What is ransomware?
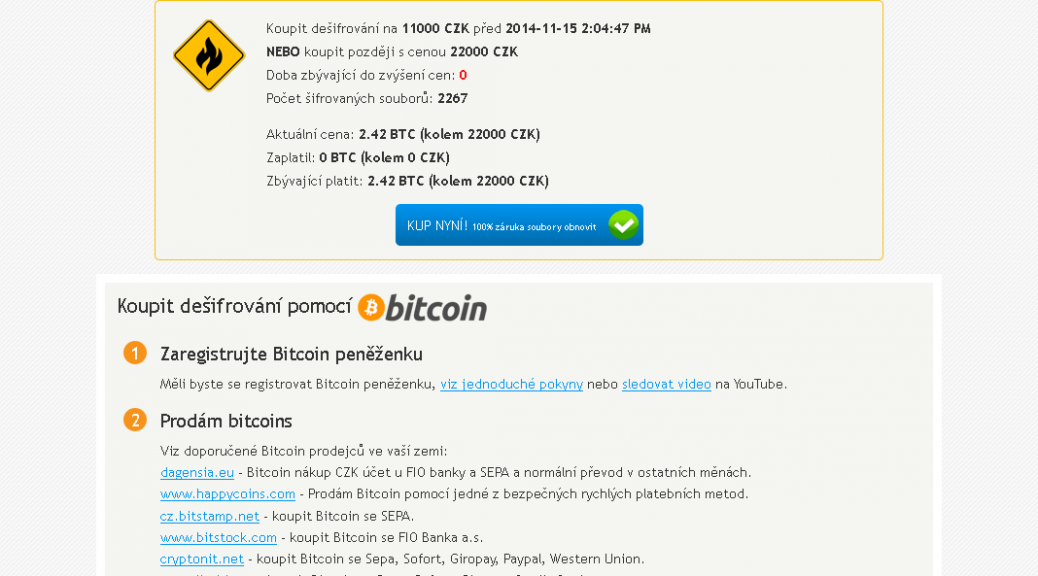
As we witnessed with CryptoLocker earlier this year, ransomware is a type of malware which encrypts certain files on your system and then extorts a ransom to unlock them.
Which files are affected?
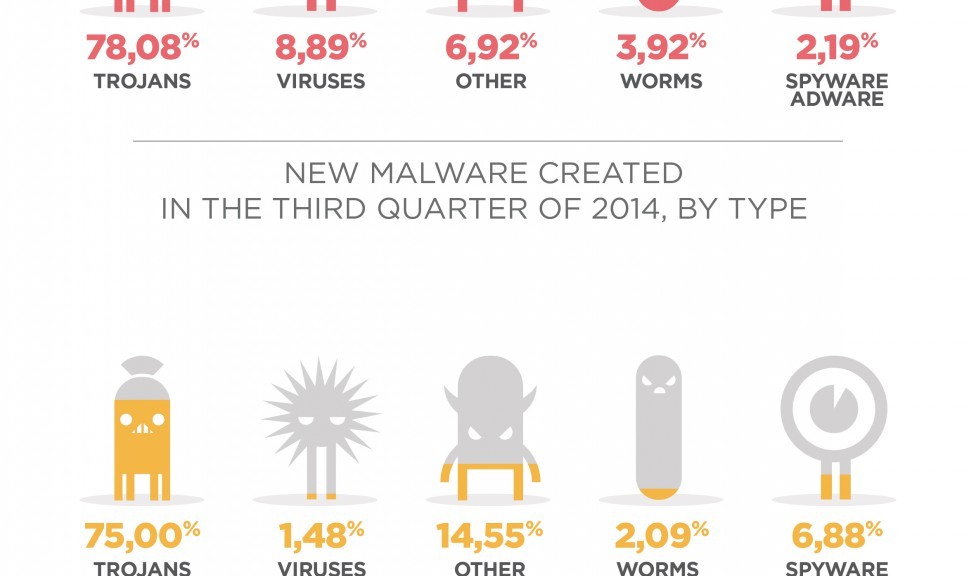
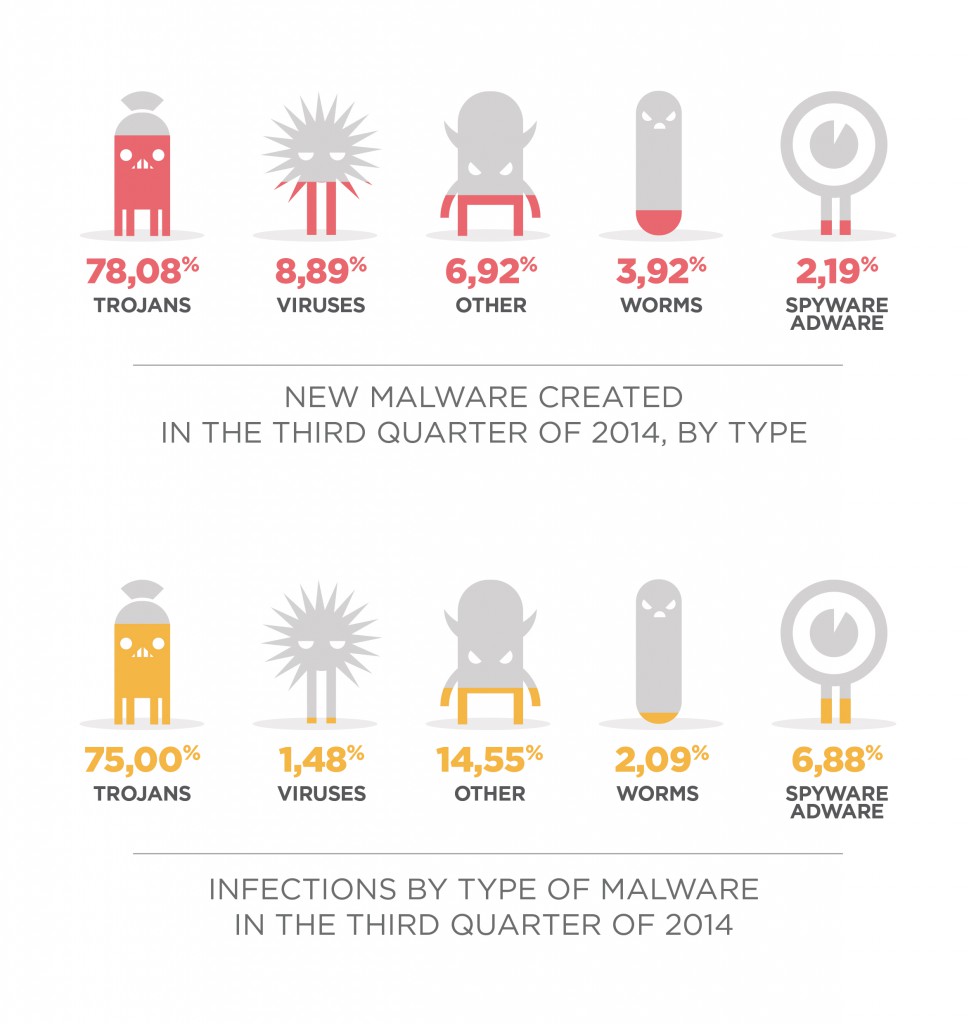
Most ransomware does not target important system files but instead looks for user files to encrypt. These can be everything from JPG images to office documents and emails, anything personal that could be a value to the user.
What is new about this variant?
Previous ransomware variants had weak or flawed encryption, which meant that files often could be recovered. This new variant contains a much stronger algorithm and encrypted files are almost impossible to recover without the encryption key, which is only held by the attacker. Interestingly the ransom can be paid in cryptocurrency as well as Czech Koruna.
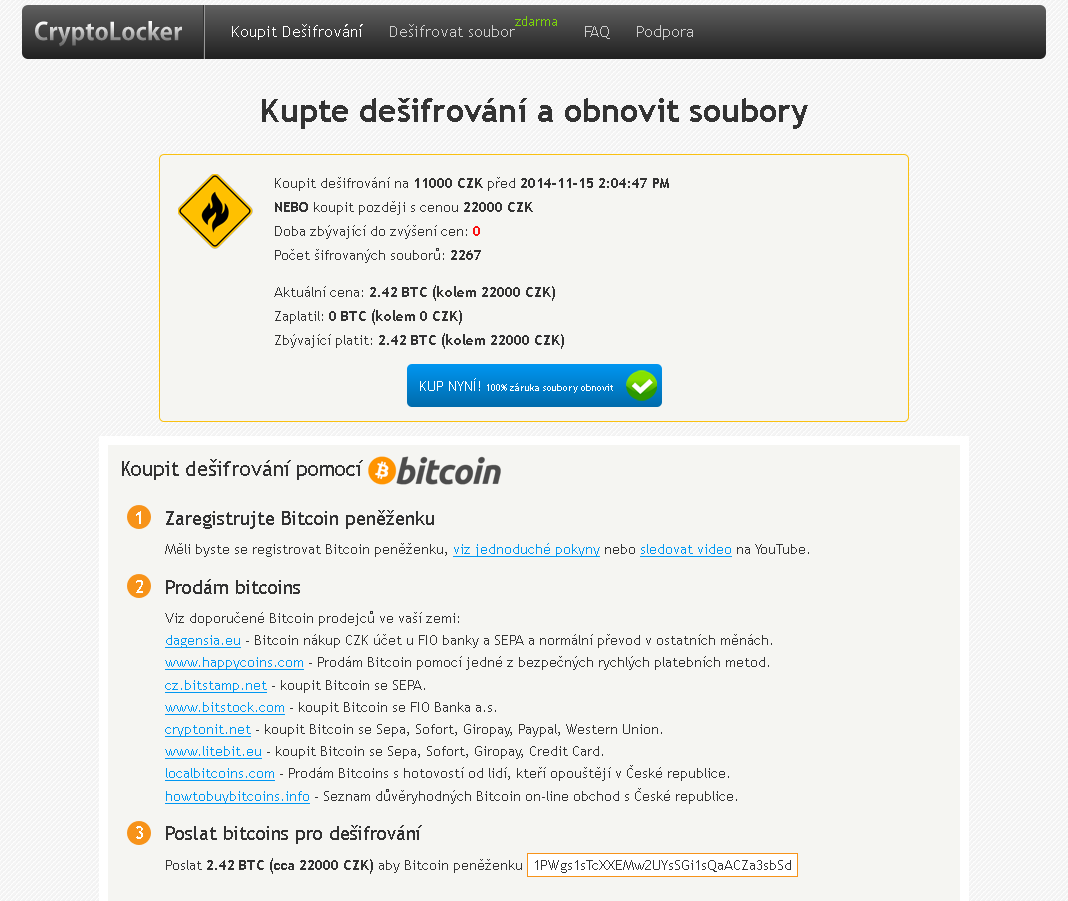
Is there any way to recover my files without paying the ransom?
Historically, it has been possible to restore files using Shadow Copy, a tool that allows users to backup parts of their system even while they are in use. Sadly most new ransomware variants are resistant to recovery with Shadow Copy. Always seek advice before taking any drastic action to recover data encrypted by ransomware.
How can you stay protected?
- Always backup -remember that malware has ability to encrypt files on all disks connected to your computer (including external USB disks, etc.) so be careful of leaving your backup connected to your machine or plugging in a backup to an infected device.
- Think before you click – If you are unsure whether a link or file is untrustworthy, it is always safer to ignore it and delete it. Never download a file or follow a link from an untrustworthy source.
- Get protection – As new variants emerge, they are continuously added to the database of definitions maintained by security companies like AVG. Up-to-date virus definitions are your front line protection against malware.
- Get some Identity Protection tools – Security software like AVG has specially designed tools to protect your personal data from fraudsters and malware.
Story from Tomas Prochazka
![]()
![]()