With over double the attendance of San Diego’s Comic-Con (340,000 attendees last year, compared to Comic-Con’s 130,000), gamescom highlights not just how pervasive video games have become in our lives, but also how video games have gone since the late 1970s and early 1980s from being a small offshoot of the “traditional” computing industry to becoming a full-fledged multi-billion dollar industry in themselves. Today, companies like Microsoft, Nintendo and SONY generate billions of dollars from sales of games and gaming consoles; and there is a burgeoning market for dedicated gaming hardware for PCs ranging from specialized graphics processors from companies like AMD (formerly ATI) and Nvidia to exotic cooling solutions using liquid nitrogen and metalized thermal interface materials; to the creation of AAA games such as Electronic Arts‘ fifteen year old (and still going strong) The Sims franchise, and Blizzard‘s World of Warcraft, which redefined MMORPG gaming.
Gaming by the numbers
To get an idea of just how pervasive computer gaming is, let’s look at these successful games and consoles, and match them up with some other real-world numbers:
|
ITEM
|
NUMBER
|
EQUIVALENT TO
|
|---|---|---|
| The Sims | 175 000 000 (copies sold over 15 years) |
Combined population of Austria, Belgium, Denmark, Germany, Liechtenstein, Luxembourg, Netherlands, Poland, Slovakia and Switzerland |
| World of Warcraft | 7 600 000 (avg. # players over last 4 quarters) |
Cost of 2014 upgrades (in USD) to Kensington Palace, United Kingdom |
| 8th generation console units | 18 680 000 (PS4+Wii+XBONE units shipped/sold) |
Average number of viewers per episode of Big Bang Theory during its 2012-2013 season |
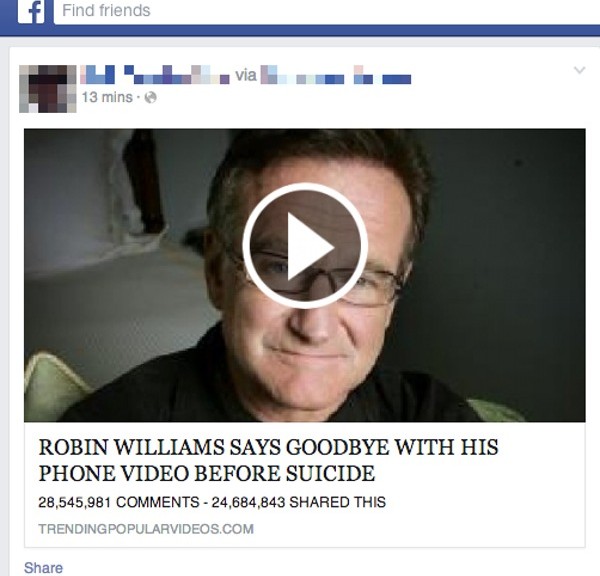
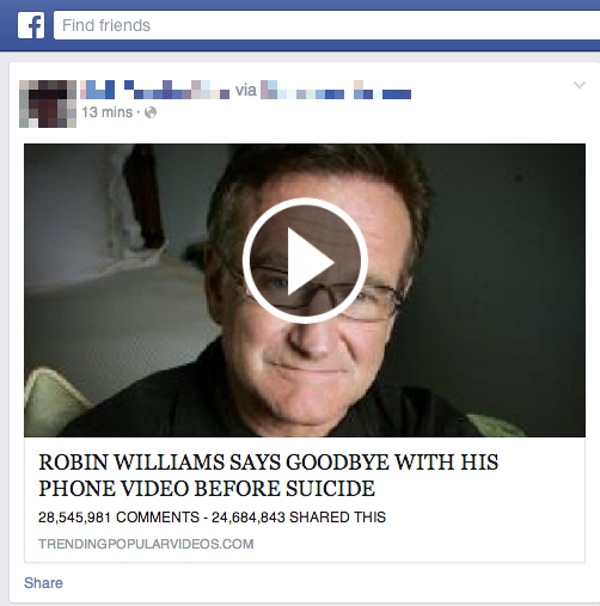
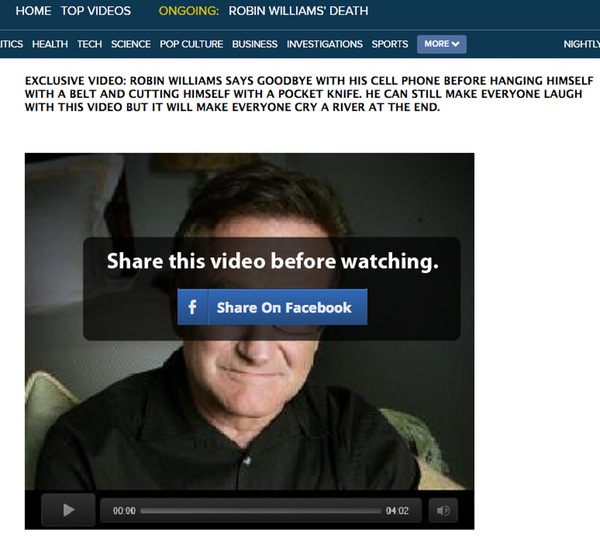
Computer gaming is a huge and a wildly successful market, and as in any system that works at scale, there are going to be so-called businessmen or entrepreneurs who “seek to optimize their return on investment through whatever means possible” or, to put it more succinctly, criminals who abuse the ecosystem. Â But in virtual worlds, can real crimes occur?
Game Crime
As it actually turns out, there’s actually quite a bit of undesirable activity that can occur online, such as trolling or griefing, which have occurred for as long as people have been playing games online. Â The exact nature of these activities varies between games, as do their consequences, but while some online behavior is horrifying, it is not always clear whether an actual crime, prosecutable outside of cyberspace, has occurred and, if so, in what jurisdictions. Â Likewise, cheating, while unsportsmanlike, may be a violation of a game’s acceptable-use policy, but not a criminal offense.
Doing time, online
Computer game companies police their virtual worlds to various degrees, as unwanted or objectionable in-game behavior could cause paying customers to leave en masse, with a corresponding drop in revenue. Â If warnings are not sufficient, the usual sentence for abusive users is to ban them from playing the game for a fixed amount of time. Â Repeat offenders, or those who may have done something especially offensive, may find themselves permanently banned from the game and their accounts closed.
Real thieves in a virtual world
The sale of virtual goods (including virtual currencies) is an important part of in-game economies, but also presents criminals with some unique opportunities as well:
Theft of Goods
The longer you play a MMORPG, the more likely you are to get items which are rare, limited edition, unique or otherwise contain powerful buffs for your character. Â Game companies create these kinds of items and adjust their scarcity because it helps encourage gamers to pay real money, either for the items themselves, or for in-game currency. Â Or the developer may charge a subscription fee to play the game. Â And that use of real money is what makes some games lucrative targets for thieves.
In some games’ player-versus-player (PvP) combat, the losers of fights may drop items that they were using in their inventory or currency, upon their in-game death. Â In some games, this has led to the creation of gangs or “mafias” who often target new players, either to “loot their corpses” or merely to threaten them with looting in order to obtain their items or currency.
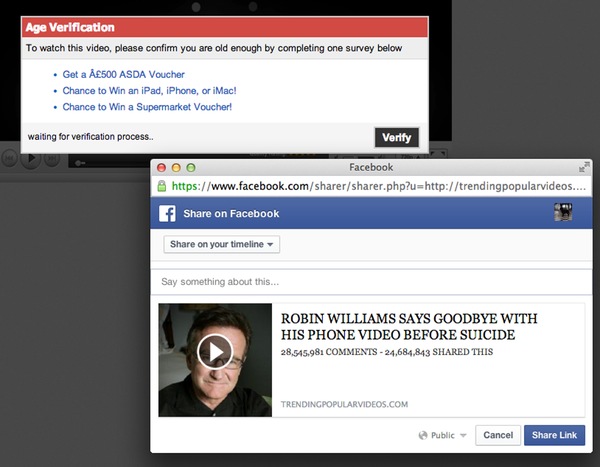
In the real world, gamers are regularly targeted by criminal gangs with phishing emails, as well as password stealing software, in order to gain access to their account credentials. Â From there, it is a simple matter for the criminals to empty out the gamer’s account, akin to taking the jewels out of some kind of high-tech safe deposit box.
While some game companies employ sophisticated geolocation tracking and even two-factor authentication systems identical to those employed by banks, others do not, and this makes those game accounts not only vulnerable to being emptied out, but to being stolen themselves. Â It can take years of grinding away at some games to reach the upper levels. Â For some unsporting game players, that represents an almost irresistible target.
Counterfeiting items
The amount of virtual items (including virtual currencies) is usually carefully calculated by gaming companies, even to the point of employing economists, to help ensure the stability of their virtual economy. Â Unfortunately, as in the real world, some virtual worlds are subject to counterfeiting, where in-game items or currency is duped (“duplicated”) over and over again by criminal gangs by exploiting vulnerabilities or bugs in the game, network connection or timing issues, and so forth.
If an in-game item can be duped ad nauseam, it can generate a lot of money, especially if it is the in-game currency that is being copied, and not some scarce or unique item. Â While item duping may not be enough to disrupt the in-game economy if the item is not being sold, it does disrupt game play and fairness when characters become seriously overbalanced.
Regardless of why it is being done, counterfeiting can be difficult to deal with, especially if the recipient of a duped item is not aware of its provenance. Â This may not stop game admins from removing counterfeit items or currency from a gamer’s account, or even banning the gamer, though.
Gold farming
Although in-game currency is not always golden coins, gold farming is the generic term used to describe players who do nothing but play a game in order to generate in-game currency, which they sell online for real-world currency. Â This is particularly problematic in China, where there have been reports that prisoners are used as slave labor to generate revenue for prison authorities.
As with item duping, gold farming is disruptive to gaming economies because it leads to inflation. Â Aside from that, it also leads to other problems, both in-game and in the real world, with being spammed with advertisements for gold. Â And, as with selling counterfeit or stolen goods, one runs the risk of having the items removed by the game admins or even being banned for having received counterfeit or stolen virtual property.
Companies under assault
Of course, computer criminals don’t just target gamers: Â Gaming companies themselves can be targeted as well. Â Probably the most well-known example of this is the April 2011 breach of the SONY PlayStation Network gaming and Qriocity music streaming service, which resulted in the compromise of the names, addresses and credit card details of 77 million user accounts.
ESET provided extensive coverage of the SONY data breach in our blog, starting from the initial report of the breach in April 2011 all the way up to the proposed settlement of a week ago.  As a result, I am not going to discuss the details of the SONY breach in this article.  Readers should be aware that this sort of problem is not unique to SONY, either.  Almost exactly, two years ago, Blizzard Entertainment suffered a data breach themselves, although they responded in a different and—this author thinks—more responsible fashion.
The point here is that that computer game companies and their associated services face real threats from criminals: Â If they charge customers for online play, the purchase of in-game items, or otherwise contain customer billing data in their computers, then those computers systems are targets for financial crime. Â But even if they don’t charge customers, their systems might still be targeted by criminals seeking access to accounts for the reasons mentioned in the preceding section. Â Game companies recognize this, of course, and as a result their security practices have improved greatly over the past couple of years.
Final thoughts
For the most part, computer gaming poses no additional risks beyond any other activities you might perform on the Internet. Â You may, however, wish to take a few extra precautions, as outlined in the previous two articles from We Live Security:
I would also suggest reading our Comic-Con 2014: Eight super-powered digital safety tips article. Â While Comic-Con is not exactly the same type of conference as gamescom, going to any type of conference with your computer, tablet, smartphone and various digital devices poses similar risks these days, and you may find some helpful information in that article.
Thanks to my colleagues Bruce P. Burrell, David Harley and Righard Zwienenberg for their assistance with this article.
Aryeh Goretsky, MVP, ZCSE
Distinguished Researcher, ESET
Selected Bibliography
For further reading, here is a fairly complete compendium of gaming-related articles from We Live Security:
- Windows XP Doomed – hackers play classic shooter on ATM (2014-07-29)
- SONY hacked: Victims to get $15M in ‘quality’ games – some day (2014-07-28)
- World of Warcraft account hacked – should thieves face jail? (2014-07-24)
- Gaming giant Ubisoft falls victim to breach – user emails and passwords at risk (2014-07-03)
- World Cup Phishing Scam hits FIFA 14 players through Instagram, Twitter (2014-06-20)
- Watch Dogs: How realistic is PS4 city-hack thriller? (2014-05-28)
- Watch Dogs pirates hit by scurvy Bitcoin-mining malware (2014-05-27)
- Activision Blizzard attacks hidden market in game “cheats” (2014-05-23)
- The future of security: Microsoft rewards 5-year-old who found critical password flaw (2014-04-05)
- Gamers warned after hi-tech malware leapfrogs World of Warcraft’s security with fake website(2014-01-06)
- Pat Garratt: PC games will always be easy prey for cybergangs – but it’s not ALL our fault, says industry veteran (2014-01-07)
- PC gaming service fined $1M for serving up Bitcoin-mining malware (2013-11-22)
- Fake Grand Theft Auto V tempts thousands of PC users to download “malware” (2013-10-23)
- Grand Theft Android: Gamers warned to avoid fake “iFruit” GTA app (2013-09-23)
- League of Legends players warned after major security breach (2013-08-22)
- Crytek latest gaming company to face security breach (2013-08-07)
- Nintendo site breached after month-long brute force assault (2013-07-08)
- Blizzard issues World of Warcraft security alert over auction house scams (2013-06-25)
- Xbox One Kinect microphone “always on” security fears (2013-05-22)
- PC game services admits to serving up Bitcoin-mining malware (2013-05-01)
- Up to 600,000 gamers at risk as emails and other details stolen from online zombie game (2013-04-04)
- Gamers warned of risks of “always online” games such as SimCity and Diablo (2013-03-27)
- PokerAgent botnet stealing over 16,000 Facebook credentials (2013-01-29)
- Foxxy Software Outfoxed (2012-08-07)
- Kids’ computer game malware – Scammers stoop to new lows (2011-10-06)
- SONY new Terms of Service – you can’t file a class action suit (2011-09-15)
- Win32/PSW.OnlineGames.OUM Part 2: Data Stealing (2011-08-02)
- Win32/PSW.OnlineGames.OUM Part 1: The Update Process (2011-08-01)
- Boys will be boys… (2011-07-11)
- SONY lawsuit: security experts fired prior to breach (2011-06-27)
- SONY Says Personally Identifiable Information Might Have Been Stolen (2011-06-08)
- A Nice Pair of Breaches (2011-06-07)
- SONY USA has an Opening for a Senior Network Administrator (2011-06-06)
- SONY Breached Again – User names and password published (2011-06-02)
- SONY Identity Theft Protection (Are there Stingers in the Honey?) (2011-05-27)
- Back to the Basics – AKA Not SONY Again? (2011-05-24)
- Hacking SONY for Fun and Profit (And Let’s Nail Your Company Too) (2011-05-23)
- SONY PlayStation – Rehacked reloaded?   (2011-05-18)
- SONY PlayStation Network and Qriocity Services Hacked – 77 Million Accounts at Risk (2011-04-26)
- Blackhat SEO uses online games to distribute malware (2010-06-19)
The post Gamescom: How gaming grew up into a target for crime appeared first on We Live Security.
![]()