As you know, phishing is a technique that involves tricking the user to steal confidential information , passwords, etc, into thinking you are a confidential site.
So far the hackers have used emails to launch this type of attack, but with the widespread use of social media networks and smartphones with internet access, the types of attacking are multiplying.
These emails include a link that takes the user to site known to have a confidential website, but they’re mere mimics with zero confidentiality.
Thus, overconfident users who do not have adequate antivirus protection, could be involved in attacks that are aimed to steal personal data.
And because of the economic crisis which is unfortunately affecting several countries, phishing attacks attracting people with the promise of a great job or an easy way to get money.
The question is … How can we prevent this type of phishing attack?
10 Tips to Prevent Phishing Attacks
1. Learn to Identify Suspected Phishing Emails
There are some qualities that identify an attack through an email:
- They duplicate the image of a real company.
- Copy the name of a company or an actual employee of the company.
- Include sites that are visually similar to a real business.
- Promote gifts, or the loss of an existing account.
2. Check the Source of Information From Incoming Mail
Your bank will never ask you to send your passwords or personal information by mail. Never respond to these questions, and if you have the slightest doubt, call your bank directly for clarification.
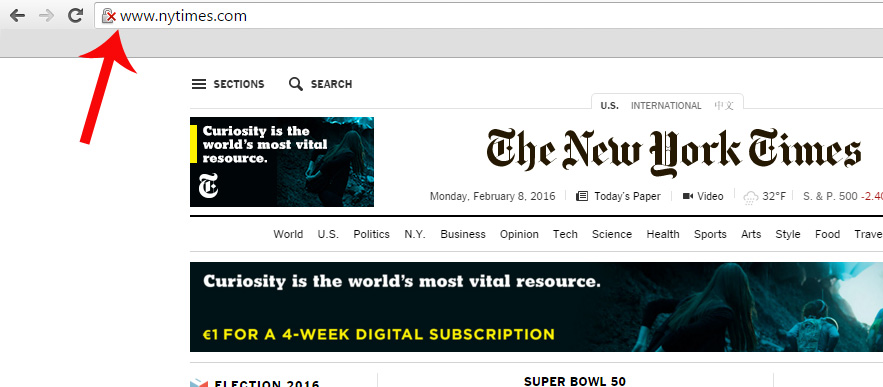
3. Never Go to Your Bank’s Website by Clicking on Links Included in Emails
Do not click on hyperlinks or links attached in the email, as it might direct you to a fraudulent website.
Type in the URL directly into your browser or use bookmarks / favorites if you want to go faster.
4. Enhance the Security of Your Computer
Common sense and good judgement is as vital as keeping your computer protected with a good antivirus to block this type of attack.
In addition, you should always have the most recent update on your operating system and web browsers.
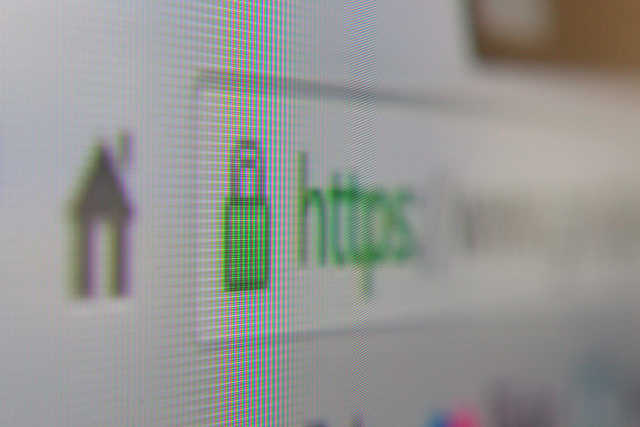
5. Enter Your Sensitive Data in Secure Websites Only
In order for a site to be ‘safe’, it must begin with ‘https://’ and your browser should show an icon of a closed lock.
6. Periodically Check Your Accounts
It never hurts to check your bank accounts periodically to be aware of any irregularities in your online transactions.
7. Phishing Doesn’t Only Pertain to Online Banking
Most phishing attacks are against banks, but can also use any popular website to steal personal data such as eBay, Facebook, PayPal, etc.
8. Phishing Knows All Languages
Phishing knows no boundaries, and can reach you in any language. In general, they’re poorly written or translated, so this may be another indicator that something is wrong.
If you never you go to the Spanish website of your bank, why should your statements now be in this language?
9. Have the Slightest Doubt, Do Not Risk It
The best way to prevent phishing is to consistently reject any email or news that asks you to provide confidential data.
Delete these emails and call your bank to clarify any doubts.
10. Check Back Frequently to Read About the Evolution of Malware
If you want to keep up to date with the latest malware attacks, recommendations or advice to avoid any danger on the net, etc … you can always read our blog or follow us on Twitter and Facebook . Happy to answer any questions you may have!
The post 10 Tips to Prevent Phishing Attacks appeared first on MediaCenter Panda Security.