With the Smartphone revolution and the wide choice of free messaging services available, receiving an SMS is definitely an unusual occurrence. Instead of being a way for friends and family to communicate, it has now become the preferred way for businesses to get in contact with you. However, you need to be vigilant of exactly what it is that these messages are trying to tell you as it could put your security at risk.
As was uncovered in a recent report published by the University of Toronto, SMS messages are being used by a group of cybercriminals to rob Gmail account passwords with the aim of accessing the victim’s account.
This attack doesn’t just avoid the two-step verification process offered by Google as a security measure, but also manages to work in a way that the victim won’t suspect a thing.

It all starts with an SMS being sent to the victim’s mobile. It appears to be from Google advising the user that someone has tried to access their email account.

The purpose of this message is to alarm the victim. Ten minutes later the victim will then receive an email which appears to be from Google warning them of an “unexpected login”. The email contains a link that, supposedly, will lead the victim to a website where they can change the password in order to reinforce the safety of their account. However, this couldn’t be further from the truth.
What really happens is that the user is brought to a phishing tool which permits the cybercriminal to obtain their password. What’s more, this false webpage will ask for the user’s verification code which is sent to the user’s mobile phone by SMS.
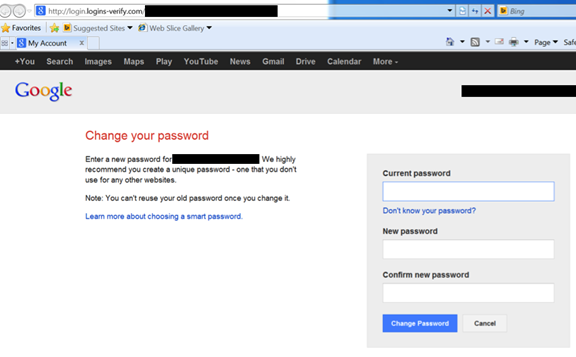
This way, in just two steps, they are able to steal your Gmail information and bypass the two-step verification process that Google has in place.
However, this isn’t the only attack that the investigators uncovered. Cybercriminals are also trying to steal password information by a phishing system which begins with what seems to be a phone call pertaining to a business proposal.
This is of course a trick and the false proposal was sent to the victim’s email account via a link that is held in a Google Drive document. Of course, to access this document the user must enter their Google password which allows the cybercriminals to get a hold of this private information.
So far what is known about these attacks is that they have originated from a group of cybercriminals based in Iran that have gone after political dissidents in their country. However, all Gmail users should take precautions and be alert to any possible scam, as anybody could become a victim of identity fraud.
To help protect yourself, and to be safe against any form of password theft, we recommend that you always create secure passwords and change them frequently.
The post If Google sends you an SMS warning you that someone has accessed your account… be careful! appeared first on MediaCenter Panda Security.