The success of WhatsApp has a downfall: while the instant messaging service reached 600 million active users last summer, the numbers of frauds emerging around the app are also growing steadily.
What are the most common scams in WhatsApp? What should we do so we don’t take the bait?
WhatsApp: 6 scams you must pay attention to!
-
A fake invitation to WhatsApp voice calls
With the arrival of WhatsApp voice calls a new fraud has emerged. While millions of users are waiting for an invitation to access this new feature, cybercriminals are distributing the malware via a link, which automatically downloads the malware.

To avoid falling into the new WhatsApp fraud, you should keep in mind that voice calls are only available for Android phones.
-
Frauds via browser
After WhatsApp launched their browser platform, fraudulent websites were created to steal your banking data.
This fake webpages use different types of scams:
- Asking for the phone number of the gullible users and then, subscribing them to downloading premium services which charge special rates.
- Making users download an application in their computers, but actually is a Trojan that will allow cybercriminals to obtain confidential information, such as banking information.
In this case, one thing to remember is that the only browser version of WhatsApp is free, and you don’t need to download anything to your computer to use it.
-
How to disable the blue double check
Scammers also tried to take advantage of WhatsApp’s double check launch. Before the instant messaging service allowed disabling this feature, in social networks we could find advertisements of fraudulent services for getting rid of the darned double check.
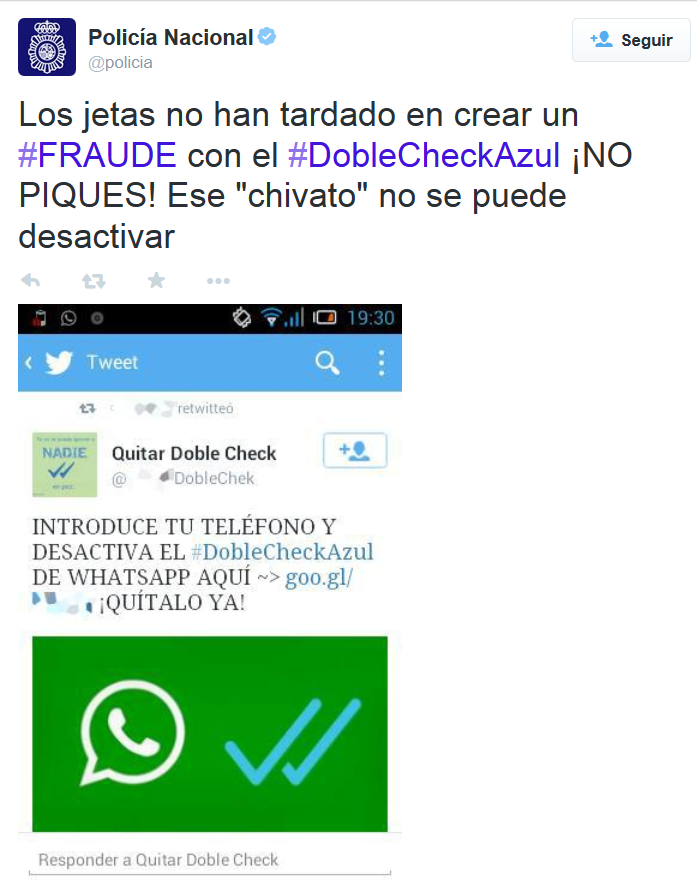
Getting some users to sign up for a premium SMS service without knowing it, which has a special rate. Remember: you can disable the double check feature from the app.
-
WhatsApp Gold
The Spanish National Police and Civil Guard reported a couple of months ago the existence of a scam that can be expensive, actually, 36 euros per month.
The fraud starts with a message via social networks in which WhatsApp users are invited to click on a link to update their app to the inexistent Oro version (Gold version), including supposed new and exclusive features. The link takes the user to a web page where, if he wants to use these improvements, he has to give his phone number.
In fact, all those who gave their number will subscribe to a premium SMS service: each text message that you receive will cost you 1.45 euros, until a maximum of 36.25 euro per month. If you ever cross paths with this message, remember there is only one official version of WhatsApp. Common sense is, as usual, your best ally.
-
The fake voicemail of WhatsApp
In contrast to the ones before, this scam doesn’t take the advantage of a recently launched service, it just invents one. It starts when a user receives an email, in which they inform him that he has an unread voice message in the WhatsApp nonexistent voicemail.
When he hits “Play”, there is no message, but it downloads malicious software that the scammers introduce to your device. From that moment on, text messages with special rates or the theft of confidential information can cause the user a great deal of trouble. Remember: there is no WhatsApp voicemail.
-
WhatsApp’s Spy
We are aware of the existence of WhatsApp Public, an application that allows you to spy your contacts in WhatsApp, but there is a scam that goes one step ahead and offers( with a similar name) a service which allows anyone to read conversations of others. But it is just another way of infecting with malware the gullible user’s phone.

Obviously, you can’t spy other people’s conversations and the only change it will bring it will come in your phone bill, which will increase considerably.
Remember that it is important to maintain your cellphone’s security. If you want, you can download free of charge our antivirus for Android.
The post WhatsApp: 6 scams you must pay attention to! appeared first on MediaCenter Panda Security.