
We daily capture them on our phones. We have dozens of them stored on our computers. We share them on social networks and we love to see those of others. We are talking about the images in JPEG format, the most used one because when compressed the pictures don’t lose much quality. Indispensables, and yet, could be the tool used by a cybercriminal to access any corporate or institution network.
This was proven by security expert Marcus Murray, who researched a new way a cyber-attacker could exploit a malicious JPEG to compromise Windows servers and access any company’s sensitive information.
The researcher demonstrated how someone could performed this attack during the RSA Conference in San Francisco, an event that gathers dozens of experts in computer security every year. Murray implemented a ‘demo’ to compromise a similar security network to any US government agency network.
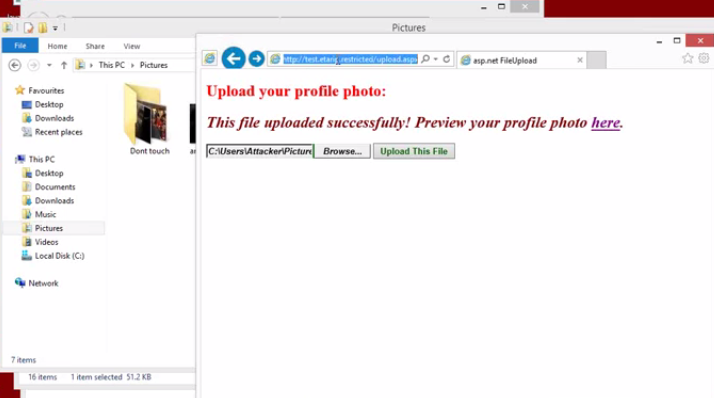
Murray changed the attributes or metadata that any JPEG file stores including in it a malicious code. Then he got this image to infect the corporate network. How did he do it? By a form that allowed users to upload a profile picture to the alleged government agency web page. Once inside, the file became a gateway for the attacker.
Thanks to the malicious JPEG, the cyber-criminal’s administration permissions over the network grew more and more, reaching a point at which he could steal sensitive information or even take control over the network.
The rest of the process is simpler: the criminal only has to exploit his advantage to install malicious software that infects the computers to spy the corporation or steal confidential information. According to Murray, this attack can be performed in “even mixed environments” with Windows and Linux.

On the conference in San Francisco, he showed how to introduce a remotely accessed Trojan he created using Metasploit, the popular open source project that allows trying different kinds of attacks as part of a ‘pentest’ (penetration test).
That’s how he prove that only with a picture you can access any company’s network and steal their confidential information, without the employees realizing the damage a file so seemingly harmless could make.
The post A JPEG may jeopardize your company’s network appeared first on MediaCenter Panda Security.