Until recently it would have been unthinkable to imagine that a simple Barbie doll could pose a threat to data security and information relating to minors, however, more and more toys aimed at children are now connected to the Internet of Things which leaves them vulnerable to attack.
A current example is the new Hello Barbie, recently released by Mattel, which can speak to children – it has up to 8,000 recorded phrases, allowing it to communicate with its owners.
The toy needs to be connected to a Wi-Fi network to send the audio to the servers of ToyTalk (the company responsible for the voice recognition technology), where it is analyzed and a suitable response is chosen. The users, which in this case would be the parents, have to download an application and open an account with ToyTalk to enable the doll to speak.

Mattel claims that the microphone will only activate itself once the related button is pressed, adding that “parents and guardians have control over their children’s information and can manage it via the account”. However, as is the case with other devices, the servers are exposed to a possible cyberattack.
An example of this type of technology’s vulnerability is the recent data leak suffered by VTech, manufacturers of electronic toys for children. The Chinese company sells tablets, mobiles, and baby monitors.
The cybercriminals managed to get data belonging to five million parents and 200,000 children from the company’s servers. This information included names, email addresses, passwords, postal addresses, and thousands of photographs of minors, and even included recordings of the conversations between the toys and their children.
With the growth in electronic toys comes a growth in possible leaks, which has led to national governments taking measures to counteract this. A recent document released by the British government stipulates the areas in which technological fields intelligence and security agencies can investigate, and each of their respective obligations.

According to a report from the BBC, Antony Walker from techUK (an organization that represents more than 850 companies in the UK) has claimed that any device connected to the Internet is at risk of being used as a spying tool.
Walker also raised concern with regards to the danger posed by toys that come equipped with cameras and microphones. “In theory, the manufacturer of those products could be the subject of a warrant to enable equipment interference with those devices”, he added.
The aim of these warnings isn’t to cause panic, nor to put people off purchasing these toys, but rather to raise awareness of the growing risk attached to this type of gift.
The post How kids’ toys are becoming a tool for cybercriminals appeared first on MediaCenter Panda Security.













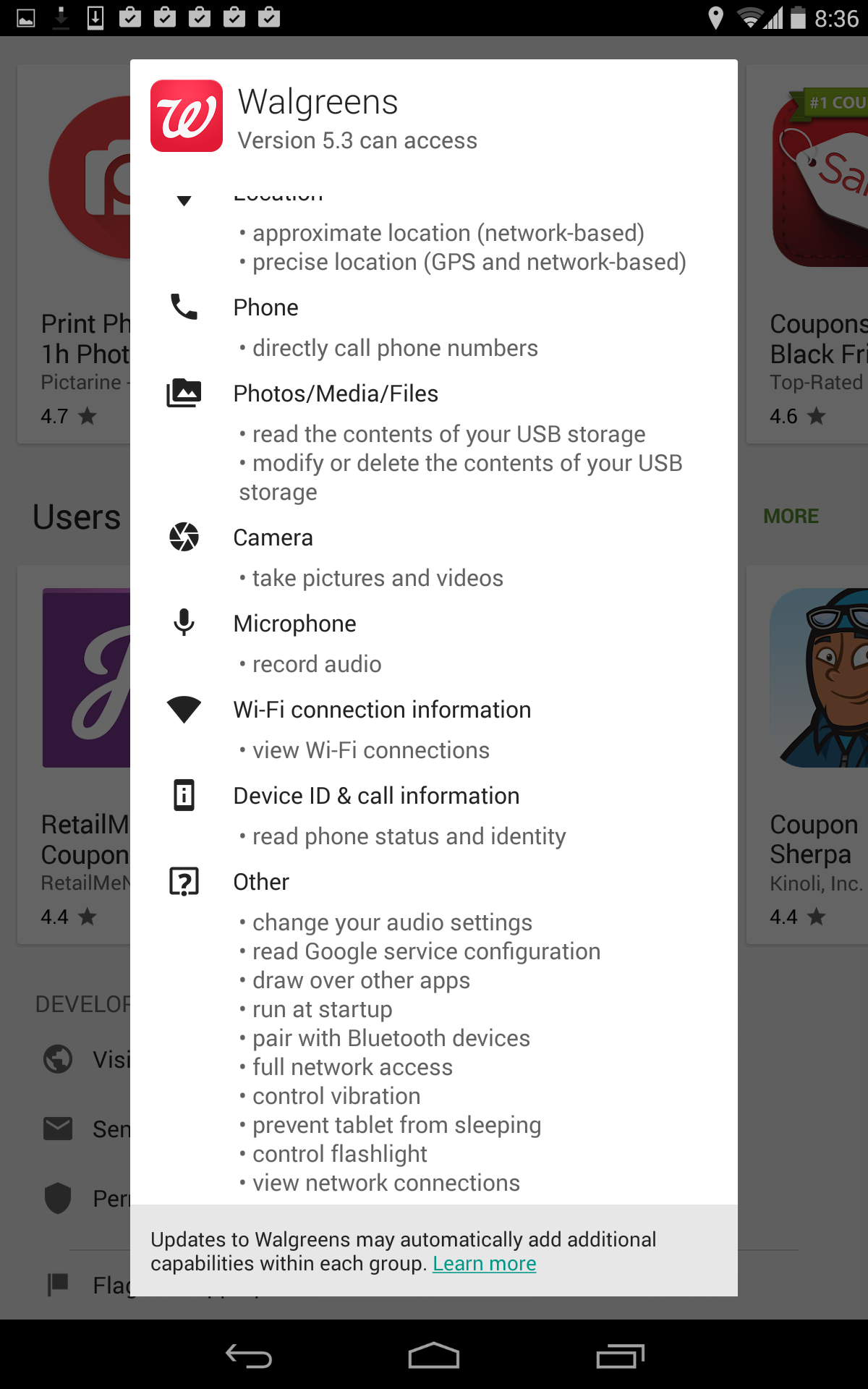
 If you want to choose a shopping app based on the amount of unnecessary permissions it collects then Walgreens is the app for you!
If you want to choose a shopping app based on the amount of unnecessary permissions it collects then Walgreens is the app for you!