The main objective of the Locky malware is to encrypt certain system files and network drives to coerce the affected user into paying a ransom to recover them. It renames all encrypted document as hash.locky files.
Systems are infected via an email attachment. When the user opens the attached Word document, they enable a malicious macro that runs a script to download Locky’s binary file.
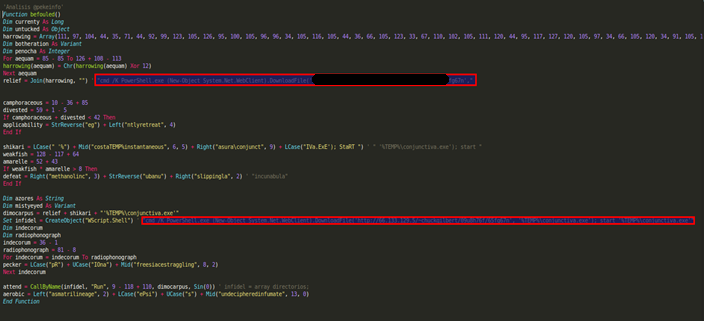
Macro code that runs the script
The script communicates with a server to download the malicious file to the %TEMP% folder and run it.

Trace used to download Locky to the target computer
Once run, Locky generates a unique machine ID using the operating system’s GUID. Then, it creates the following registry key with the generated value: HKEY_CURRENT_USERSoftwareLockyid. Additionally, it communicates with a C&C server to get the public key it uses to encrypt the system files with the RSA-2048 and AES-128 algorithms, and stores it in the following registry key: HKEY_CURRENT_USERSoftwareLockypubkey.
Locky downloads a .TXT file with the instructions for paying the ransom, saves it to the registry (HKEY_CURRENT_USERSoftwareLockypaytext), and creates a file named __Locky_recover_instructions.txt in every folder which contains an encrypted file. Then, when it is done encrypting the hard disk, it uses the ShellExecuteA API function to open the .TXT file.
Locky checks every file on the system, targeting those files whose extension coincides with the list of extensions included in its code. Those files are encrypted with AES encryption and renamed as hash.locky files.
List of extensions targeted by Locky
.m4u, .m3u, .mid, .wma, .flv, .3g2, .mkv, .3gp, .mp4, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .mp3, .qcow2, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11 (Security copy), .ms11, .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wb2, .123, .wks, .wk1, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .602, .dotm, .dotx, .docm, .docx, .DOT, .3dm, .max, .3ds, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .p12, .csr, .crt, .key
Finally, the malware uses the vssadmin command to disable the system’s shadow copy service, preventing users from recovering the backup copies created by the operating system. Then, it attempts to delete the .EXE file to remove any traces of its presence on the computer.
Although this variant doesn’t take any actions to ensure it becomes persistent on the system, other versions do add the following registry key:
HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun “Locky” = “%TEMP%[name].exe”
The post Locky malware report appeared first on MediaCenter Panda Security.