Google added a cool feature to chrome. It is voice search. They just forgot to ask the users before doing so.
The post Google, Chromium, HotWord, and our Avira browser appeared first on Avira Blog.
Google added a cool feature to chrome. It is voice search. They just forgot to ask the users before doing so.
The post Google, Chromium, HotWord, and our Avira browser appeared first on Avira Blog.
Nowadays, our Personal Computers are able to perform a huge amount of tasks as we can find Applications for mostly everything one can imagine. Not to mention, we often have more than one App installed for the same kind of task. When does it become too much?
The post Legit APPS or PUA? Keep your eyes wide open! appeared first on Avira Blog.
Windows 10 will be launching in T-minus seven days and will be offered for free within its first year of availability to Windows 7 and 8 users. Not only will the beloved Start button be back in Windows 10, but Windows 10 will also include a personal assistant, Cortana. What’s more, the new operating system will introduce many promising security features and a new browser.
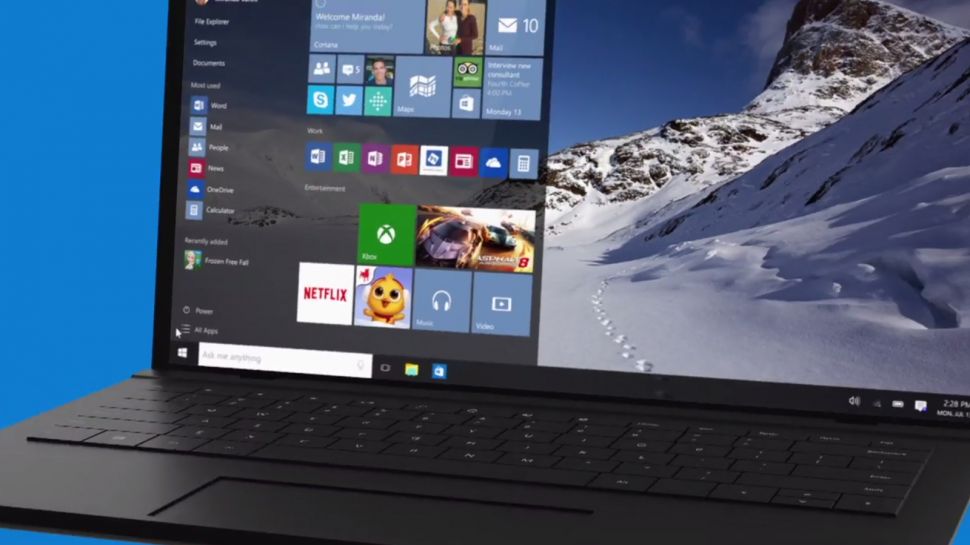
Image: TechRadar
Hello there, Windows Hello and Passport!
Windows Hello is biometric authentication that either scans your face, iris or fingerprint to access your Windows 10 device – very secret agent-like security! By doing so, Windows Hello eliminates the chance of hackers stealing your password to access your device, simply because you will no longer have a password to begin with!
Windows Passport also eliminates the use of passwords to access your online accounts. For now, Microsoft will work with the Azure Active Directory and has joined the FIDO alliance to subsequently support password replacement for other consumer, financial and security services. Windows will verify that you are truly the one using your device through a PIN or via Windows Hello, and then it will authenticate Windows Passport so you can log in to websites and services without ever using a password. Combined use of Windows Hello and Windows Passport would mean that a hacker would not only have to physically steal your device, but also kidnap you to access your accounts.
You will, of course, need hardware that is capable of infrared scanning your face or iris, or that has a built-in fingerprint reader to use Windows Hello. Microsoft has already confirmed that all OEM systems with Intel® RealSense™ 3D Camera (F200) will support Windows Hello’s facial unlock features.
Bye-bye Patch Tuesday
Microsoft usually issues security patches on the second Tuesday of every month, which can leave users vulnerable until Patch Tuesday comes around. In Windows 10, Microsoft will regularly issue security patches and users will be forced to accept every update, meaning they will be immediately protected from zero-day bugs.
Forcing updates is a good move. It’s the same as with an antivirus – everyone wants to have an up-to-date database to protect their system as much as possible. – Jiri Sejtko, Director of Virus Lab Operations
More app developer security support
AMSI – Antimalware Scan Interface will help protect users from script-based malware by offering an interface standard that allows apps and services to integrate with antivirus programs on Windows 10 devices. App developers can have their application call the AMSI interface for additional scanning and analytical services. The interface will look for potentially malicious content such as obfuscation and evasion techniques used on Windows’ built-in scripting hosts. Antivirus vendors can implement support for AMSI so that their engine can gain deeper insight into the data that applications consider potentially malicious. Avast will be implementing AMSI in the near future.
Edge, the edgy new browser in town
Microsoft’s Internet Explorer doesn’t have the best reputation, which is probably why Microsoft is introducing the new Edge browser in Windows 10. Edge was created from the same core as Internet Explorer by removing many of the old outdated features that were kept for compatibility reasons, including support for binary extensions like Active X and Browser Helper Objects. Basically, Edge will not support any browser extensions in its initial release, but will add a Javascript/HTML model similar to that of Mozilla, Google, Apple and Opera later on to offer browser extensions. Flash will be built into the Edge browser as well as PDF rendering. Additionally, Edge will be deployed as a Universal Windows App, so users can update Edge from the Windows App Store rather than via Windows updates, and it will run in a sandbox, meaning it will have little to no access to the system and other apps running on your device.
Not supporting any extensions and running Edge inside Windows’ sandbox is very good from a security standpoint. Browser extensions can not only distract users, but they can slow down the browsing experience and can create a huge security risk if abused, as they can see everything you do within the browser, including on encrypted sites. – Lukas Rypacek, Director of Desktop Platform
Avast is already compatible with Windows 10
Avast has been compatible with Windows 10 since March.
No major changes were needed to make Avast compatible with Windows 10; we had to slightly change some components to make everything work as it should, but no changes were needed in terms of behavior and communication. What we are now doing is migrating users to the latest version of Avast to ensure a smooth Windows 10 upgrade. – Martin Zima, Senior Product Manager
Are you looking forward to Windows 10 and will you be upgrading? Let us know in the comments section ![]()
Follow Avast on Facebook where we keep you updated on cybersecurity news every day.
![]()
The goal with the browser is to create an easy-to-use, secure and privacy respecting browser. These are the more advanced tactics we will be using:
Adding cloud features to file scanning was a large success. The detection quality of malicious files went straight up. Short:
On the client there is a behaviour detection kind of pre-selection. If a file is suspicious the cloud server is asked if the file is already known
If unknown:
We built incredible databases covering malicious files during the last years. We should have something similar for the browser and use our large knowledge base and server side classification tools for web threats as well.
It should look something like that:
 )
)To get there we will have to improve the signal-to-noise ratio. We are only interested in malicious pages. If the pre-selection in the browser is too aggressive and sends non-malicious pages to us, it‘s a waste of CPU cycles and bandwidth. With millions of users as a factor, even minor slips will be expensive and annoying for everyone involved.
We will also remove private data before sending it (we are not interested in user data. We are spying on malware). Personal data is actually toxic for us. Servers get hacked, databases stolen, companies gag-ordered. Not having that kind of data on our servers protects us as well as you. I mean just think of it: Some web pages have the user name in the URL (*/facepalm*). I do not think we can automatically detect and remove that trace of data though. But maybe we could shame the web pages into fixing it …*/think*
The parts in the source that collect the data and prepare them for sending are Open Source. Here I am asking you to NOT trust us and review the code! 
I hope we find a simple solution to display the data being sent to us before sending. The only problem is that it could have a negative impact on your browsing experience. Having a modal dialog when you expect a page to load …
One option could be to at least offer a global configuration to switch cloud requests off (always, in incognito mode only, never) and show you in logs what got sent.
You want your own AV? Or protection technology in your Tetris game to make it unique? Just contact our SI department and make a deal.
Other companies have thousands of web-crawlers simulating user behavior to identify malware.
Millions of real Avira users are our scouts and sensors.
We need some branding. That would include Avira specific changes in the browser (names, logos, some other texts). But also links. This is not only relevant for brand-awareness but also to keep our users away from Chrome/Chromium support to avoid confusion (“Which Chrome version do you have ?” … listens … “we never released that, can you please click on “about and tell me the version number” … listen … “WTF?!?” => Confusion) and direct them to our support – who actually CAN help.
We will always improve the build process. There are compiler switches for features called Position Independent Executable (PIE), Fortify Source, etc. that we should enable on compilation (many are already enabled). Most time here will be spent on ensuring that they do not get disabled by accident, are enabled on all platforms, and do not slow down the browser. This task can start simple and suddenly spawn nasty side effects. This is why we need TestingTestingTesting.
Google added the Hotwords feature to Chromium and Chrome. It’s a nice feature. But it switches on the microphone and “spies” on the user (this is a convenience feature many users want). For our secure and privacy respecting browser this crossed a line though. This is the reason why we will have to verify that no “surprise !!!”-Extensions get installed by default. One more task for our testers that add verification tasks to the browser to handle our specific requirements. Keep in mind: Chrome and Chromium already have very good unit-tests and other automated test cases. We just need some extra paranoia. That’s the job for our testers in the team.
We will write blog posts covering all the features. The attacks they block, their weaknesses, what we did and will be doing to improve them. We will offer you a guided tour Down the Rabbit Hole. Go with us as far as you dare.
TL;DR:
There is so much we can do to improve the browser; without touching the core.
We reached the bottom of this specific Rabbit Hole.
Thorsten Sick
#content .entry-content
.bq{width:100%;border:1px
solid #dde5ed;margin-top:0px;margin-bottom:25px}#content .entry-content
.quest{margin:0px;font-weight:bold;font-size:16px;text-shadow:0px 1px 0px #f8fafb;padding:6px
11px;background:#eaeff5;border-top:1px solid #f4f7fa;border-bottom:1px solid #dde5ed}#content .entry-content
.text{line-height:19px;margin:0px;padding:10px;font-size:14px;background:#f8fafd;color:#758fa3}#content .entry-content .text
p{line-height:19px;background:#f8fafd;font-size:14px;color:#758fa3}
The post Avira’s Secure Browser: Plans and Tactics (Part 2) appeared first on Avira Blog.
In order to have a secure browser, security issues have to be fixed in a certain time frame. This sounds logically, right? For us that’s only a few days after we get to know about them. Chrome fixes vulnerabilities with every release, so we are also forced to release in sync with the Chrome releases. But every change we make in the Chromium source code causes merge conflicts. When changes made by us (and which are Avira specific) and changes made by Chromium developers overlap our tools cannot combine them together. After about 150 changes we had one conflict per week. This meant spending hours untangling code.
The sword to slice through the knot: We will not introduce differences to the Chromium code.
Let’s see the browser more like a Linux distribution (Ubuntu, for example). We select the best tools. Combine them. Maintain them. Optimize them.
There are awesome security extensions for browsers out there. Let’s just invest some man-years, copying their features. We can make closed source versions of those extensions which are almost as good as the original – but OURS!
… just kidding …
We decided to say ‘hello’ to the communities and explained our plans to them. We already started to contribute and will contribute even more (we struggled with the foundation for the browser longer than expected, so we are a bit behind the original time frame – but more about that in another post). The first extensions are integrated, more are upcoming and planned. Efficient engineering. A win-win situation.
Only code differences between our browser and Chromium cause issues. If we want a security feature and contribute the code to Chromium we do not have differences nor merge conflicts. We accidentally protect more people than we have to, but nobody is perfect. 
We already did contribute a stash of changes that allow simpler branding (see below). But the HTTPS-Everywhere guys alone have a wish list of 2-3 large Chromium code changes. Our next steps will be to extend the extension programming interface (API) because we want more information available in the extensions. For example right now the encryption details (used cypher suite, Certificates) cannot be seen from an extension. That means that something like Calomel cannot be written for Chrome so far.
Chromium contains more than 100 third party libraries. They can contain vulnerabilities, bugs and flaws. When we find something we fix it and send the patches upstream (= to the authors). We are currently experimenting with the best way to release as many fixes per week as possible. As soon as we have figured out a good solution, we will inform you via another blog post.
Of course we already integrated ABS (Avira Browser Safety) and our Safe Search. This is a no brainer. So let’s just move on.
Right now we plan on integrating our AV scanner into the browser. We already scan with the WebGuard, but the future of the internet is encryption (more HTTPS, o/). Webguard is a proxy, and scanning encrypted traffic with a proxy causes lots of crypto-headache. Luckily the browser does decrypt the data (it has to) as soon as it gets there: Scanning the content of the decrypted data packages directly inside the browser solves said crypto-headaches.
As of now WebGuard is fine. But of course we already plan for the future. When the future is here we will be ready – with scanning abilities in the browser.
This above are only about 50 % of what we plan on doing. Stay tuned for two more and rather advanced tactics that we plan on using and which will be described in the next blog post!
TL;DR:
There is so much we can do to improve the browser. Without touching the core.
Halfway down the Rabbit Hole. Time for a break.
Thorsten Sick
The post Avira’s Secure Browser: Plans and Tactics (Part 1) appeared first on Avira Blog.
Chrome got both its stable and beta versions hacked in just two minutes. Google paid $75,000 for just one buffer overflow in Chrome which allows an attacker to bypass the sandbox.
Apple’s Safari got also hit by using a use-after-free (UAF) vulnerability in an uninitialized stack pointer in the browser and bypassed the sandbox for code execution.
Internet Explorer 11 64-bit was taken out with a time-of-check to time-of-use (TOCTOU) vulnerability allowing for read/write privileges. The attacker evaded all the defensive mechanisms by using a sandbox escape through privileged JavaScript injection, all of which resulted in medium-integrity code execution.
Mozilla Firefox was hit with an out-of-bounds read/write vulnerability leading to medium-integrity code execution.
A team of researchers showed their skills against Flash by using a heap overflow remote code execution vulnerability and then leveraging a local privilege escalation in the Windows kernel through TrueType fonts, bypassing all defensive measures. They were awarded $60,000 for the Flash bug and a bonus of $25,000 for the SYSTEM escalation. Another researcher exploited Flash by using a use-after-free (UAF) remote code execution vulnerability and sandbox escape directory traversal vulnerability in the Flash broker.
Adobe Reader was exploited twice through a stack buffer overflow – once for an info leak and again for remote code execution. The researcher leveraged an integer overflow to exploit the broker, netting him a cool $60,000 USD. For the day, that brings his total payout to $90,000 USD.
The final numbers for Pwn2Own 2015 are quite impressive:
5 bugs in the Windows operating system
4 bugs in Internet Explorer 11
3 bugs in Mozilla Firefox
3 bugs in Adobe Reader
3 bugs in Adobe Flash
2 bugs in Apple Safari
1 bug in Google Chrome
————————————-
$557,500 USD bounty paid out to researchers
As with every Pwn2Own, all vulnerabilities were disclosed to their respective vendors in the “Chamber of Disclosures,” and each vendor is working to fix these bugs through their own processes.
The post Pwn2Own: Nothing is safe appeared first on Avira Blog.
Google and the University of Pennsylvania performed a study intended to determine the effect of best practices on the efficacy of SSL browser warnings.
All kinds of fun facts bounce around the internet. You might have seen the one about contextual reading: It deson’t mttaer in waht oredr the ltteers in a wrod aepapr, you can sitll raed it wouthit pobelrm. See how this neuro-scientific peculiarity helps phishing criminals earn lots of money and what simple things you can do to protect yourself.
As I work in the URL detection team of Avira’s Protection Labs, you might not be surprised by me saying that URLs are a very important part of our daily lives. In ancient times, ten or fifteen years ago that is, data was shared through floppy disks, which were still in heavy use back then. (You know, the legacy industrial equipment that looks like the ‘Save’ button in your applications.) Times have changed and so has the industry. In today’s world, files are distributed over the Internet. File hosting services, like Dropbox and OneDrive, flourish like never before. The Internet actually consists of many subsystems like email, file sharing and the Word Wide Web. Also known as just the Web, the latter represents what you usually do in your browser: click on links, enter URLs in the browser bar, search the web; those are all examples of how you use URLs to access the Web.
Avira’s domain entered in a web browser
Domains exist because they are easier to remember than IP addresses (which domains point to). They operate pretty much like a phone book. You do not remember the phone number of a person to call, you look them up in the phone book. This establishes the connection between person and callable number. While you still have to enter the number yourself on the phone, your browser will take that burden off of you. So, when you enter www.wikipedia.org in your browser, it will look up and redirect you to the proper IP address of the web server that hosts the site. If you enter www.wikkepedia.org, you will not be redirected to the site you intended to visit but rather receive a browser warning, stating that the website does not exist – just like the well-known “The person you’ve called is temporarily not available” message you hear on the phone when you dial the wrong number.
“Where does the neuroscience bit come into play?”, you might ask. Cyber criminals are able to register this domain and host advertisements. Once you accidentally enter the wrong URL, you will be redirected to this so-called typosquatted domain and thus will have accessed ads. This in turn generates money for the advertiser. Check out my other article about online advertisements for further information. The important thing to remember is, that this is possible not due to careless surfing. It works because the human brain operates with contextual sections.
Some just want to make a few bucks by registering a misspelled domain in order to sell it back to the brand owner. One could register www.citybank.com and sell it to www.citibank.com, as this is a common misspelling.
Other unfair practices include redirection to potentially unwanted applications (abbreviated PUA). Your browser will typically show a warning about the state of your computer – telling you it might be infected, your drivers might be out of date or that you have won a million dollars. To give you a practical example: I found this software recommending driver updates for my computer while going through misspelled Wikipedia links (I omit the direct URL for obvious reasons). A click on “Installieren” (region-specific, as I am browsing from Germany), tries to install the software that I do not actually intend to have on my PC. Fortunately, I am one of the lucky people having Avira security products installed. The Web Protection kicks in and saves me from accidentally installing PUA on my PC.
No antimalware solution will ever give you 100% security. They are considered to provide you with something in between base and enhanced detection of malicious software on your PC. Nowadays, those programs also include effective web protection like cloud-based scanning of URLs. Avira offers both traditional antimalware solutions and an unobtrusive browser plugin to protect you against most of it. However, you should never solely rely on software to protect you. It helps a lot to know about the risks. You just might look twice the next time. ![]()
Breaking the Code: Why Yuor Barin Can Raed Tihs
Typosquatting
We knew the web was big…
How Big Is The Internet?
TypoSquatting – Malicious Domains Malware Domains
The post On Neuroscience and Phishing Attacks appeared first on Avira Blog.