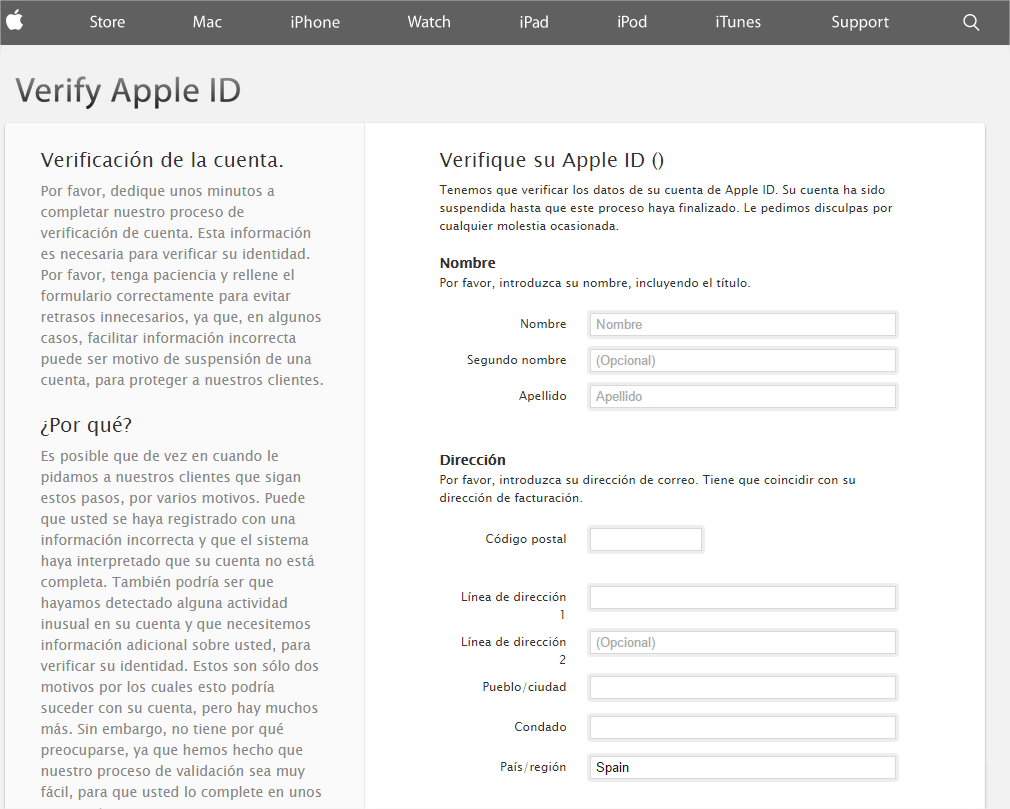
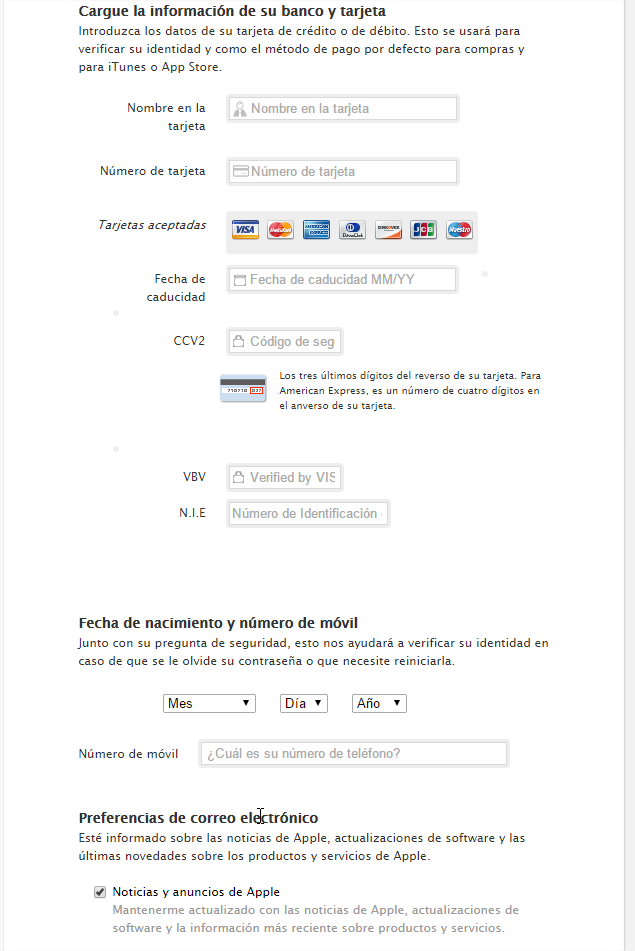
Recently we caught what seems to be a new ransomware variant in our nets. The mail contained a file called “Transferencia devuelta pago erroneo” (translated: “Transfer back erroneous payment”) with the .cmd extension and is actually just an executable.
When running the file, you’ll get the following notification:
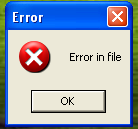
Error in file, nothing to see, move on… Right? Not exactly, in the background a new folder on C: called xwintmp is created and new files are being download and executed:
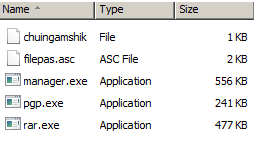 5 new files are created:
5 new files are created:
- chuingamshik -> file which contains the word “chuingamshik”, possibly the project’s name
- filepas.asc -> contains your calculated PGP key and ransom message
- manager.exe ->payload, dropped by Transferencia devuelta pago erroneo.cmd
- pgp.exe -> generates your custom PGP key
- rar.exe -> to encrypt the files
As to not arouse suspicion or to evade sandboxes, the malware then waits for a while using the Windows API “sleep” function and afterwards starts ‘encrypting’ all your files:
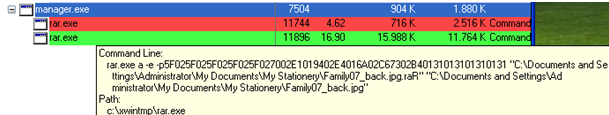
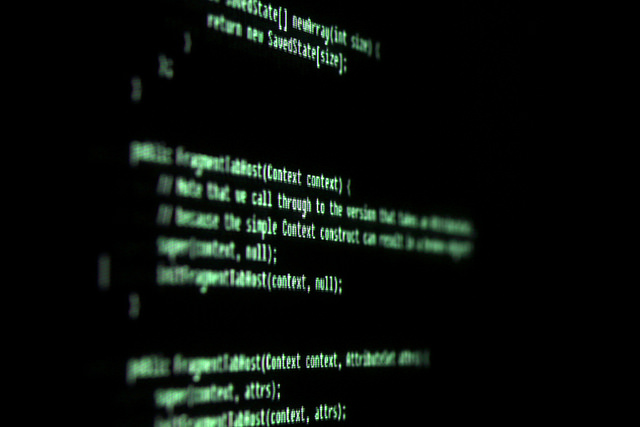
I’ve used single quotation marks here since there’s no real encryption going on, but rather the manager.exe file starts archiving (or “RARring” if you will) your files with some parameters and adds a password, using the command line version of WinRAR. The ransom creates a random key, unique per infection process. The seed for the random key is the Windows API “GetCursorPos”. “GetCursorPos” gets the current X and Y coordinate from mouse cursor, and is launched 16 times, making it impossible to guess or recover the key.
It connects to a TOR server where it sends the random key encrypted with PGP and the public key it contains.
Here’s the good news: when the malware is still encrypting your files, you can easily retrieve the password from memory as is also shown in the screenshot above. Starting with 5F0 and ending with 131 is in fact the password used to encrypt the files. You can use for example Process Explorer to determine the command line arguments and extract the password.
As said earlier, the filepas.asc contains your PGP key + a ransom note, which is as follows:
The files are packed in archives with a password.
Unpacked – 300 eur
To unpack the files send two files to email: [email protected]
1) file you are reading now
2) one packed file (no more than 1 megabyte)
In response comes the original file and the instruction for bitcoin transfer
(The original file is proof that it is possible to return all files to their original)
After the transfer bitcoin, you will receive your password to archives.
Also coming program to automatically unpack files
Reply to your letter will come within 24 hours.
If no response comes for more than 24 hours write to reserved e-mail: [email protected]
Do not pay for ransomware, but restore your files using Volume Shadow Copies or straight from a backup.
In case you’re fast enough, you can get the password and restore your files (kill the manager.exe process after copying the password though, or it will keep encrypting your files).
The post Yet another ransomware variant! appeared first on MediaCenter Panda Security.