Apple’s Worldwide Developers Conference kicked off June 8 at San Francisco’s Moscone West.
Earlier this month, I was lucky enough to attend Apple’s Worldwide Developers Conference (WWDC) in San Francisco, where mobile developers from far and wide came together to learn about the future of iOS and OS X systems. Along with being the first time I was able to participate in this sought-after conference, it was also my first time visiting San Francisco.
Once you get past its glitz and the glamour, the majority of the event revolves around waiting in a series of queues — the day before the actual event began, the line for the event’s keynote lectures had formed around an entire city block. Although I wasn’t one of the first people to camp out there, I did arrive around 5:30 a.m. on Monday to stake out my spot. While the masses of people at WWDC can be a bit overwhelming, there really isn’t a better place to meet thousands of like-minded developers with whom one can strike up an interesting conversation discussing the ins and outs of of iOS development.
This year, Apple hosted 5,000 developers from 70 different countries, the vast majority of whom were present at WWDC for the first time. The WWDC Scholarship Program awarded 350 scholarships to recipients, the youngest of whom was Kiera Cawley, a 12-year-old app developer who has been coding since the age of nine. Apple CEO Tim Cook made a guest appearance at the conference’s special orientation session, mingling with the recipients and even taking selfies with some of them.

WWDC 2015
OS X EL CAPITAN — what a name! At first, I thought it had to be another joke from Craig Federighi, but I was wrong. A noteworthy new feature in El Capitan is the split view mode, which allows us to work on two apps simultaneously. Apple claims that there has been a 1.4x time increase in app launch times and 2x improvement in app switching speeds. In general, Apple has been quite busy and has made huge improvements for developers. The most exciting news is that Apple will be making Swift open source later this year — a big step forward for the developer community.
The recent release of iOS 9 makes the entire system smarter and more secure. Now, users can run two apps at once on an iPad, side by side in split view (the same feature present in OS X). This will be challenging for developers who still don’t prefer Auto Layout. For the rest of us, though, it works quite well. It’s also possible to make activities and documents within your app searchable using Spotlight or to include special links on your site that launch your app at a specific view. And yes, it’s still necessary to support iPhone 4s on iOS 9. However, it should be more optimized now more than ever before.
Jennifer Bailey announced release of Apple Pay in the UK next month. This was a bad piece of news for the developer sitting right next to me. He was working as a freelancer for a company that provides mobile payments in the UK via iOS. “My company is screwed and I should start looking for a new job,” he said in response to Bailey’s announcement. Apple Pay’s imminent launch is, unfortunately, not the best update for people whose jobs revolve around mobile payments.
During the rest of the week, Apple featured 100 sessions and labs, and over 1000 Apple engineers were present and ready to give me advice. UI Design Lab was the most popular workshop at the conference, and you could count on the fact that there’d be a huge line every day. After trying to get into the session every morning, I was finally able to make an appointment on Friday. In the end, it was worth the wait. ![]()
All in all, WWDC was a great opportunity to meet an impressive collection of talented developers and to discuss the vast amount of progress Apple has been making within the mobile sphere. See you next year, Apple!
![]()



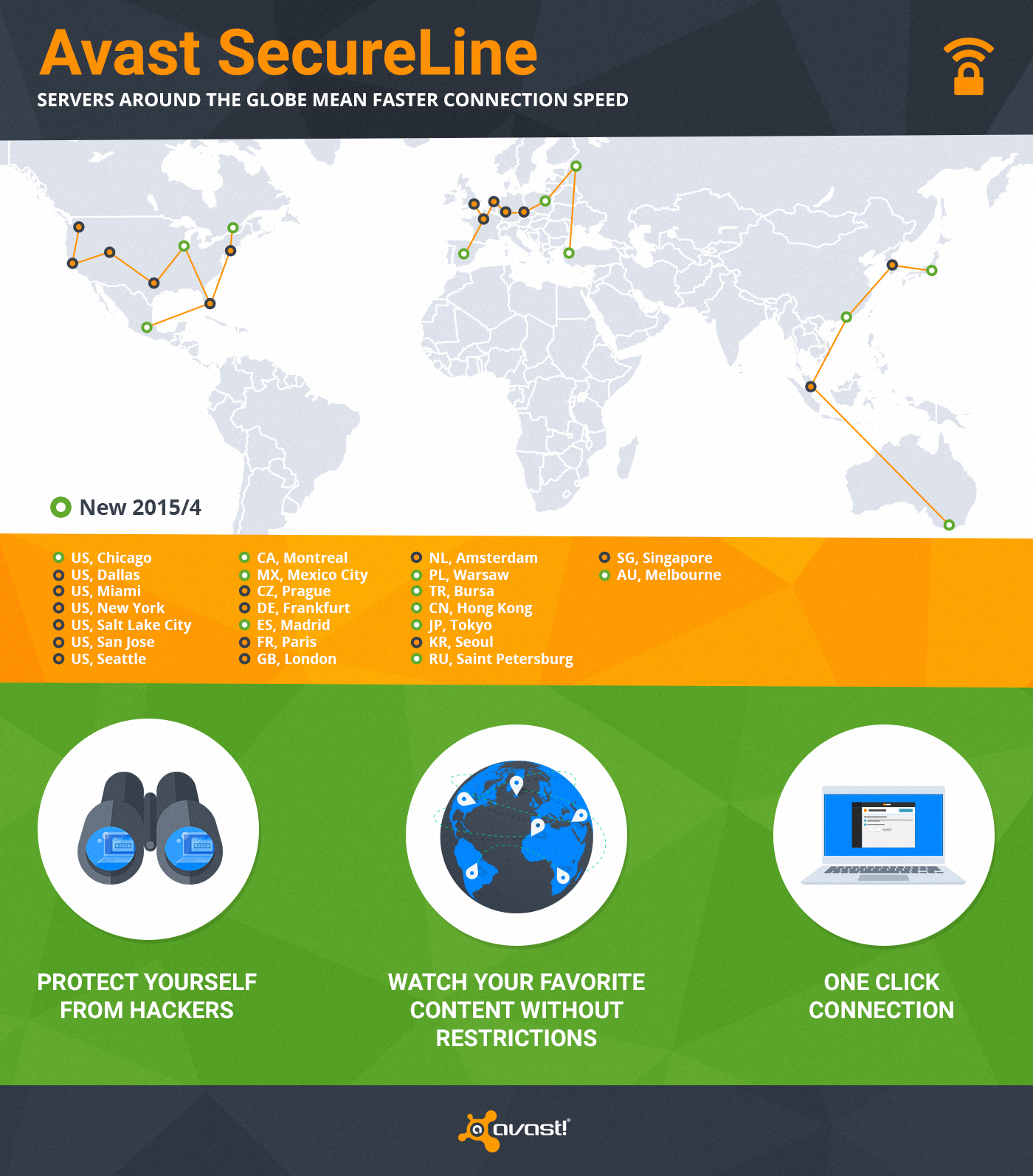

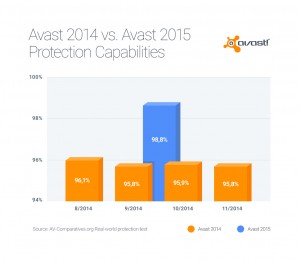 Avast customers who are using older versions of our Avast antivirus products cannot upgrade to Windows 10, but more importantly they will no longer receive product upgrades or enhancements. We recommend that everyone upgrade to the latest version to benefit from better detection rates and new features. Read
Avast customers who are using older versions of our Avast antivirus products cannot upgrade to Windows 10, but more importantly they will no longer receive product upgrades or enhancements. We recommend that everyone upgrade to the latest version to benefit from better detection rates and new features. Read  The new Android powered tablets by ASUS come preloaded with Avast Mobile Security, so you are protected right out of the box. Read
The new Android powered tablets by ASUS come preloaded with Avast Mobile Security, so you are protected right out of the box. Read  Want a career with Avast? A new Avast Software office has opened in Charlotte, North Carolina to bring the new free Avast for Business to the U.S. market and beyond. Read
Want a career with Avast? A new Avast Software office has opened in Charlotte, North Carolina to bring the new free Avast for Business to the U.S. market and beyond. Read