It’s difficult to accept that we made an unwise purchase or even that a piece of technology has gone obsolete. But when it comes to the security of your home network, it’s time to face up to it.
Last February, Craig Young, a researcher at security firm Tripwire, published research showing that 80% of the 25 best-selling small office/home office (SOHO) wireless router models on Amazon had vulnerabilities. Because some routers, in fact, a lot of them, have so many non-patched vulnerabilities, the easiest way to secure your home network is to replace the router completely with a secure model.
How to update your router
But let’s not spend your money yet. Only four of the reported vulnerabilities were completely new, and many have been patched in later models, so you should first look for firmware updates. Some conscious manufactures release updates for their hardware controls and, if applied, could solve all (or at least some) known vulnerabilities.
Routers do not perform automatic updates, so the process requires appropriate patches to be manually downloaded and installed. Avast 2015 includes a Home Network Security scanner that can help you determine what needs to be done, explain why, and can direct you to the router manufacturer’s website.
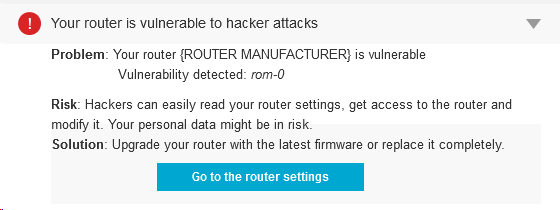
Open the Avast user interface, click Scan from the menu on the left, then choose Scan for network threats. Avast will take a look at your router and report back any issues. In most cases, if there is an issue to be addressed, then it will direct you to your router manufacturer’s website.
Yes, Virginia, there is a Santa Claus Router Attack
If you’re not convinced that router attacks are something to be concerned about, then think back on the attack from earlier this year. Attackers remotely altered DNS configurations for more than 300,000 small office/home office (SOHO) routers, subsequently opening up victims to a host of compromises
Among several vulnerabilities around, there is one that is quite common. It’s called ROM-0 and allows the attacker to easily gain control of the whole router and, subsequently, your Internet connection. In short, the attacker could request ROM-0 through HTTP (i.e. http://192.168.1.1/ROM-0) and then he can download all the important and secret data stored in your router: Your ADSL login/password combination, WIFI password and basically all your configuration data.
How to avoid attackers from downloading your Rom-0 configuration file and manipulating your router?
It’s simple (if you are comfortable around computers. Ask a techie to help you, if you’re not):
- Forward port 80 on the router to a non-used IP address on your network.
- Enter your router configuration and go to “Port forwarding†configuration.
- Send all http traffic, of all protocols, to star and end port 80 in a non-used local IP address (something like 192.168.0.xxx, where xxx would be a non-used IP).
There are free guides of “port forwarding†for quite a lot of routers. Check your model here.
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.