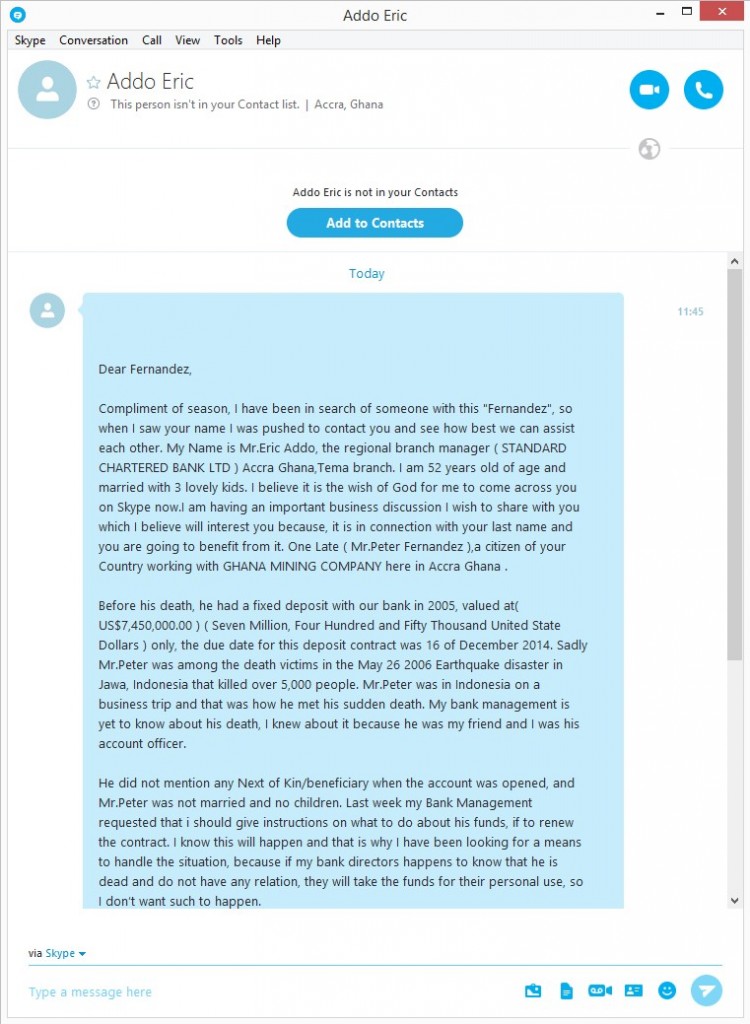
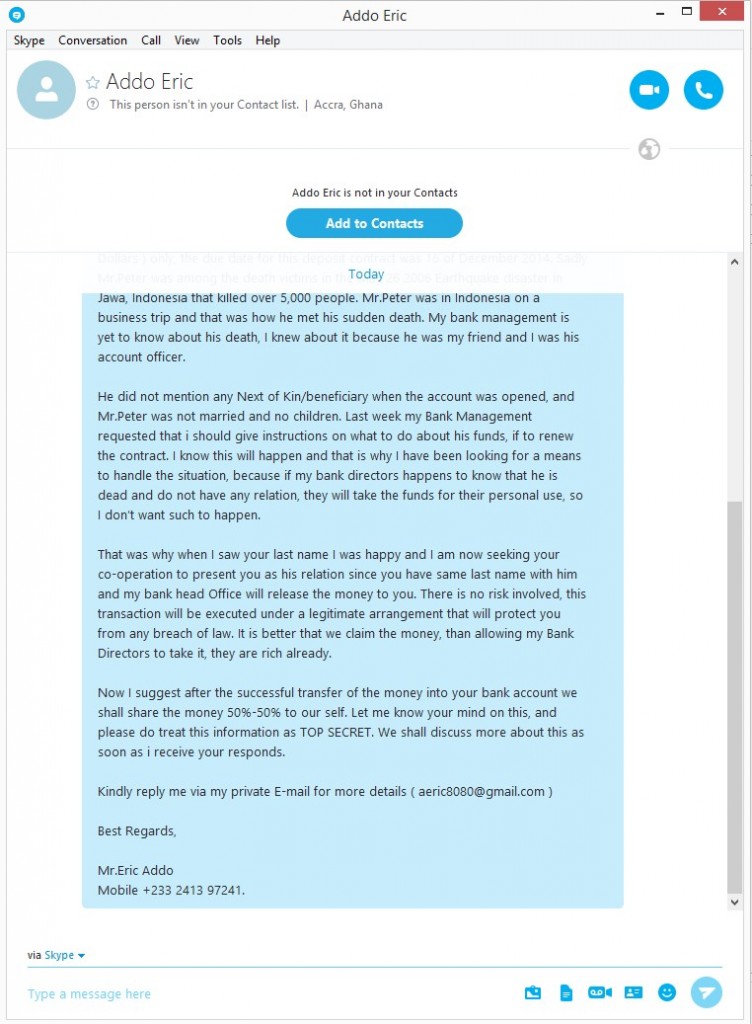
From offering discounted sunglasses (designer label, of course) to gift card for well-known stores, the world of SMS spam is one that continues to trick unwitting victims. You’d think that by now we would all be aware of the scams behind these messages which we receive on our mobile devices, but with these spammers becoming increasingly desperate to make a quick buck, they are using all manner of tactics to dupe their victims.
Luckily, the authorities are taking spam campaigns seriously. Just this week a US judge ordered Phillip Fleitz, a 37-year-old native of Pennsylvania, to 27 months in federal prison for his role in a massive spam campaign.

Over the course of nearly 2 years, the spammer sent millions of illegal spam messages to US and international cellphones and computers. With the help of two accomplices, Fleitz managed to earn between $2,000 and $3,000 per month by violating a 2003 law designed to protect cellphone and computer users from unwanted marketing and pornography emails and text messages.
The trio carried out their attacks by operating computer servers from China and using them to infiltrate the personal computers of millions of people worldwide. Naveed Ahmed, one of the accomplices, wrote a program that helped match cellphone numbers with their carriers. That allowed the scammers to bombard the phones with unsolicited messages.
The computer and text-message spam both included internet links. Those who received the text messages were told they had won gift cards that could be accessed by clicking on the links. In reality, those who followed the links were directed to web pages controlled by internet “cost per action” networks – marketing companies that collect email addresses and other personal information. Such companies are legal but using spam to drive traffic to them is not.
So, with this in mind, what can steps can you take if you receive unwanted spam on your cellphone? You’re in luck, as the latest Apple and Android cellphones allow users to block spam with relative ease.
iPhone users
If you have iOS 7 or later installed, open the spam message and click on contact, then on the “i” button that appears. A small contact card, mainly blank, will pop up and all you need to do is scroll down and select “Block this contact”.
To check out all of the numbers and spammers that you have blocked, you can view them in your message settings by scrolling down to Blocked.
Android users
For users of this operating service, blocking spammers is a little trickier but can still be done. First of all, the inbuilt messaging app doesn’t allow you to block anybody, so you’ll need to get an app from the Google Play store (remember to only download apps from official or trusted sources).
The apps available offer different forms of spam-blocking assistance – from ones that allow you to create a blacklist of contacts to others that automatically flag suspicious messages as spam.
If your Android device has been updated to KitKat (you can verify this by clicking on the “About Phone” section of your settings; if it’s 4.3 or above then it’s on KitKat) then you have it a little more complicated again. However, you can install Google Hangouts which not only sends and receives standard SMS messages, but lets you place spammers on a “blocked” list.
The post US man jailed for massive SMS spam operation – How to avoid becoming a victim appeared first on MediaCenter Panda Security.