This is an additional EXTRABACON module for Cisco ASA version 9.2(3). This does not use the same shellcode as the Equation Group version, but accomplishes the same task of disabling the auth functions in less stages/bytes.
Monthly Archives: September 2016
Threatpost News Wrap, September 16, 2016
The news of the week is discussed, including Schneier’s DDoS article, a patched IE/Edge zero day, a new OS X malware detection method, and Google’s Project Zero prize.
MP3 Cutter 1.1.0 Registration Bypass
MP3 Cutter version 1.1.0 suffers from a registration bypass flaw.
Oktoberfest 2016: How to quickly connect to secure Wi-Fi in Munich
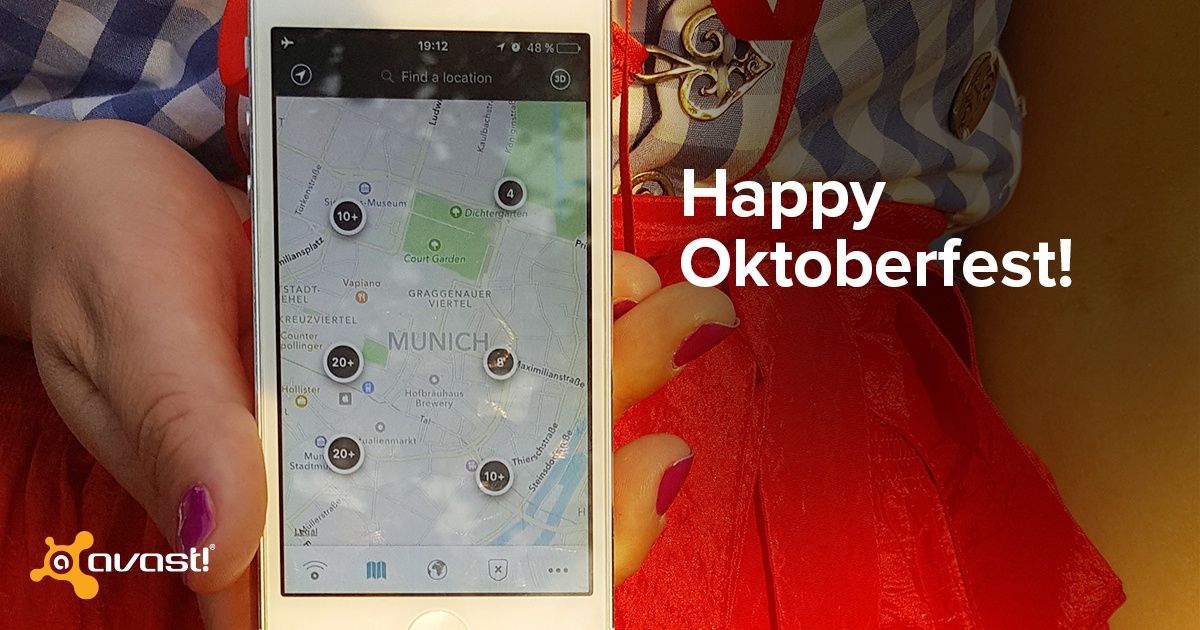
This Saturday, the 183rd Oktoberfest will take place on the Theresienwiese in Munich, Germany. People will travel to the Bavarian capital from all over the world to enjoy beer, music, chicken, cotton candy, amusement rides and more!
If you are traveling to Munich for Oktoberfest, you probably want to share your exciting beer hall photos and videos with friends and family to show off (as soon as possible) what an awesome time you are having! You may also need to access Google Maps to find your way around the city while sightseeing. Now, you’re probably asking yourself: How am I going to do this, unless I pay for an expensive international plan?
![]()
Beware of crafty WarCraft malware

This is a story that began 18 years ago. If you are a long time gamer like me, you know it well: Company starts developing a game, company decides the game is not up to standard, company decides to scrap game. But then something happens …
The post Beware of crafty WarCraft malware appeared first on Avira Blog.
Oktoberfest is oh so trending

It’s Oktoberfest time. Don’t let anyone put a restriction between you and that beer!
The post Oktoberfest is oh so trending appeared first on Avira Blog.
“Counter- intelligence as a change to the IT security strategyâ€, David Barroso

David Barroso is one of the key names in IT security in Spain and our guest article. We’ve known each other for years, as even though we haven’t had the chance to work together on joint projects, we have often met at security conferences over the last decade or so. That said, I’m going to let him introduce himself:
1- David, who are you? How have you got to where you are in IT security? How did you get into this crazy, fascinating world?
It all started when I began university in the 90’s. I left my home town of Palencia to study in Madrid, living on campus with more than 300 others. The IT and telco people had set up a network of coaxial cables across the floor (later we were able to wire up each room with RJ45) and we were responsible for managing the network. In fact, in the late 90’s, we were the first ADSL customers in Spain, so it was like running a company of 300 employees. This was the era of the beginning of Linux, Windows 95, with all the fun of using winnukes, land, back orifice, exploits for X-Windows with your colleagues, generally to play tricks on people. But we also had to configure the whole network back then, to share a miserly 256Kb ADSL connection among 300 students: IP masquerading, QoS, provide email for everyone, Web pages, Linux security, Windows, etc.
I learned a lot during this time because we did everything from scratch and everything was really manual, not to mention the continuous incidents affecting our ‘users’.

David Barroso, CEO of Countercraft
2- As an entrepreneur you have set up your own company, Countercraft. What are the main challenges and obstacles nowadays when setting up a cyber security startup?
I think there are several major challenges. The first, of course, is to create a product or service that customers want to buy, and that means finding a balance between the technical and business sides of the project. Tech people often fail to appreciate the marketing and sales aspects, but both are essential.
Another mistake we tend to make in Spain is that we don’t think about creating something international from the outset; we try to do something local. That’s so different from the Israeli or US outlook (today’s leaders in IT security) where they want to take on the world from the word ‘go’.
It is also makes a difference where you start up your company. We are grateful to have had support though it is nowhere near the support that companies get in the countries mentioned before. They are not only supported financially, but are also helped to position their company or product.
Tech people often fail to appreciate the marketing and sales aspects, but both are essential.
3- Tell us about a typical day in the life of David Barroso. What sort of challenges do you come up against in your day–to-day life?
The truth is that for obvious reasons, I’m working quite intensely at the moment, dedicating some 12-13 hours a day to our company, doing everything: programming (which I really enjoy), defining the product, analyzing the competition, discussing the market policy, talking with partners, visiting customers, administrating computers, changing print toner, buying laptops, sorting out invoices, etc. There’s no time to get bored.
We’re gradually beginning to outsource some tasks, especially after the round of financing, though there are still many, many things to do in a small company.
I’d say the main challenge is to try to get the whole band playing in tune in this early phase without creating problems further down the line.
4- Countercraft sets itself out as a counter-intelligence startup… Can you explain this concept and the focus of the company? What kinds of organizations need these solutions?
We are positioning ourselves as a change to the IT security strategy. Today, most companies tend to focus on setting up all possible security measures, then resolving security incidents as they occur.
What we propose is to use a lot of the techniques that our enemies are using, particularly as we need to be more proactive. Just as attackers deceive and lie, why not do the same thing (legally, of course)?
We use the classic concept of honeypots adapted to the present day, with many other techniques to make life as difficult as possible for attackers. The idea is to identify them as soon as possible, discover their tools and modus-operandi, as well as getting as much information about them as possible.
We are positioning ourselves as a change to the IT security strategy(…) Just as attackers deceive and lie, why not do the same thing ?
The types of companies that can adapt to this new strategy are those that have already done their security homework, i.e. mature companies from a security perspective, as it is not a good idea to use lures if you have security holes.
5- The world of IT security is advancing at an incredible pace, both in terms of technological developments as well as the sophistication and complexity of attacks. What new challenges will security companies have to face over the coming years?
An inherent problem is that human beings will always be the main entry point for security problems, and as such, technology and security products face an uphill task as we are so unpredictable. It’s also true that we don’t really like following security procedures and we are easily tricked. So even if we give most users highly secured desktops, attackers will (and already do) target system administrators, who generally have more freedom.
In our case, what we try to do is to find a human error or lapse on the part of the attackers (they also make mistakes), and give a tug on the loose thread to see if we get what we’re looking for. In other words, we also take advantage of the fact that attackers are human and make mistakes, maybe because of too much haste or greed, or a lack of knowledge.
6- The type of strategy employed by Countercraft is strongly focused on attacks that aim to penetrate corporate networks and steal sensitive data. Do you believe that these techniques could be used to counter other types of attacks?
Of course. In fact there are other scenarios in which we are using the same techniques, such as to counter fraud to identify and monitor malware and phishing campaigns, sabotage of governments or companies, or working with law enforcement agencies to tackle child pornography or online recruitment by terrorist groups.
7- Managing to hoodwink cyber-crooks offers you the chance to find out a lot about them, not just how they operate and the steps they take to infiltrate a company, but also data that could also help to identify the culprits. Do you anticipate, as part of your strategy, working with law enforcement agencies, or would this be a decision for each of the customers you protect?
From the outset we work with law enforcement agencies, although the decision to contact them regarding incidents in companies is entirely down to the customer.
The post “Counter- intelligence as a change to the IT security strategy”, David Barroso appeared first on Panda Security Mediacenter.
AnoBBS 1.0.1 Remote File Inclusion
AnoBBS version 1.0.1 suffers from a remote file inclusion vulnerability.
Using 'Signal' for Encrypted Chats? You Shouldn't Skip Its Next Update
Two Researchers have discovered several vulnerabilities in Signal, the popular end-to-end encrypted messaging app recommended by whistleblower Edward Snowden.
One of those vulnerabilities could allow potential attackers to add random data to the attachments of encrypted messages sent by Android users, while another bug could allow hackers to remotely execute malicious code on the targeted
![]()
BINOM3 Power Meter CSRF / XSS / Credential Management
BINOM3 power meter suffers from cross site request forgery, weak credential management, information leakage, and cross site scripting vulnerabilities.




