
set. If a user were tricked in to opening a specially crafted website, an
attacker could potentially exploit this to conduct cross-site scripting
(XSS) attacks. (CVE-2016-5262)
A type confusion bug was discovered in display transformation during
rendering. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to cause a denial of
service via application crash, or execute arbitrary code. (CVE-2016-5263)
A use-after-free was discovered when applying effects to SVG elements in
some circumstances. If a user were tricked in to opening a specially
crafted website, an attacker could potentially exploit this to cause a
denial of service via application crash, or execute arbitrary code.
(CVE-2016-5264)
Abdulrahman Alqabandi discovered a same-origin policy violation relating
to local HTML files and saved shortcut files. An attacker could
potentially exploit this to obtain sensitive information. (CVE-2016-5265)
Rafael Gieschke discovered an information disclosure issue related to
drag and drop. An attacker could potentially exploit this to obtain
sensitive information. (CVE-2016-5266)
A text injection issue was discovered with about: URLs. An attacker could
potentially exploit this to spoof internal error pages. (CVE-2016-5268)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 16.04 LTS:
-
firefox
48.0+build2-0ubuntu0.16.04.1
- Ubuntu 14.04 LTS:
-
firefox
48.0+build2-0ubuntu0.14.04.1
- Ubuntu 12.04 LTS:
-
firefox
48.0+build2-0ubuntu0.12.04.1
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
After a standard system update you need to restart Firefox to make
all the necessary changes.
References
USN-3041-1: Oxide vulnerabilities
Ubuntu Security Notice USN-3041-1
5th August, 2016
oxide-qt vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 16.04 LTS
- Ubuntu 14.04 LTS
Summary
Several security issues were fixed in Oxide.
Software description
- oxide-qt
– Web browser engine for Qt (QML plugin)
Details
Multiple security issues were discovered in Chromium. If a user were
tricked in to opening a specially crafted website, an attacker could
potentially exploit these to read uninitialized memory, cause a denial
of service (application crash) or execute arbitrary code. (CVE-2016-1705)
It was discovered that the PPAPI implementation does not validate the
origin of IPC messages to the plugin broker process. A remote attacker
could potentially exploit this to bypass sandbox protection mechanisms.
(CVE-2016-1706)
It was discovered that Blink does not prevent window creation by a
deferred frame. A remote attacker could potentially exploit this to bypass
same origin restrictions. (CVE-2016-1710)
It was discovered that Blink does not disable frame navigation during a
detach operation on a DocumentLoader object. A remote attacker could
potentially exploit this to bypass same origin restrictions.
(CVE-2016-1711)
A use-after-free was discovered in Blink. If a user were tricked in to
opening a specially crafted website, an attacker could potentially exploit
this to cause a denial of service via renderer process crash, or execute
arbitrary code. (CVE-2016-5127)
It was discovered that objects.cc in V8 does not prevent API interceptors
from modifying a store target without setting a property. A remote
attacker could potentially exploit this to bypass same origin
restrictions. (CVE-2016-5128)
A memory corruption was discovered in V8. If a user were tricked in to
opening a specially crafted website, an attacker could potentially exploit
this to cause a denial of service via renderer process crash, or execute
arbitrary code. (CVE-2016-5129)
A security issue was discovered in Chromium. A remote attacker could
potentially exploit this to spoof the currently displayed URL.
(CVE-2016-5130)
A use-after-free was discovered in libxml. If a user were tricked in to
opening a specially crafted website, an attacker could potentially exploit
this to cause a denial of service via renderer process crash, or execute
arbitrary code. (CVE-2016-5131)
The Service Workers implementation in Chromium does not properly implement
the Secure Contexts specification during decisions about whether to
control a subframe. A remote attacker could potentially exploit this to
bypass same origin restrictions. (CVE-2016-5132)
It was discovered that Chromium mishandles origin information during proxy
authentication. A man-in-the-middle attacker could potentially exploit this
to spoof a proxy authentication login prompt. (CVE-2016-5133)
It was discovered that the Proxy Auto-Config (PAC) feature in Chromium
does not ensure that URL information is restricted to a scheme, host and
port. A remote attacker could potentially exploit this to obtain sensitive
information. (CVE-2016-5134)
It was discovered that Blink does not consider referrer-policy information
inside an HTML document during a preload request. A remote attacker could
potentially exploit this to bypass Content Security Policy (CSP)
protections. (CVE-2016-5135)
It was discovered that the Content Security Policy (CSP) implementation in
Blink does not apply http :80 policies to https :443 URLs. A remote
attacker could potentially exploit this to determine whether a specific
HSTS web site has been visited by reading a CSP report. (CVE-2016-5137)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 16.04 LTS:
-
liboxideqtcore0
1.16.5-0ubuntu0.16.04.1
- Ubuntu 14.04 LTS:
-
liboxideqtcore0
1.16.5-0ubuntu0.14.04.1
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
In general, a standard system update will make all the necessary changes.
References
One Hardcore Gamer’s Take on Pokemon Go
An inside look into how Nintendo’s popular mobile game is bridging generational gaps and keeping you outside through the lens of one avid gamer. This piece originally appeared on GamesBeat.
All technical woes aside, Pokémon Go—which I’ve been playing nonstop since its release now—is a lot of fun. While it may not offer the complex gameplay, storytelling, or character development the past decade of Hollywood-standard video games has delivered, it’s engrossing — and its astronomic growth is a phenomenon.
Which got me thinking … what does account for the appeal? As a way to come up with an answer, I’ve made these four observations, which are as much about human nature as they are about gaming culture.
1. It’s just like that one Star Trek: The Next Generation episode
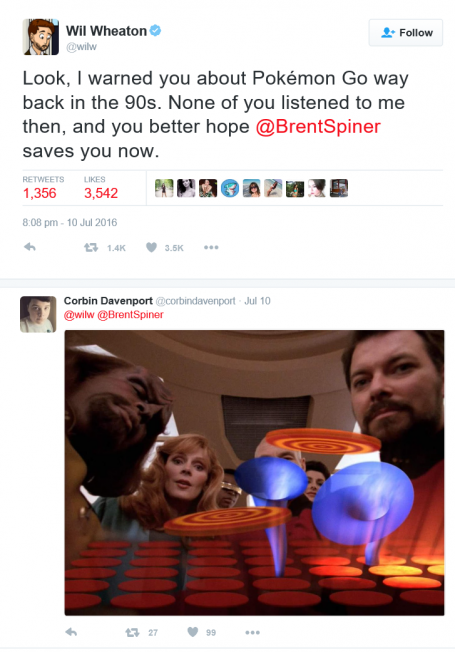
Pokémon Go has been compared to The Matrix, Ready Player One, and just about every other dystopia where technology controls humans. But while Pokémon Go arguably is an addictive worldwide phenomenon whose ultimate reach is yet to be determined … wait, am I talking myself out of my own conclusion that it’s not actually dangerous to society? OK, it’s not, seriously. It does, however, remind me to an eerie degree of “The Game” episode of the Star Trek: The Next Generation TV series. In “The Game,” the crew of the Enterprise became obsessed with an augmented reality game in which the object is to throw a flat plate (Pokéball, anyone?) into a cone (Do I hear Pokémon?) in order to score and move to the next level.
Apparently I’m in good company, because Wil Wheaton, who played Wesley Crusher in that episode and later saved the Enterprise, even Tweeted about it.
The verdict: While Pokémon Go doesn’t (yet) seem to psychologically manipulate people, it is, for better or worse, mesmerizing. And people love to be mesmerized.
2. I want it to keep getting better
Nintendo was once known for stellar gameplay and mechanics, but it’s been struggling to keep up with Sony and Microsoft in the marketplace. Niantic’s Pokémon Go is the first hit associated with the Nintendo brand in quite a while. As someone who grew up with Nintendo games, I hope they can turn this into a comeback and that the excitement around Pokémon Go can catapult them back to their former glory. Nintendo needs to take Niantic’s start and increase the depth, interaction, and engagement. Right now it’s simple—catch, level, feed, fight, train. Lather, rinse, repeat. Even casual gamers need more.
The Verdict: I guarantee I’m not alone in hoping Pokémon Go sticks around and gets more challenging, which just shows that people love a success story, especially when whoever’s being successful is somewhat of an underdog.
3. It bridges generation gaps

I never expected that playing Pokémon Go would bring me closer to generations I must admit I barely knew—or thought I could know.
Pokémon Go has connected me with people—while grocery shopping, going for my morning run, or just walking down the street. Within the first three days I was stopped by kids less than half my age and a couple more than twice my age.
On day 2, I noticed several tweens in the grocery store pointing at me, whispering, “Look at him. …” I turned to them, held up my phone, and asked, “Pokémon?” Nods, and big smiles. Nearly 30 minutes later, while hanging out at the cheese counter where they’d caught a monster, we’d talked about smartphones, gaming, school, grades, friends, sports … and I got an all-too-rare glimpse into what it’s like to be a kid in 2016.
Day 3 brought me face-to-face with an elderly couple who wondered, as they saw me stop and hold up my phone during a run through the forest, what I was taking a photo of. I told them what I was up to, and they were in awe of today’s technology. This, too, became a conversation about how maybe they needed phones, about where they’d grown up, their family, their work, their life.
All the scary stories about people being injured or lured to harm by strangers while playing Pokémon Go, while true, likely don’t happen nearly as often as the sort of positive experiences I had with people in my own community—people I probably never would have talked to, were it not for Pokémon Go.
The verdict: People want to connect, and it’s amazing how the shared experience of a cultural phenomenon like a game—or a movie, or a book, or a TV show—can forge common ground among people who otherwise couldn’t be more different. And the more we have these experiences, the more open we are to recreating them.
4. It makes you go outside
Truth be told, this aspect of Pokémon Go does make me feel a bit uneasy: while the game’s become mainstream in a very short time and is all over the news, you can’t expect every last person on earth to know what it is or how it’s played. Which could explain the suspicious looks I’ve gotten while wandering around my quiet family neighborhood. While nothing bad came of any neighbors’ quizzical looks, I’m sure there were moments of confused uneasiness, and if you’re going to play, you’re wise to consider your surroundings and be conscious of people’s privacy. And if you get “those” looks, explain it (or invite them to play, it could turn out well!—see observation 3).
But you can’t discount the really wonderful opportunity to explore areas near your home, work, or school that you may never have seen. I took it on my morning run (which usually follows the same route) and ended up going down beautiful forests paths I’d never seen and through neighborhoods I’d never been to. You’re essentially combining exercise, exploration, and gaming—which until now never really went together that well.
The verdict: While I am a bit torn about the overall benefits of Pokémon Go’s ability to bring you together with new people and new aspects of your everyday world (see: potentially freaking out the neighbors), there’s no doubt that its forcing players to go beyond routine is a big part of its appeal. People love adventure.
My verdict
Pokémon Go promotes exercise and getting outdoors … but it makes you look at your phone even more than you probably already do. And some of the things that account for its appeal—the fact that it’s somewhat mesmerizing—also have a flip side, in this case overly repetitive gameplay. You should play it, too, see for yourself, see if the appeal is well-founded, see if its current cult status is likely to last.
While I’ve noticed my interest waning (I spent hours on end in week 1 catching dozens of Pokémons and now use it only 15-30 minutes a day in week 2), I’m not sure yet if I’m getting tired of it overall, or if there’s going to be a “second wave” of excitement.
What’s your verdict?
![]()
![]()
Ecwid Ecommerce Shopping Cart WordPress Plugin unauthenticated PHP Object injection vulnerability
Posted by Summer of Pwnage on Aug 05
————————————————————————
Ecwid Ecommerce Shopping Cart WordPress Plugin unauthenticated PHP
Object injection vulnerability
————————————————————————
Yorick Koster, June 2016
————————————————————————
Abstract
————————————————————————
A PHP Object injection…
Cross-Site Scripting in Store Locator Plus for WordPress
Posted by Summer of Pwnage on Aug 05
————————————————————————
Cross-Site Scripting in Store Locator Plus for WordPress
————————————————————————
Yorick Koster, July 2016
————————————————————————
Abstract
————————————————————————
A Cross-Site Scripting vulnerability was found in Store Locator…
DLL side loading vulnerability in VMware Host Guest Client Redirector
Posted by Securify B.V. on Aug 05
————————————————————————
DLL side loading vulnerability in VMware Host Guest Client Redirector
————————————————————————
Yorick Koster, December 2015
————————————————————————
Abstract
————————————————————————
A DLL side loading vulnerability was found in the…
CVE-2015-8945 (origin)
openshift-node in OpenShift Origin 1.1.6 and earlier improperly stores router credentials as envvars in the pod when the –credentials option is used, which allows local users to obtain sensitive private key information by reading the systemd journal.
CVE-2016-0782
The administration web console in Apache ActiveMQ 5.x before 5.11.4, 5.12.x before 5.12.3, and 5.13.x before 5.13.2 allows remote authenticated users to conduct cross-site scripting (XSS) attacks and consequently obtain sensitive information from a Java memory dump via vectors related to creating a queue.