There’s something every Instagrammer wants to know: who is looking at my photos? We live in a show-and-tell world, with I-see-I-do-I-post-mindsets, comments, and “likes”. No one wants to disappear at fault of a #boring photo.
Instagram makes it easy to play pretend, but what happens when someone else pretends to be you? In theory, social media sites like Facebook make it so that third parties can’t access your “secret information” but without our knowledge, hackers are taking advantage of us: robbing personal data (even those super-complicated-and-thoroughly-though-out passwords) and gaining full access to our profiles.
For Turker Bayram, hacking into social media profiles is his specialty. On multiple occasions, this sadly popular yet elusive malware developer has been able to place his malicious “apps” in the top charts on Google Play and the App Store. Soon after he creates them and uploads them, there are massive numbers of downloads. By the time someone figures out what’s going on, and after hundreds of thousands (potentially millions) of users are robbed of their personal information, Google and Apple finally delete the apps. This has happened at least twice.
Just a few weeks ago, an independent developer named David Layer-Reiss warned us on his blog about Bayram’s new malicious “software”. The iOS version was called “Who Cares With Me – InstaDetector”, and in Android, “InstaCare — Who Cares With Me”. These “apps” discovered by Layer-Reiss have already been eliminated and, in November 2015, both Apple and Google withdrew Bayram’s original platform, InstaAgent. It is not the first time malware takes over a popular site (i.e. Instagram, WhatsApp, Facebook) in order to massively rob user profiles… and it won’t be the last.
These “apps” always return to the top of the charts and sometimes under the umbrella of the same developer. In the case of “InstaDetector”, the victim innocently enters their credentials, unaware that the confidential data is sent to the attacker’s server. Instead of discovering “who has been looking at your Instagram?”, the cyber-attacker seamlessly accesses the account as if it were their own and posts spam photos on the owner’s behalf.
From telegrams to Instagrams, the more technically sophisticated we become the more important it is to trust the communication source, or in this case, the “app”. “InstaDetector” is just one of the many scams designed to take advantage of the enormous interest generated by social networks. The most worrisome thing about them is their popularity, always massive and immediate, that by the time Google or Apple are involved it’s too late for thousands of users. Combat these threats by staying alert, ignoring false promises, and installing a tough antivirus on all of your devices.
The post We know “who’s viewed your Instagram” and it’s not who you think appeared first on Panda Security Mediacenter.
 Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently,
Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently, 

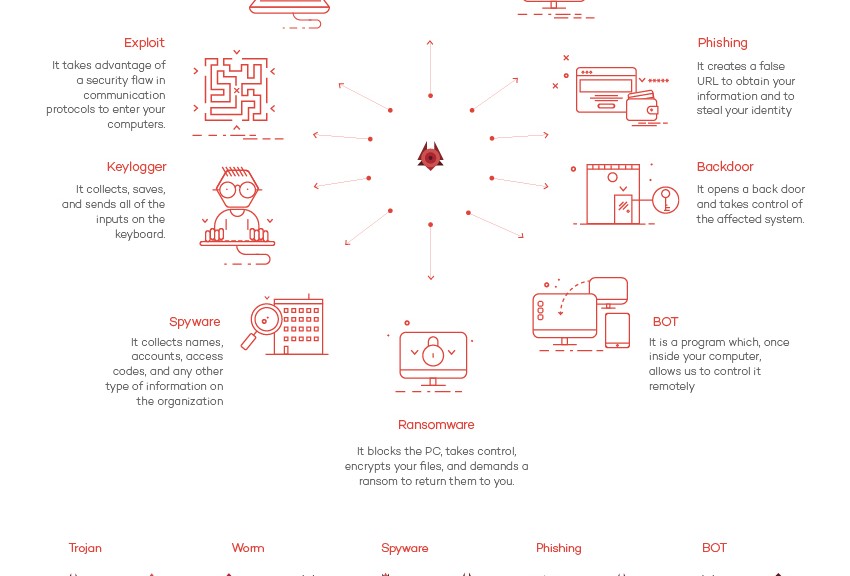
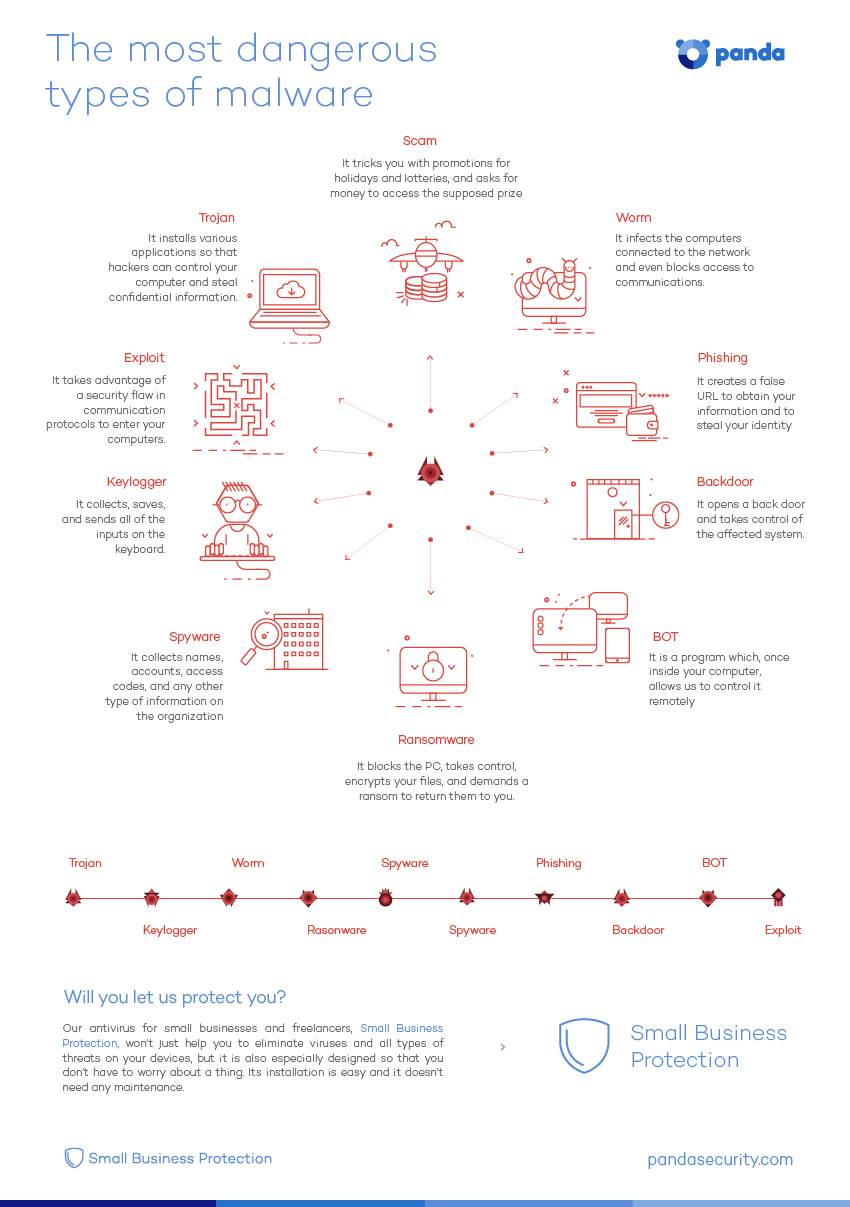













 A Logitech spokesperson has already claimed that the “vulnerability would be complex to replicate” and “is therefore a difficult and unlikely path of attack.” Despite that, the company has decided to develop a firmware update for the affected devices.
A Logitech spokesperson has already claimed that the “vulnerability would be complex to replicate” and “is therefore a difficult and unlikely path of attack.” Despite that, the company has decided to develop a firmware update for the affected devices.