Kaspersky Lab today announced a two-year partnership with the World Chess Federation (FIDE) and World Chess.
Category Archives: Antivirus Vendors
Antivirus Vendors
Borders matter when it comes to malware
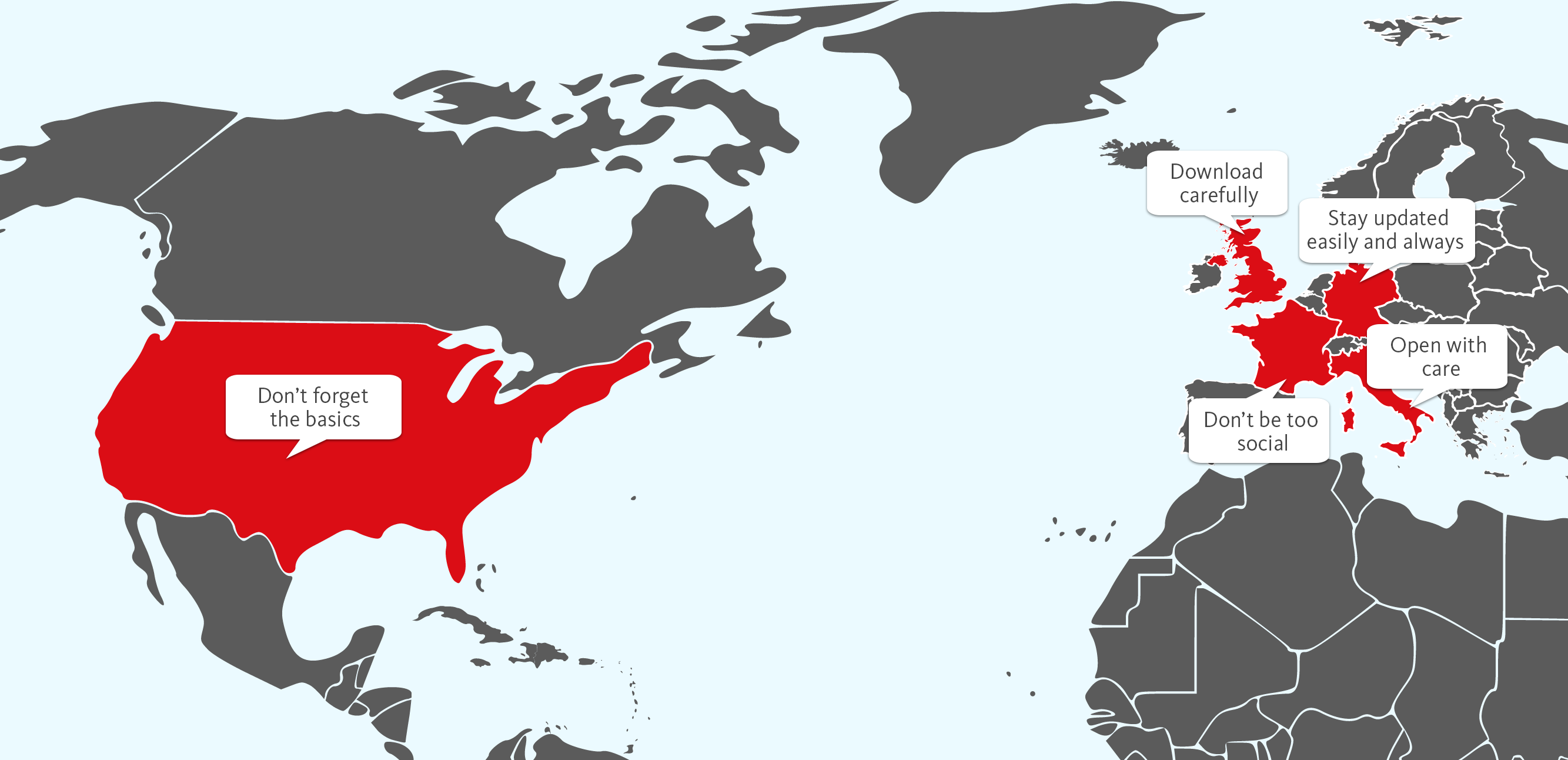
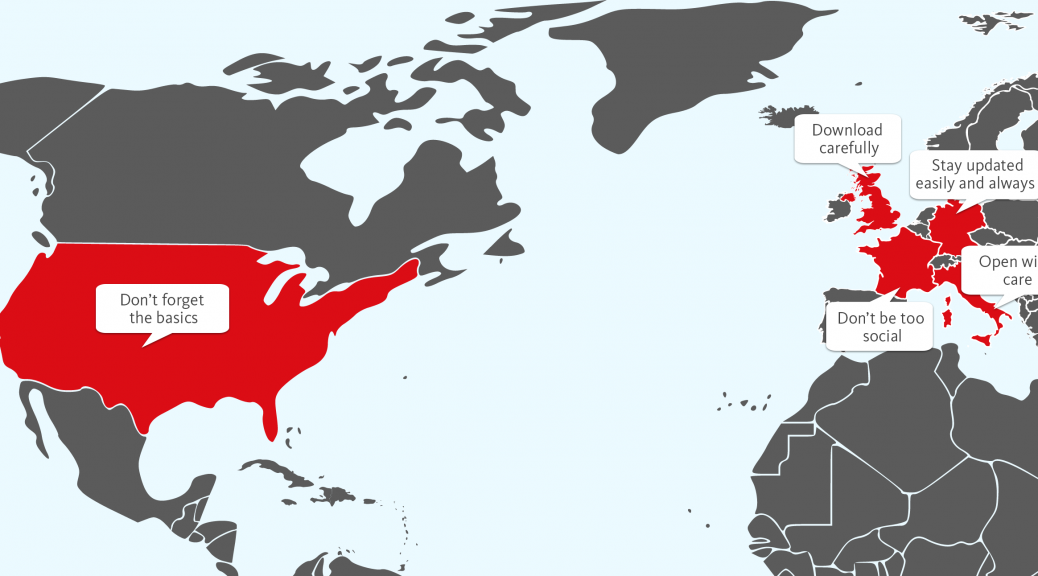
Despite open borders, regional variations persist when it comes to malware distribution – and demonstrating good security habits. Take a five-country boost to your security on Safer Internet Day. Is the distribution of malware influenced by borders? Geography plays a continuing role in determining what types of malware people are exposed to but these country […]
The post Borders matter when it comes to malware appeared first on Avira Blog.
Keychain, Apple’s Cloud-Based Tool That Safeguards Your Data
Safeguarding your company’s confidential information, in many cases, calls for having your employees create and properly manage a series of passwords. Not only should they choose complex credentials, but they should also vary among themselves. And they definitely should not be saved in easily accessible places, like a text document.
Password managers come in handy in this task that is so indispensable to corporate security. For their part, companies that have Apple devices for their employees have the Keychain as an ally: it is a password manager in the cloud that makes things really easy when defending corporate privacy via robust password selection.
Activating this tool is simple: just go to iCloud Settings from an iPhone or an iPad and activate the Keychain option. From a Mac you go to the “System Preferences” menu.
Once activated, all the passwords used by the employee will be stored in iCloud, with its own encryption. Once uploaded to the cloud, it will be possible to use those credentials on all devices that are synchronized and authorized to do so.
However, the Apple Keychain is much more than just a place to store passwords in the cloud. In fact, it allows users to completely forget about the clutter of having several passwords since, when they sign up for the service, the keychain suggests complex and distinct options to those already used and automatically saves it. No need to commit anything to memory.
It is also possible to store credit card data and certificates to sign documents digitally. Thus, Apple encryption and its cloud service are one hundred percent responsible for security on the platforms used by employees.
By combining this tool with the right protection to avoid threats, your company’s confidential information will be safer. It makes sure that your passwords are secure and that they will not be stored remotely in any place. And those who want to spice up their passwords can still edit them (or delete old ones) to make them even more complex. When corporate security is at stake, it can never hurt to add extra layers of protection.
The post Keychain, Apple’s Cloud-Based Tool That Safeguards Your Data appeared first on Panda Security Mediacenter.
Avast sponsors Virtual GP motorsports team
Avast is proud to sponsor our first virtual Formula One team with rookie driver Petr Zoubek in season 3 of the Thrustmaster Virtual GP. Virtual racing competitions are new to the world of eGaming, and Virtual GP is pioneering a unique platform using modern technologies to combine the best of real motorsport with the virtual one.
![]()
Kaspersky Lab’s Targeted Attacks Detection Solution is Now Certified by ICSA Labs
Kaspersky Lab’s Kaspersky Anti Targeted Attack (KATA) Platform has successfully passed independent testing by ICSA Labs, in a test rarely performed, which focuses on the efficiency of specialized solutions to protect businesses from advanced and targeted threats.
Android and Linux, the Technologies with the Most Security Holes in 2016
The latest version of Google’s mobile operating system, Android Nougat, has quite a few security improvements over older versions and, in fact, its arrival on the market is more than necessary. Not for nothing, Android has managed to win the dubious honor of being the product with the most security vulnerabilities discovered in 2016.
According to the ranking carried out by the CVE Details digital platform, more than five hundred holes in Google’s mobile operating system over the past year have been found. To be exact, there were 523 security errors that put its more than 1.5 billion users at risk.
So Android has overtaken Apple. In 2015, the operating system of Apple computers, Mac OS X, had the greatest amount of vulnerabilities to their credit. However, this year Cupertino seems to have done their homework. They’ve gone from leading last year’s ranking with more than 400 vulnerabilities to closing out 2016 at number eleven on the list, with little more than 200 holes identified throughout the year.
So it turns out having a mobile fleet in your company comprised of Android phones can pose a real risk if you don’t have the right protection. In addition, it is important to update the terminal with the latest version possible, which ultimately will depend on the manufacturer (some are quicker than others, and all are abandoning their older models completely). It’s no wonder there are more than 300 million Android devices that no longer even receive security patches.
Two Linux distributers, Debian and Ubuntu, are the technological products that join Android on the podium of the most error-riddled software. Throughout 2016 over 300 vulnerabilities were found in Debian, while the other distributer came in third place with almost 280 errors.
Choosing your company’s technological tools can be key to preserving both your safety and that of your customers. However, not many are able to escape vulnerabilities: operating systems like Windows 10, browsers such as Google Chrome, or software giants like Adobe are also among the twenty products with the most vulnerabilities discovered in 2016.
The post Android and Linux, the Technologies with the Most Security Holes in 2016 appeared first on Panda Security Mediacenter.
Video: How to recover your Avira license key
![]()
The post Video: How to recover your Avira license key appeared first on Avira Blog.
Strategic cybersecurity will stymie ‘expanding threat landscape’
Strategic cybersecurity the key to keeping the threat of cyberattacks at bay, a new report states.
The post Strategic cybersecurity will stymie ‘expanding threat landscape’ appeared first on WeLiveSecurity
![]()
When Ransomware Comes Knocking at Your Door… or Locks it
A lot of things can go wrong on your holidays, like losing luggage or missing a flight, forgetting your travel documents or getting sick at the worst possible time. But have you ever been locked out of your hotel room because of a cyberattack?
That’s just what happened to guests at a luxury hotel in Austria when they were left stranded outside of their rooms after a ransomware attack that overrode electronic key systems.
This concept, which can be summed up as “if you don’t pay, your guests won’t be able to get into their rooms”, underscores a strategy shift in ransomware. Instead of directly attacking the hotel chain directly, cybercriminals are looking to increase profitability by compromising the well-being of paying customers.
The Evolution of Cyberattacks against Hotels
Infected computers and POS systems, credit card theft, access to confidential information… in the age of the Internet of Things and smart homes, these attacks are becoming commonplace or even antiquated.
Clearly the attacks that this industry has been experiencing are not something casual or fleeting. Behind them lies a real economic interest and a preoccupation with stealthy operations. The hotel sector has become a major target for organized cybercriminals in possession of malware specifically designed to harm its running smoothly, not only in payment systems, but also by sealing off access to your room, turning lights on and off, or locking your blinds.
This is, undoubtedly, a worrisome situation that could cause significant harm not only on an economic level, but also a PR level, sowing fear among clientele.
Taking appropriate measures is a matter of necessity. Hotels are being forced to reinforce the security of their networks, devices, and systems to avoid becoming victims to this kind of attack. But not all protection systems offer the same level of security, nor are they all valid for any kind of business environment.
Traditional antiviruses are not effective against these attacks, since they are specifically tailored to the victim and are cleaned of all recognizable malware signatures before being launched. Current anti-malware solutions use proactive technology that rely on these signatures to catch malware, rendering them useless against attacks that actively avoid incorporating traits recognizable to these solutions. That’s why it is vital to have advanced cybersecurity protection like Adaptive Defense 360, one that can activate protection systems before the malware is even able to run.
The post When Ransomware Comes Knocking at Your Door… or Locks it appeared first on Panda Security Mediacenter.
Video: Password Manager: Makes your digital life easier
![]()
The post Video: Password Manager: Makes your digital life easier appeared first on Avira Blog.