Do you trust the internet with your secrets?
Perhaps you shouldn’t, even if you’re using an app which professes to “deliver anonymously” secrets to your friends, and their circles, without identifying you as the owner of those secrets.
As Wired reports, researchers at Seattle-based Rhino Security Labs discovered a weakness in how the popular Secret app works, giving them a way of reading anybody’s supposedly anonymous postings.
At this point you’re probably imagining that for anyone to hack Secret, a popular app amongst iOS and Android users, would take ninja-like skills and advanced methods.
But in truth researchers found it remarkably easy, and the secrets of users can spill out within just a matter of minutes, as a Rhino Security researcher demonstrated to journalist Kevin Poulsen over lunch:
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
White hat hacker Ben Caudill is halfway through his sandwich when he casually reaches over to his iPhone, swipes the screen a few times, then holds it up to me. “Is that you?†he asks.
It is, but nobody was supposed to know. He’s showing me one of my posts to Secret, the popular anonymous sharing app that lets you confess your darkest secrets to your friends without anyone knowing it’s you. A few minutes ago I gave Caudill my personal e-mail address, and that was all he needed to discover my secret in the middle of a Palo Alto diner, while eating a BLT.
So just how did researchers manage to connect users’ email addresses with secrets they had posted via the Secret app?
Well, it’s breathtakingly simple.
When you create an account on Secret, the app requests access to your address book – so it can identify friends who might also be using the service.
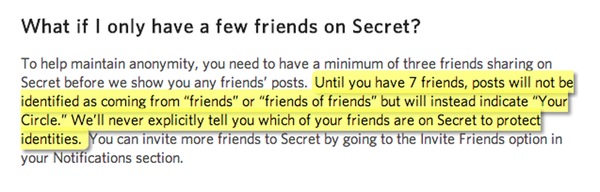
And, as Secret’s FAQ explains, you need at least seven friends before the app will begin to say that a secret has been posted by one of your friends (although, of course, it doesn’t identify which one).
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
Until you have 7 friends, posts will not be identified as coming from “friends†or “friends of friends†but will instead indicate “Your Circle.†We’ll never explicitly tell you which of your friends are on Secret to protect identities.
Does that sound reasonable to you?
Well, maybe this will make you think again.
Because what the researchers then did was create seven bogus Secret accounts – something that’s remarkably easy to do as Secret doesn’t require you to confirm your phone number or email address.
And then came the really clever part, as Kevin Poulsen of Wired explains:
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
Next, [Caudill] deleted everything from his iPhone’s contact list, and added the seven fake e-mail addresses as contacts. When he was done, he added one more contact: the e-mail address of the person whose secrets he wanted to unmask — me.
Then he signed up for another new Secret account and synced his contacts. He now had a new, blank Secret feed that followed eight accounts: seven bot accounts created and controlled by him, and mine. Anything that appeared as posted by a “friend†logically belonged to me.
Clever, huh? And, in retrospect, remarkably straightforward.
So all that was required to find out what secrets you had posted was your email address – something that, for most of us, cannot really be considered private or secret.
Secret CEO David Byttow told Wired that the vulnerability has now been closed, and claimed that they had no evidence that the privacy hole had been maliciously exploited.
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
“As near as we can tell this hasn’t been exploited in any meaningful way. But we have to take action to determine that.”
However, it’s worth bearing in mind that an absence of evidence is not evidence of absence. Just because Secret can’t tell if the flaw has been excused to embarrass or blackmail individuals who have posted compromising secrets, doesn’t mean that it hasn’t happened.
 And the Secret app’s developers have confirmed that since a bug bounty was introduced in February, a total of 42 security holes have been identified and fixed.
And the Secret app’s developers have confirmed that since a bug bounty was introduced in February, a total of 42 security holes have been identified and fixed.
Obviously it’s good that security and privacy vulnerabilities are being fixed, but when it’s your *secrets* which are at stake, wouldn’t you feel happier knowing that the app had been built on more sturdy ground in the first place?
One has to wonder whether Secret’s claims of “refined algorithms” to detect bots and suspicious activity on Secret are really enough to protect its users.
Secret is no stranger to controversy, of course.
Just this week a Brazilian judge has called for the app to be banned from official app stores, claiming that it encourages anonymous bullying.
But, in my mind, the problems lies not so much with the app but with the people who use it.
They clearly haven’t learnt the most basic rules of keeping secrets.
Don’t tell anyone. Don’t write it down. Don’t type it into an app. Never ever post it onto the internet.
As soon as you trust anyone or anything else with a secret, you’re doomed.
The post Secret app takes mere minutes to hack, revealing anyone’s secret via simple vulnerability appeared first on We Live Security.
![]()