The m_authenticate function in modules/m_sasl.c in Charybdis before 3.5.3 allows remote attackers to spoof certificate fingerprints and consequently log in as another user via a crafted AUTHENTICATE parameter.
Monthly Archives: September 2016
CVE-2016-7154 (xen)
Use-after-free vulnerability in the FIFO event channel code in Xen 4.4.x allows local guest OS administrators to cause a denial of service (host crash) and possibly execute arbitrary code or obtain sensitive information via an invalid guest frame number.
CVE-2016-7163 (debian_linux, fedora, openjpeg)
Integer overflow in the opj_pi_create_decode function in pi.c in OpenJPEG allows remote attackers to execute arbitrary code via a crafted JP2 file, which triggers an out-of-bounds read or write.
CVE-2016-7166 (enterprise_linux_desktop, enterprise_linux_hpc_node, enterprise_linux_hpc_node_eus, enterprise_linux_server, enterprise_linux_server_aus, enterprise_linux_server_eus, enterprise_linux_workstation, libarchive)
libarchive before 3.2.0 does not limit the number of recursive decompressions, which allows remote attackers to cause a denial of service (memory consumption and application crash) via a crafted gzip file.
Warning — You Can't Install Linux On Microsoft Signature Edition PCs from Lenovo
In past few months, Microsoft opened the source code of a lot of its projects, convincing people that the company loves Linux.
But a new report shows that Microsoft is not really a big supporter of Linux.
Microsoft has banned Linux on some Windows 10 powered Signature Edition PCs, which provides the cleanest Windows experience on the market.
<!– adsense –>
Signature Edition PCs are
![]()
Mozilla Patches Certificate Pinning Vulnerability in Firefox
A remote code execution in Firefox caused by the expiration of certificate pins was patched by Mozilla in Firefox 49 and Firefox ESR 45.4.
Hey, Poker Face — This Wi-Fi Router Can Read Your Emotions
Are you good at hiding your feelings?
No issues, your Wi-Fi router may soon be able to tell how you feel, even if you have a good poker face.
A team of researchers at MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) have developed a device that can measure human inner emotional states using wireless signals.
Dubbed EQ-Radio, the new device measures heartbeat, and
![]()
Germany’s Federal Paramedics Competition – we were on-site

Staring allowed – that was this years slogan for the 56th federal Red Cross paramedics competition in Wangen. The competition was organized by a local association which was a first timer.
The post Germany’s Federal Paramedics Competition – we were on-site appeared first on Avira Blog.
Photos On Dark Web Reveal Geo-locations Of 229 Drug Dealers — Here's How
It’s a Fact! No matter how smart the criminals are, they always leave some trace behind.
Two Harvard students have unmasked around 229 drug and weapon dealers with the help of pictures taken by criminals and used in advertisements placed on dark web markets.
Do you know each image contains a range of additional hidden data stored within it that can be a treasure to the investigators fighting
![]()
Improved Efficiency and Centralized Management with the Latest Version of Panda Systems Management
Computer systems have become part of every aspect of our lives. As digital transformation continues to grow in the corporate environment and the number of devices connected to the network is on the rise, the issues associated with this topic are becoming increasingly complex.
For this reason, Panda Security has presented the latest version of Panda Systems Management: the most powerful, scalable and easy-to-use RMM administration tool on the market. Systems Management is capable of combating all inefficiencies in the IT environment, allowing businesses to save time and money.
The Problem
This new hyper-connected context means that new challenges may arise while trying to increase your company’s productivity. Some of the challenges that have added to the already complex IT environment include: the increasing and varied number of devices connected to the network, the growing number of remote users, and the need to fix problems with greater flexibility (anytime, anywhere).
The mixture of tools used everyday in the workplace provoke incidents and interrupt work. Consequently, as these inefficiencies multiply, they add to the IT department’s workload, and other important details that affect business management and security can be overlooked.
The Solution: Greater Automation and Maximum Performance
Systems Management remotely monitors and manages devices from the Cloud so that every IT department can offer a professional service with minimal impact on employee work.
What does the new version offer?
The new version of Systems Management gives you maximum performance ’out of the box’. To increase efficiency and grow business for our clients and partners, the Systems Management manager facilitates five pillars (asset inventory, device monitoring, remote device management, resolution tool support that is not intrusive, and generated reports) with the following functions:
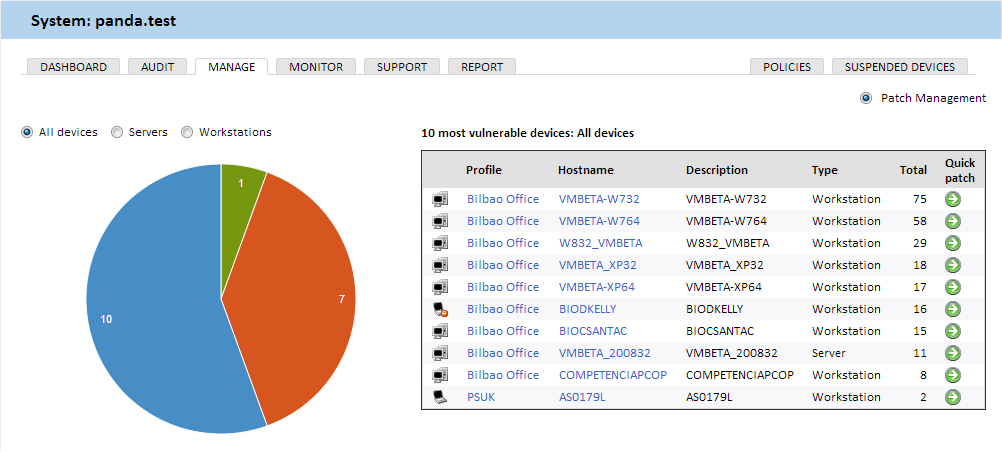
 Recommended monitoring policies based on the best practices of our clients.
Recommended monitoring policies based on the best practices of our clients.
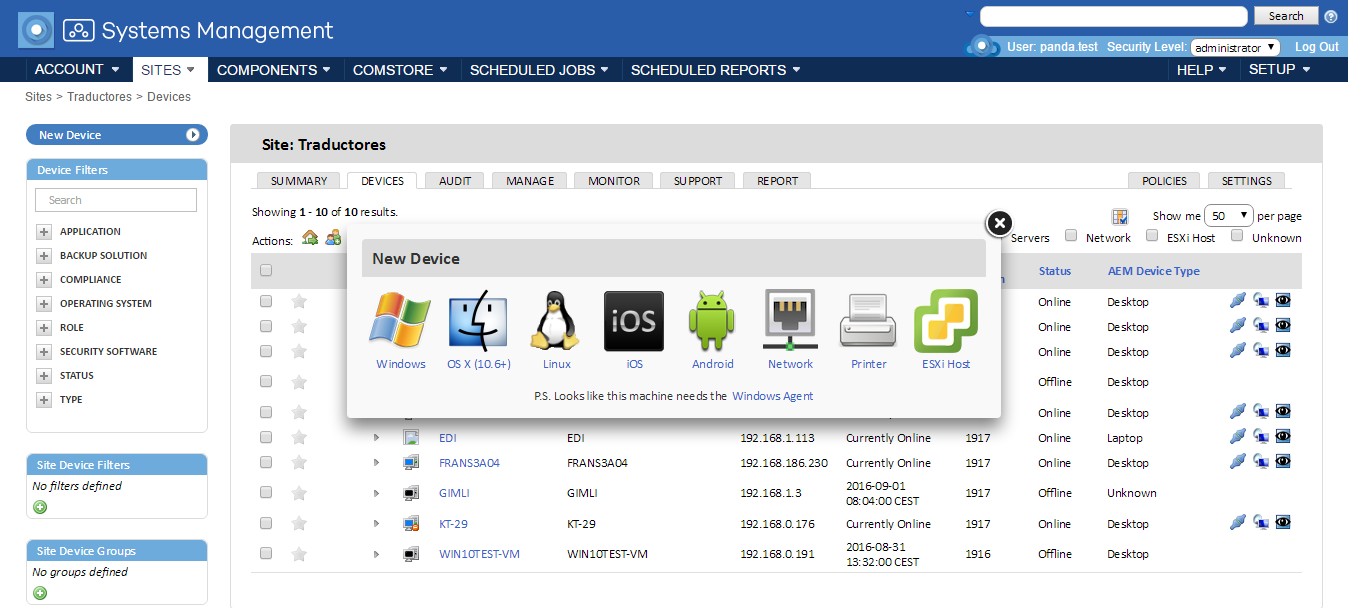
- New filters improve management systems: instant visualization of the IT Park so you can see what you need.
- New reports for server performance, CPU, memory, and disk performance for the last 30 days, including general averages.
- Integrates with Microsoft Hyper-V and the new hardware monitors added for VMware ESXi.
- New maintenance Windows- now alerts can be programmed and silenced.
The post Improved Efficiency and Centralized Management with the Latest Version of Panda Systems Management appeared first on Panda Security Mediacenter.