Get your small business up and running with free software.
Getting a new business off the ground is not an easy task and can be quite costly, but there are a lot of free software and services available online that your new or small business can use as an alternative to paid-for products.
Here is a list (in alphabetical order, so no favorites ![]() ) of some you will find useful:
) of some you will find useful:
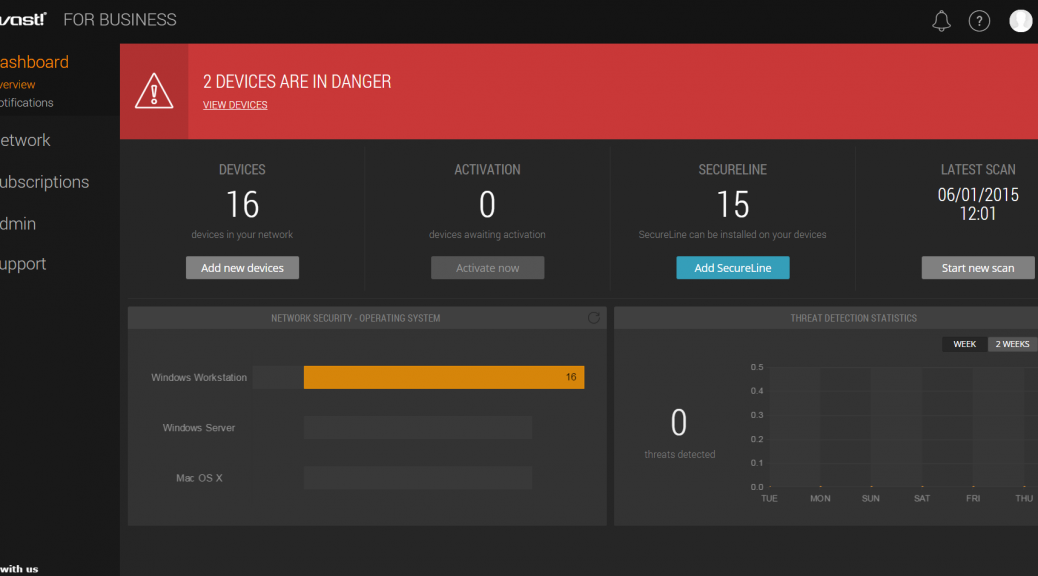
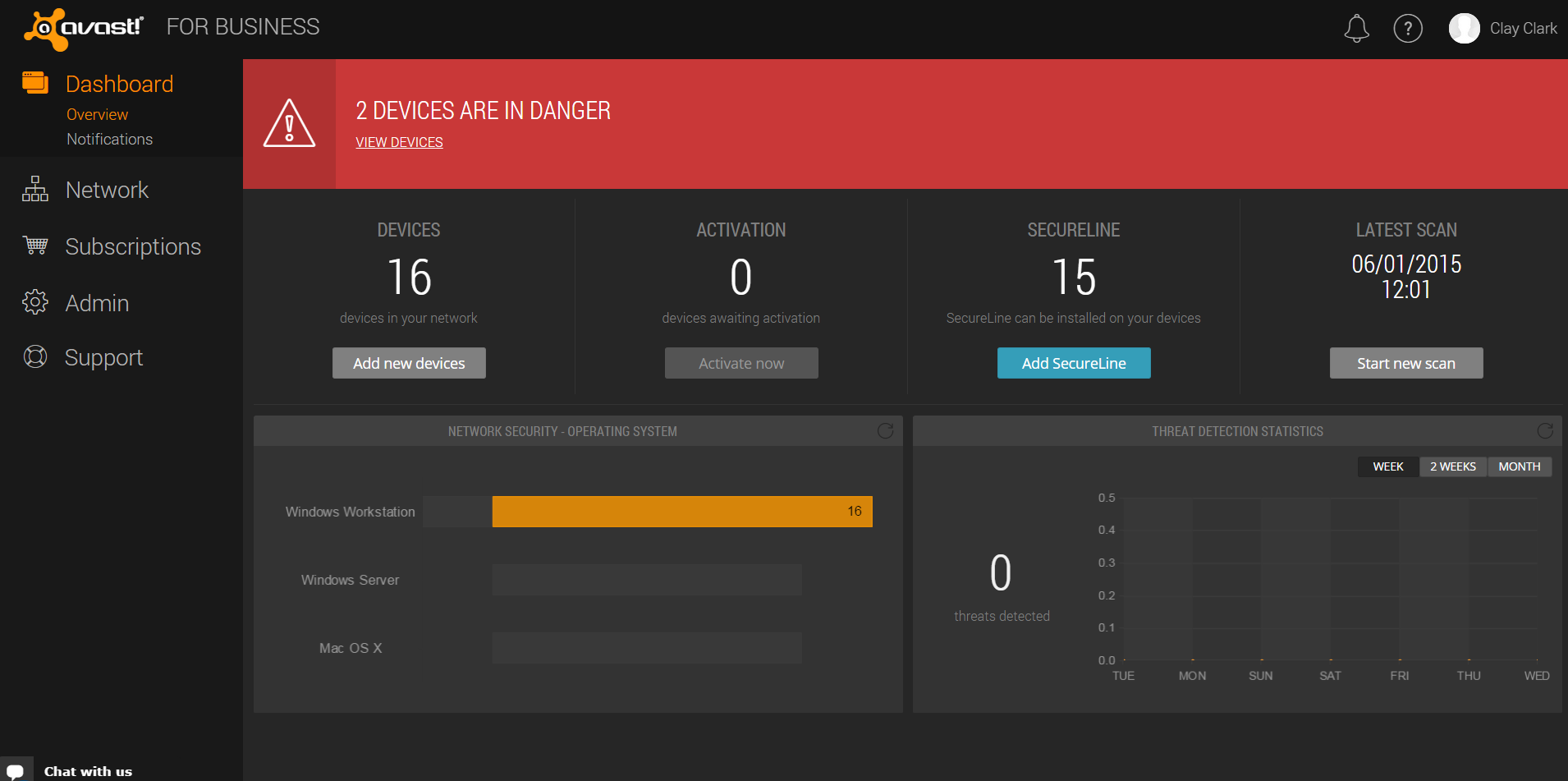
 Avast for Business – cloud-managed security
Avast for Business – cloud-managed security
Avast not only provides consumers with free security, but we also provide small and medium sized businesses with free cloud-managed protection. Avast for Business is easy to install and can be managed from anywhere and at anytime.
Facebook Page – alternative to building your own website
If you’re a restaurant owner or a small boutique you could also, either in addition to or instead of hosting your own website, create a Facebook page for your business. You won’t be able to sell items online, but you can add your business’ address and directions, opening hours, a description of your business and post images and status updates to inform your customers of new items on your menu or of new items available for sale in your store.
![]() Fundera – loans for your business
Fundera – loans for your business
Fundera is a free service that offers you loan options and lets you choose the one best suited for your small business. All you need to do is fill out a short questionnaire and then you are presented with loan products, lenders and rates and can apply to the lenders that fit you best with only one application.
Hootsuite – social media manager
Using social media is a great way to get the word out about your budding business, and a social media manager is, therefore, very helpful to keep track of your sites and their effectiveness. Hootsuite offers a free starter package where you can add three social media platforms, get basic analytics reports and schedule posts.
 Jimdo and Weebly – (subdomain) website hosting
Jimdo and Weebly – (subdomain) website hosting
Jimdo and Weebly are both web hosting services that offer free starter packages when you create a website using their subdomain. With Jimdo’s free package you get 500MB of storage space, one password-protected area and mobile versions of your site. Weebly offers unlimited pages and a drag and drop builder. Both services offer the possibility to sell up to five items for free in case you want to use your site for ecommerce. Checkout services are also included for free.
Ope nCart – shopping cart solution
nCart – shopping cart solution
OpenCart is a free and open source shopping cart solution. All you need to do is install OpenCart, select your theme, add your products and you are ready to start selling your products on your website!
Ope nOffice – office suite
nOffice – office suite
Apache OpenOffice is a great alternative to Microsoft’s Office Suite. OpenOffice is an open source office suite that includes essentials like a Word processor, spreadsheet, multimedia, graphics, database and math software. Best of all, OpenOffice is license-free and can be installed on as many computers as your business needs!
Orange HRM – human resource management software
Orange HRM is a free and open source software for human resource management. It is a full-featured HR management system offering various modules such as system administration, personnel information management, and recruitment.
Producteev – task manager
Producteev is a task manager that offers unlimited users, projects and tasks in its free version so you can ensure that you and your team stay on top of the most important to-dos to get your business up and running!
Suite CRM – customer relationship management
Suite CRM is free, open source software for customer relationship management. It’s based on Sugar CRM and comparable to Salesforce. It gives you a full overview, including products, quotes, contracts, projects, reporting, teams, workflow and much more.
![]() Wave – accounting tools
Wave – accounting tools
Wave offers cloud-based invoicing, accounting, payroll and payments for free for businesses with 9 people or less. They finance their services by connecting small business owners with vendors of products and services that offer discounts to Wave users.
Nearly all of the above mentioned products also offer premium services your business can take advantage of as it grows. For now, we wish your business the best of luck and hope this list of free software helps your business. ![]()
![]()

 We are very excited to announce the debut of a new series of videos called Avast Hack Chat. Every week we invite a security expert to talk us through the hacks on Mr. Robot, USA Network’s summertime hit TV show. We also talk about current news, technology in pop culture, and tips that you can use in your everyday life to keep your devices and data secure. Please subscribe to
We are very excited to announce the debut of a new series of videos called Avast Hack Chat. Every week we invite a security expert to talk us through the hacks on Mr. Robot, USA Network’s summertime hit TV show. We also talk about current news, technology in pop culture, and tips that you can use in your everyday life to keep your devices and data secure. Please subscribe to 



 BYOD, or bring your own device, is a common practice at many businesses around the world. CEO Vince Steckler announced the acquisition of
BYOD, or bring your own device, is a common practice at many businesses around the world. CEO Vince Steckler announced the acquisition of  Students wanting to know how they did on their AP test installed
Students wanting to know how they did on their AP test installed