Facebook have added the ability for organizations to detect if their OS X system is being exploited by XARA with their framework osquery.
Tag Archives: Apple
Apple reinforces security with iOS 9 and OS X El Capitan
Moscone Center in San Francisco (California), the same convention center where Google or Intel hold their events, welcomed around 5,000 developers between June 8th and 12th. All attended Apple’s annual Worldwide Developers Conference (WWDC).
Cupertino’s company officials revealed some of the features of the brand’s new operating systems, which are already available in their beta version. IPhones and iPads will update to iOS 9 and Mac computers to OS X 10.11 El Capitan, named after a vertical rock formation in Yosemite National Park (California).
In addition to the changes aimed to improve the user experience, in both new versions many of the innovations have to do with security. An aspect in which Apple has insisted over the past years.
One of the most obvious changes affect passwords. To increase the level of protection, the devices running iOS 9 after the update will require six digits passwords, instead of the standard four-digit one. However, you will be able to choose from several options: you can use a custom alphanumeric code, a custom numeric code or, as it was so far, a four-digit numeric code.
For those who decide to join the new format, this new passcode will make it more difficult for cybercriminals who want to take control over your phone or tablet. It allows over a million different combinations, significantly more than the 10,000 allowed by the current authentication method.
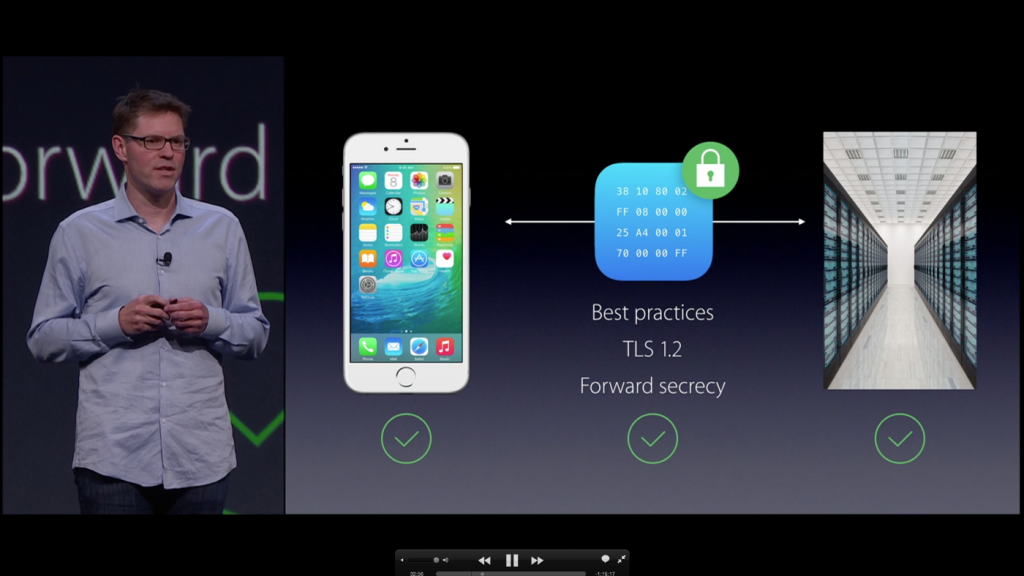
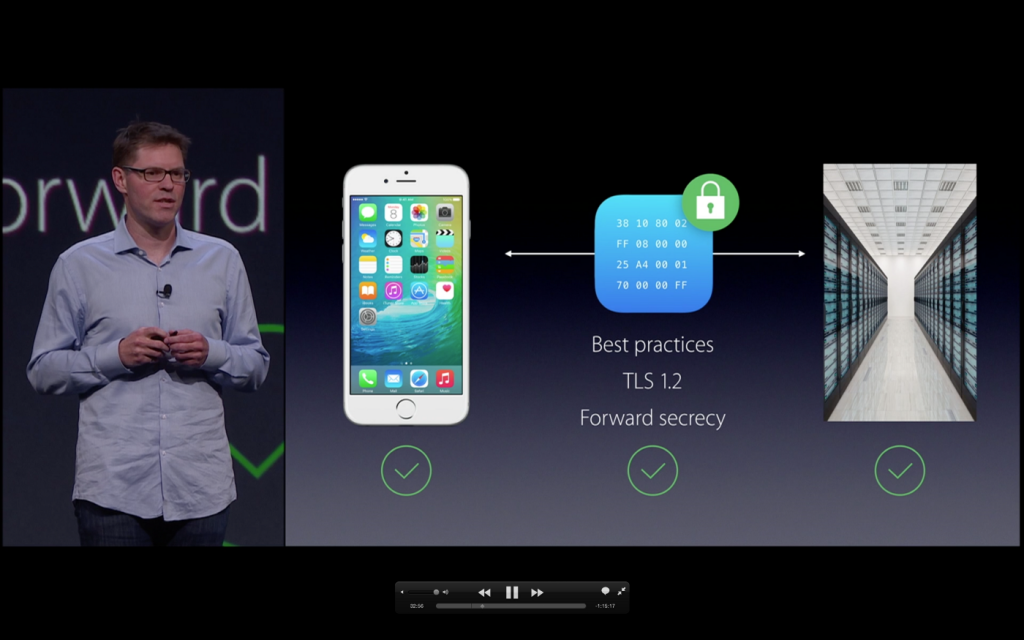
On the other hand, developers will have the best tools to guarantee the security of applications in their hands. With them, they will be able to connect their apps to the Internet via virtual private networks (VPN), a technology that allows a device to send and receive data in a public network with, in theory, as much security as if it was private.
Another important innovation is related to the Secure Socket Layer (SSL), which includes the protocols that encrypt communications over the internet. iOS 9 allows users to configure their system so that all internet connections made by their applications use HTTPS, a secure data transfer protocol.
In addition, Cupertino’s team ensure that the protocols will be updated constantly to avoid security vulnerabilities.
Another iOS 9 security goodness. Apple’s SSL library (SecureTransport) has support for Certificate Transparency! pic.twitter.com/d59VtFNwoH
— Frederic Jacobs (@FredericJacobs) June 8, 2015
Safari has also improved its security measures. On the one hand, the extensions will have a certificate from Apple. Developers can distribute extensions with their own signature, but the apps will not be updated by themselves.
On the other hand, this new version includes extensions to block content (‘Content Blocking Safari extensions’), a way of preventing the execution of cookies, pop-ups, automated videos and other web content.
Despite the rumors for iOS 9 that suggested it would be ‘rootless’, which means it would not be possible to gain access to root directories, this feature does not exist in the beta versions. It is true that Apple has changed the administrators’ privileges in OS X El Capitan, so they cannot modify any of the options of the critical system files. The measure prevents the installation of some types of malware, and its persistence. There are also those who think that it will serve, rather than to protect the security, to avoid that users apply the dreaded ‘jailbreak’ to Apple’s devices.
The post Apple reinforces security with iOS 9 and OS X El Capitan appeared first on MediaCenter Panda Security.
Looking back at WWDC 2015

Apple’s Worldwide Developers Conference kicked off June 8 at San Francisco’s Moscone West.
Earlier this month, I was lucky enough to attend Apple’s Worldwide Developers Conference (WWDC) in San Francisco, where mobile developers from far and wide came together to learn about the future of iOS and OS X systems. Along with being the first time I was able to participate in this sought-after conference, it was also my first time visiting San Francisco.
Once you get past its glitz and the glamour, the majority of the event revolves around waiting in a series of queues — the day before the actual event began, the line for the event’s keynote lectures had formed around an entire city block. Although I wasn’t one of the first people to camp out there, I did arrive around 5:30 a.m. on Monday to stake out my spot. While the masses of people at WWDC can be a bit overwhelming, there really isn’t a better place to meet thousands of like-minded developers with whom one can strike up an interesting conversation discussing the ins and outs of of iOS development.
This year, Apple hosted 5,000 developers from 70 different countries, the vast majority of whom were present at WWDC for the first time. The WWDC Scholarship Program awarded 350 scholarships to recipients, the youngest of whom was Kiera Cawley, a 12-year-old app developer who has been coding since the age of nine. Apple CEO Tim Cook made a guest appearance at the conference’s special orientation session, mingling with the recipients and even taking selfies with some of them.

WWDC 2015
OS X EL CAPITAN — what a name! At first, I thought it had to be another joke from Craig Federighi, but I was wrong. A noteworthy new feature in El Capitan is the split view mode, which allows us to work on two apps simultaneously. Apple claims that there has been a 1.4x time increase in app launch times and 2x improvement in app switching speeds. In general, Apple has been quite busy and has made huge improvements for developers. The most exciting news is that Apple will be making Swift open source later this year — a big step forward for the developer community.
The recent release of iOS 9 makes the entire system smarter and more secure. Now, users can run two apps at once on an iPad, side by side in split view (the same feature present in OS X). This will be challenging for developers who still don’t prefer Auto Layout. For the rest of us, though, it works quite well. It’s also possible to make activities and documents within your app searchable using Spotlight or to include special links on your site that launch your app at a specific view. And yes, it’s still necessary to support iPhone 4s on iOS 9. However, it should be more optimized now more than ever before.
Jennifer Bailey announced release of Apple Pay in the UK next month. This was a bad piece of news for the developer sitting right next to me. He was working as a freelancer for a company that provides mobile payments in the UK via iOS. “My company is screwed and I should start looking for a new job,” he said in response to Bailey’s announcement. Apple Pay’s imminent launch is, unfortunately, not the best update for people whose jobs revolve around mobile payments.
During the rest of the week, Apple featured 100 sessions and labs, and over 1000 Apple engineers were present and ready to give me advice. UI Design Lab was the most popular workshop at the conference, and you could count on the fact that there’d be a huge line every day. After trying to get into the session every morning, I was finally able to make an appointment on Friday. In the end, it was worth the wait. ![]()
All in all, WWDC was a great opportunity to meet an impressive collection of talented developers and to discuss the vast amount of progress Apple has been making within the mobile sphere. See you next year, Apple!
![]()
Reddit to Move to HTTPS-Only
In the two years since the details of the NSA’s deep penetration of the Internet infrastructure began to emerge, there has been a major movement afoot among Web companies to encrypt more and more of their resources and services. The latest large property to make this move is Reddit, which by the end of the […]
Apple iOS and OS X flaws leave passwords vulnerable
A vulnerability found in Apple’s iOS and OS X devices could allow hackers to upload malware and steal passwords for services including Mail and iCloud
The post Apple iOS and OS X flaws leave passwords vulnerable appeared first on We Live Security.
![]()
XARA – With This Exploit Hackers Can Steal Your Passwords
Six university researchers discovered high-impact “zero-day” security weaknesses in iOS and Mac, which can be abused by getting a malicious app approved by the Apple app store – something they managed to do without any issues. Through this app they were able to access sensitive data from other apps – with dire consequences. The researchers state that “our sandboxed app successfully retrieved from the system’s keychain the passwords and secret tokens of iCloud, email and all kinds of social networks stored there by the system app Internet Accounts, and bank and Gmail passwords from Google Chrome […]”
It does sound unbelievable, doesn’t it? Just take a look at the below video to see a malicious sandboxes app on OS X steal all private notes in the Evernote app:
Or how about a look at how it is able to steal any websites’ passwords:
According to their research 88.6% of the apps they tested were found to be completely exposed to the XARA attacks. This includes popular apps like Evernote, WeChat, and 1Password: “In our study, we downloaded 1,612 free apps from the MAC App Store. These apps cover all 21 categories of the store, including social networking, finance, business, and others. In each category, we picked up all the free apps when less than 100 of them are there, and top 100 otherwise. Also from the iOS App Store, we collected 200 most popular apps, 40 each from “All Categories”, “Finance”, “Business”, “Social Networking” and “Productivity”, after removing duplications.”
The researcher informed Apple about the issues in October 2014, a fix seems to be still outstanding.
Take a look at the research paper to read all about the issue.
The post XARA – With This Exploit Hackers Can Steal Your Passwords appeared first on Avira Blog.
iCloud celebrity photo hack: What’s fappening?!

Via: Huffington Post
Just about a year after a plethora of celebrities’ nude photos were leaked online, two homes in south Chicago have been raided and investigators have named one of the suspected hackers. As this controversial story and investigation continues to unfold, Avast researchers have come up with a few speculations regarding the origin and motivation behind the initial hack. We’ve discussed the case with one of Avast’s security researchers, Filip Chytry, who has put in his two cents about the situation:
GR: Why might have Apple not flagged or investigated an IP address’ 572 iCloud logins and attempted password resets?
FC: “Putting it simply, Apple just doesn’t have security implemented on this level. Even though they might sound large to us, attempting to track this number of logins and attempts to reset passwords is similar to discovering a needle in a haystack when it comes to Apple’s ecosystem. To give you a better idea of what I mean, a group of users who are connecting via a VPN and using the same server will appear under a single IP address. On the other hand, it’s quite common these days for companies to implement an automatic system which is capable of detecting any source(s) of traffic. It could be an automatic system which is able to learn from daily traffic and, using gathered data, detect if there is an anomaly present (such as the one in this case). Another key factor relevant in this attack is the timeframe over which it took place. If the hackers had accessed the various accounts over a much shorter period of time, such as a few hours, it would have undoubtedly been a huge red flag for Apple.”
GR: Couldn’t it be that a neighbor or another person in a remote location could have used the two PCs as a bot to execute the hack, similar to what’s discussed in the Tweets published within this Fusion article? Could it be that someone took control of the two PCs or the routers they’re connected to and used them to perform the hack?
FC: “Although DNS hijacking could very well be the culprit here, the extended period of time over which the hacks occurred makes this possibility less likely. It’s my theory that the suspected hacker(s) could have accessed the login details of a certain database that was uploaded by other users on a warez forum. They could have then used these login details to execute the iCloud logins using a script.”
There are a handful of coincidental components present in this investigation, leaving many questions unanswered in terms of finding the true path that led to the celebrities’ photos getting leaked. To many of us, the main thing that seems fishy about the malicious attack is the fact that the potential hackers didn’t make use of an IP-masking or anonymizing tool, making them come across as rookies within the hacker world. Since the cybercriminals behind this case didn’t appear to be clever enough to anonymize themselves, it’s even possible that they had ulterior motive for performing the hack in the first place – perhaps to be noticed and/or admired by other individuals or businesses. Based off of the current facts, we’re highly interested in seeing which direction this malicious attack’s investigation will take next.
![]()
Duqu 2.0 Attackers Used Stolen Foxconn Certificate, Signed Driver
The attackers behind the recently disclosed Duqu 2.0 APT have used stolen digital certificates to help sneak their malware past security defenses, and one of the certificates used in the attacks was issued to Foxconn, the Chinese company that manufactures products for Apple, BlackBerry, Dell, and many other companies. Researchers at Kaspersky Lab, who discovered […]
Flaw in Mail.app Can Be Used to Hijack iCloud Password
The flaw lies in the Mail.app, Apples default e-mail program for iOS. According to security researcher Jan Sourcek “this bug allows remote HTML content to be loaded, replacing the content of the original e-mail message. JavaScript is disabled in this UIWebView, but it is still possible to build a functional password “collector” using simple HTML and CSS.“ To reduce suspicion the code even detects if someone has already visited the page in the past by using cookies. If this was the case it stops displaying the password prompt.
This means that hackers could easily create phishing mails which show a form that looks exactly like the iCloud login pop-up window everyone knows. The user would be asked for their username and password, which – once entered – would then be transmitted to the cybercriminals. Just take a look at the below concept-of-proof video to see how easy it would be to trick the unsuspecting user!
Sourcek discovered the flaw in January 2015 and informed Apple immediately. Since then no action has been taken in order to fix said vulnerability. In the hope that it will make Apple take the bug more seriously, the security researcher has now published his findings together with a proof-of-concept video and the corresponding code.
Feel free to follow this link in order to find out more about the issue.
The post Flaw in Mail.app Can Be Used to Hijack iCloud Password appeared first on Avira Blog.
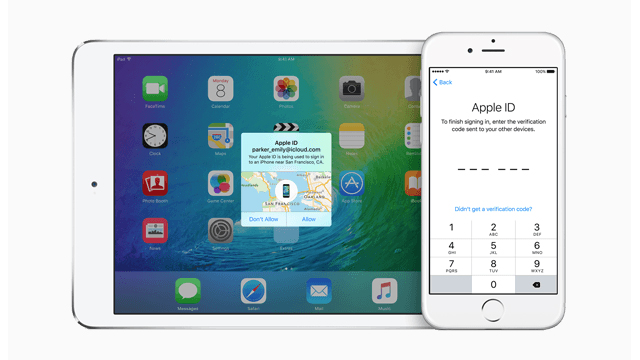
Apple Moving to 2FA, Six-Digit Passcodes in iOS 9
With each new release of iOS, Apple has been improving the security of the mobile operating system, adding new features, inserting exploit mitigations, and taking away avenues for attack. In the forthcoming iOS 9.0 release, the company is continuing this movement with the addition of two-factor authentication and a number of other security features. Last […]