What happens if someone “owns” your DNS records
The direct consequence is that suddenly when contacting domain.com and all its subdomains (www, mx, ftp, etc.), some other servers owned by the new owner (legal or attacker) answer.
This disruption in normal operation means a loss of reputation, loss of market share, loss of trust from your customers and last but not least, financial loss for your business.
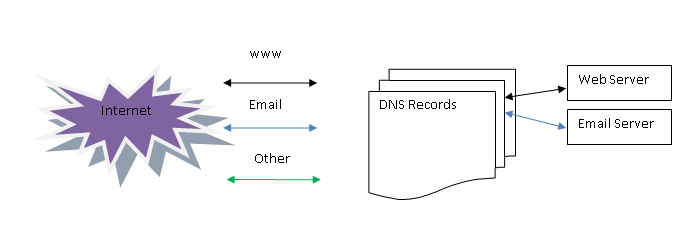
Unaltered DNS records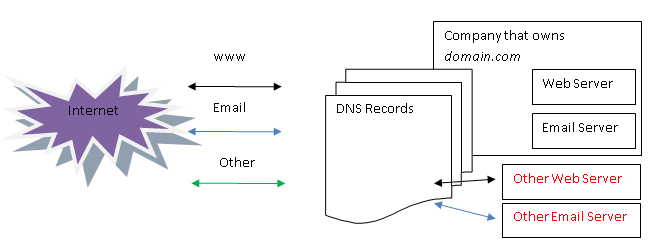
Altered DNS records
As can be seen in the above illustration, from the moment in which the DNS records are altered, the company that owns domain.com will no longer control where the traffic goes. The new owner can set up his web server to serve www.domain.com and his email server to serve mx.domain.com. Yes, this means that he can receive all email traffic for that domain.
Owning a black-white list can have even more consequences: the new server can serve whatever fits its needs. Either block any request reporting back that the item should be blacklisted (valid web sites, emails, files, etc.) or allowing everything (marking as good any malicious website, email, file). Fortunately, in such services there are many other controls that make such a task pretty complex.
What can you do to secure your domains?
Yes, there are things which you can do to prevent an attacker from taking ownership of your domains.
Lock your domains
Domain Lock or Registrar Lock is a status which can be set to a domain. When set, the following actions are prohibited by the registrar:
- Modification of the domain name, including:
- Transferring of the domain name
- Deletion of the domain name
- Modification of the domain contact details
Renewal of the domain name is, however, still possible when this flag is set.
Unfortunately, not all registrars support this functionality. If you want more security, you should choose a registrar that supports this feature. This functionality usually doesn’t come for free, but the price is not very high (10$-50$/month) and it is worth paying, especially if you have a large website or company.
Secure your domain administration information
All registrars allow entering contact persons for various functions. For example, there are some contacts for changing the IP address or deleting the domain and some others for paying the subscription. Make sure you separate them. Also, make sure that you have a contact email address that is not hosted at the respective domain. Otherwise, if something happens to the domain, you can’t access your email anymore. Remember that all traffic goes to the new owner, including your emails.
If you use some free email servers like Gmail, Yahoo or others, make sure to activate two factor authentication for those accounts.
Set up a good password and make sure you don’t use the address hosted on the domain you try to protect as the recovery email address.
Make it harder for the attacker to get access to your account.
If you have multiple domains, it would be better to host them at different registrars. If one goes down, you can at least use the other ones.
The post Secure your DNS to avoid losing business – Part 3 appeared first on Avira Blog.