This week’s episode of Mr. Robot was an exciting one for us here at Avast – our product made an appearance on the show! In addition to the exploit Avast blocked, there were many other interesting hacks in this week’s episode, which I discussed with Avast security experts, Filip Chytry and Jiri Sejtko.
Minute 7:00: Elliot is in his apartment with Isaac and DJ. Something about Vera’s brother, Isaac, bugs Elliot and what does Elliot do when he is bugged by someone? He hacks them!
Stefanie: We see Elliot once again turn to the Linux distribution, Kali, to hack Isaac’s cell phone. He seems to do this within a matter of seconds, how easy is this to do? Later on, when Elliot visits Vera in prison, we learn what Elliot plans to auto-send information from Isaac’s phone to himself. This seems really intrusive and couldn’t Isaac just get a new phone?
Filip Chytry: This is a more advanced hack and unless Elliot had everything prepped before they entered his apartment, this would taken a lot more time to execute (but this is a TV show, so things sometimes happen faster on TV then they do IRL). The Linux distribution Kali, a popular tool for penetration testing, can be used to plant code on a device. But, Isaac’s phone would have had to be connected to either Elliot’s Wi-Fi network or Elliot could have set up a fake Wi-Fi hotspot using a popular network name like “Starbucks Wi-Fi” or “ATT Wi-Fi”, a Wi-Fi network Isaac’s phone had connected to before and would connect to automatically. Elliot would then use Kali to exploit a vulnerability in Isaac’s phone and plant code to send information from the phone to Elliot’s chosen destination. Since Elliot told Vera about this, Vera could have told Isaac and Isaac could have gotten a new phone, but Isaac was not given a happy end in this episode…
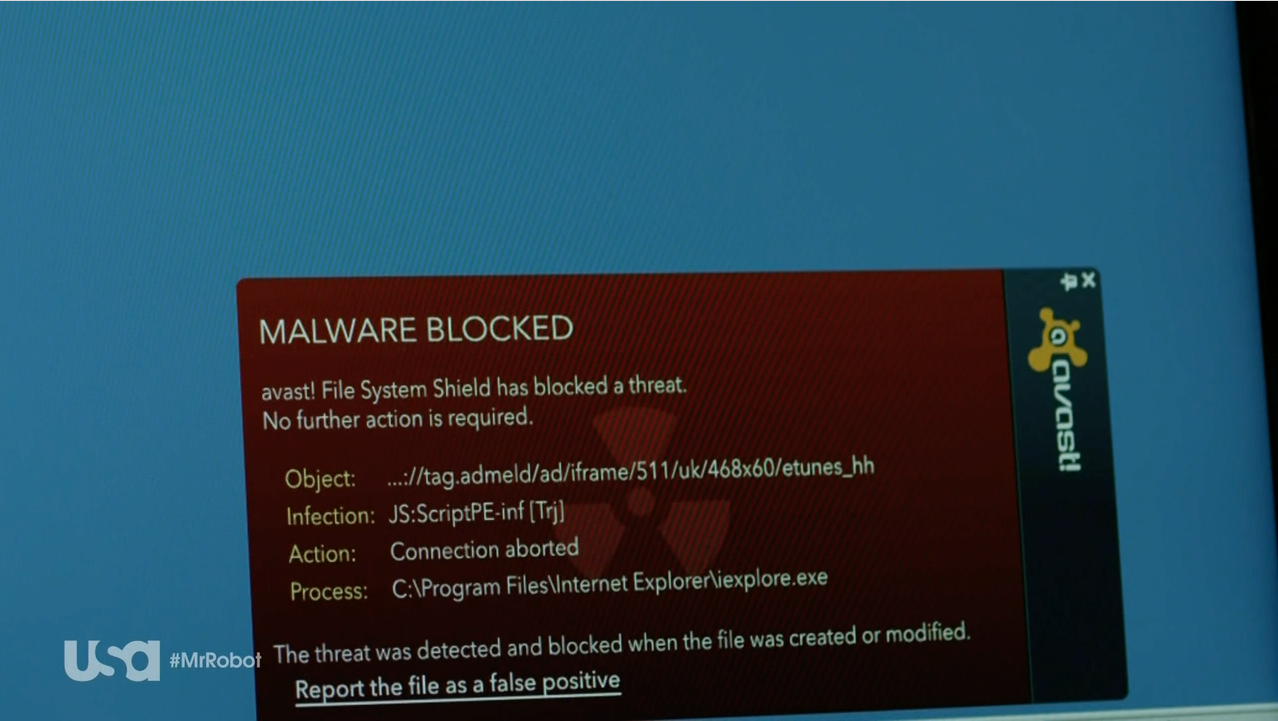
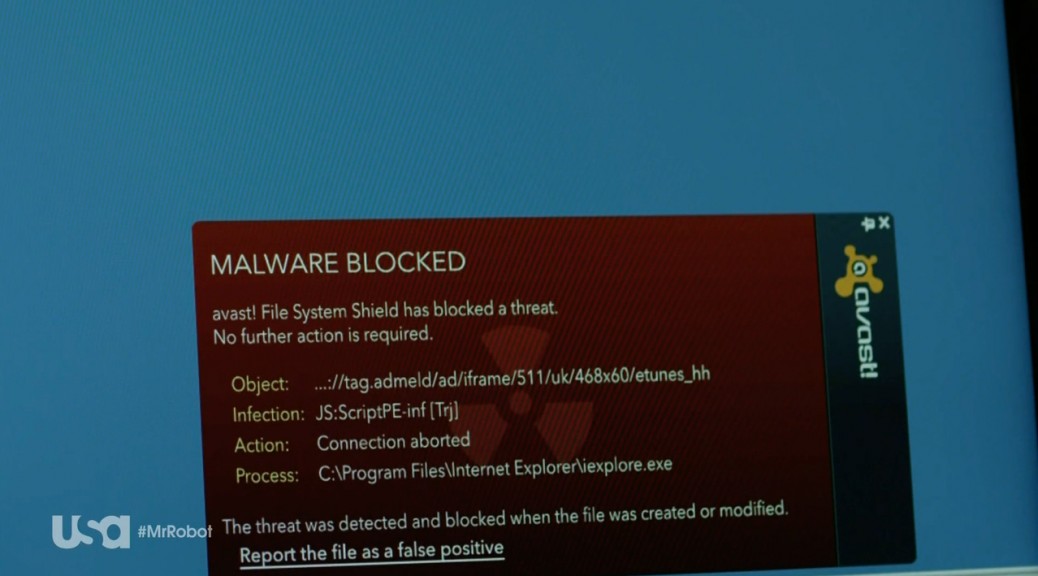
Minute 11:30: Elliott tries to find a way to hack into the prison’s network. Darlene helps him by uploading an exploit onto USB sticks. The USB sticks are branded with E-Corp’s logo, to look trustworthy. She drops the USB sticks on the prison’s parking lot. A police officer takes one of the sticks and inserts it into his work PC. First, a window appears saying “get your free $100 eTunes gift card”, and then a window asking him what his favorite music genre is appears. He clicks through several questions – and then BAM! Avast detects the exploit!

Stefanie: Watching this scene, we couldn’t be prouder. Avast detects an exploit in Mr. Robot, this is so exciting! Taking a closer look at Avast’s warning pop-up, we can see the exploit was a Trojan: JS:ScriptPE-inf (Trj) Is this actually a Trojan that exists or is this made up?
Jiri: This is a real detection. The detection is triggered by an HTML or Javascript file that contains a URL that Avast blocks, as it includes a malicious file. It is, however, hard to say what the URL contained. I would expect it to be some kind of exploit that tries to exploit a vulnerability on the officer’s machine, in order to execute code that would give Elliot access to the prison network.
Minute 31:38: Elliot runs an undetectable activated signal sniffer that will locate any wireless signal in sight on his phone while it is at the prison’s security desk. When Elliot exits the prison, he checks the data retrieved from the sniffer and is disappointed to see that the prison’s network uses WPA2 encryption.
Stefanie: Elliot mentions that WPA2 is “borderline unhackable” and then he mentions a handshake? Is WPA2 encryption really that secure and what handshake is he referring to?
Filip: WPA stands for Wi-Fi Protected Access and WPA2 is WPA’s successor, which uses AES (Advanced Encryption Standard). WPA is the best encryption currently available for Wi-Fi, so when Elliot says it is border line unhackable, he means it! There is one way WPA2 can be hacked, but, as Elliot mentions, it takes a long time to do. When a client connects to an access point, a four-way handshake happens, encrypting messages to confirm that both parties know the so called PSK (pre-shared key) and PMK (pairwise master key), without revealing them. In order to hack a WPA2 protected network, you have to capture and decrypt the authentication handshake. Capturing the handshake can be easy but the decryption can be difficult, depending on the Wi-Fi network’s password complexity.
After Elliot gives up on the idea of hacking into the prison’s Wi-Fi, a police car drives by and automatically connects to his smartphone. He says “The mobile feed on the cameras… I don’t need to hack WPA when there is dedicated 4G”. Later, in minute 35:40, we see Elliot hacking a police patrol car. His plan is to connect to the “patrol car’s bluetooth to run the exploit on the PLC”. He is successful and gives the order “at 9:49, all the cell doors should open”.
Stefanie: What’s a PLC?
Jiri: PLC stands for “programmable logic controller”, it’s a computer usually used in industrial environments. The most famous PLC attack vector is probably Stuxnet, which was designed to monitor Siemens machines in Iranian nuclear facilities and manipulate the centrifuge’s rotor speed.
Stefanie: In the case of Mr. Robot, the PLC is used in the prison to control the locks of the cell doors.
Jiri: Yes, PLC-based systems are heavily used in prisons, there are prisons in the U.S., where PLCs control over 900 doors. Security researchers have mentioned concerns about prison PLC systems’ vulnerabilities already years ago and Sam Esmail, the producer and writer of Mr. Robot, cleverly ties these concerns into the story. Potential exploits are also presented in the open source Metasploit Framework, which is a tool for developing and executing exploit code – so basically, every script kiddie can (ab)use it.
Stefanie: Sounds scary. How could a PLC be protected from an exploit?
Jiri: System administrators should make sure that the PLC firmware and controlling software is patched and always updated. They should also use proper network segmentation to prevent access to the PLC network from other local networks – air gaps – like the one in Mr. Robot, where the PLC could be accessed via patrol car’s laptop. Also, physical media like USB flash disks and mobile phones should be restricted from accessing the PLC.
Stefanie: Sounds pretty simple in a way… Has anyone ever broken out of prison by hacking into the prison’s system?
Filip: There are many ways prisoners can use technology to “hack” themselves out of prison. Earlier this year, a criminal imprisoned in a jail near London, managed to escape the prison using social engineering. He set up a fake web domain that resembled the domain of the court responsible for him. He then used this domain in an email he sent to the prison’s custody inbox, including the message that he should be released. His escape was noticed only three days later, when solicitors were supposed to interview him.
The (cyber)criminal was caught again some time later, but this story shows that a jailbreak via “hack” isn’t that unrealistic in today’s world.

via: USA Networks Mr. Robot airs on Wednesdays at 9/10 central on USA
Thank you Jiri and Filip for taking the time to discuss this week’s Mr. Robot hacks!
What did hack did you find most interesting from the episode? Let us know in the comments below 


![]()

















 Avast for Business
Avast for Business
 nCart
nCart nOffice
nOffice