A “white hat” is how we described the hacker who added Avira installers to the Dridex botnet distribution network. Our description might have been a bit off-color.
The post 50 Shades of Dridex Botnet Grey appeared first on Avira Blog.
A “white hat” is how we described the hacker who added Avira installers to the Dridex botnet distribution network. Our description might have been a bit off-color.
The post 50 Shades of Dridex Botnet Grey appeared first on Avira Blog.
A distribution channel of the Dridex botnet may have been hacked. Instead of getting loaded with malware, people are getting clean copies of Avira antivirus and we have two theories as to why. Do you know what a “white hat” is?
The post Dridex botnet distributor now serves Avira appeared first on Avira Blog.
From biometrics to Dridex in Europe and a fascinating insight into how different nations pay for things online – this week’s security review is a busy one.
The post The security review: Biometrics, Dridex in Europe and online payments appeared first on We Live Security.
![]()
When discussing banking trojans these days, Dridex is the one that everybody seems to be talking about the most. This trojan has inherited the popularity of the ancient Zeus trojan and is one of the biggest threats that we can find right now, in constant evolution to become more efficient.
The post New Dridex campaign achieves high infection ratio in European countries appeared first on We Live Security.
![]()
There’s a big difference between “mostly dead” and “all dead” with film characters … and with malware distributing botnets. The Dridex/Bugat botnet is still slightly alive …
The post Dridex/Bugat botnet is alive, says Miracle Max appeared first on Avira Blog.
The virulent Dridex malware poses a serious threat to online bankers in the UK, according to the National Crime Agency. Internet users urged to be vigilant.
The post UK’s NCA warns online bankers to be wary of Dridex malware appeared first on We Live Security.
![]()
Malware that uses macros as part of its infection method has been around for more than a decade, and was one of the first major techniques to drive changes at software vendors such as Microsoft. The tactic has been making a comeback of late, and Microsoft is seeing a major spike in the volume of […]
Malware authors like to play hide-and-seek. Hiding executable files inside PDFs and Microsoft Office documents then emailing them as attachments are nothing new, but sometimes one layer isn’t enough. This Avast Virus Lab analysis peels back the layers of a new threat.
Malware authors continually surprise us with their creativity. In an effort to trick banking customers into revealing the login credentials for their online account, cycbercrooks are using the trust people have in Microsoft Office to make them execute banking malware on their own computers. Here’s how it works:
Typically, spam emails contain executable files that can harm a victim’s computer and steal private information. In the layered version, they have PDFs or Microsoft Office documents attached that contain a malicious executable file. We recently found an email that had an added layer and decided to analyze the email.
The email, disguised as a financially-related message from a legitimate company, informed the recipient that an invoice was due and had a PDF file attached. Embedded inside the malicious PDF was a Microsoft Office document and simple java script that dropped and executed the DOC file.
![]() Inside the DOC file we found malicious macro code, which users must activate, as the code is disabled by Microsoft Office by default. The code obfuscates DOC files by creating new documents with unique methods names, variable names, and URLs, making it difficult to detect the malicious files.
Inside the DOC file we found malicious macro code, which users must activate, as the code is disabled by Microsoft Office by default. The code obfuscates DOC files by creating new documents with unique methods names, variable names, and URLs, making it difficult to detect the malicious files.
When we analyzed the malicious macro code, we found some hints that helped us with our analysis. In this sample it was a function called MICHEL.
We already knew this function would open the URL with the malicious file, and when we found this function in one of the modules, we were able to find the download path.
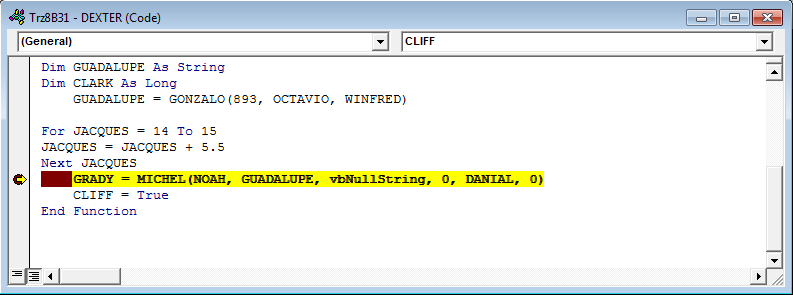
The address is stored as a GUADALUPE variable. The URL is unique for each sample and leads to the download of a malicious PE file.
![]()
The PE file would act as an information stealer, stealing login credentials from banking sites like
Our number 1 recommendation is keep your security software updated. Avast streams hundreds of updates every day to your devices, so you will stay protected. For example, the executable file downloaded by the malicious Microsoft Office document belongs to a banker family evolved from infamous Zeus. This variant is also known as a Dridex Botnet. At the time of writing this post, the botnet is still active, but the malware itself is inactive. Avast detects it as Win32: Pierre-A.
Clever cybercrooks use social engineering to manipulate their victims. Use extreme caution when opening emails related to your finances until you can verify the legitimacy.