Have you ever wonder if there is a way of locating your phone in case you lose it or it gets stolen? Well, relax, because the answer is yes! There is a way you can find your phone, how? Here we explain to you three ways of doing it! Keep reading. You have 3 ways of doing it.
How to find your phone
With Panda Mobile Security
Thanks to the mobile and tablet location system in our antivirus for Android, you can recover your device if you lose it!
Panda Mobile Security tracks and displays on a map your lost or stolen tablet or phone so you can find it quickly. You will also be able to block the device and erase all your personal information remotely to prevent others from accessing your most valuable information.
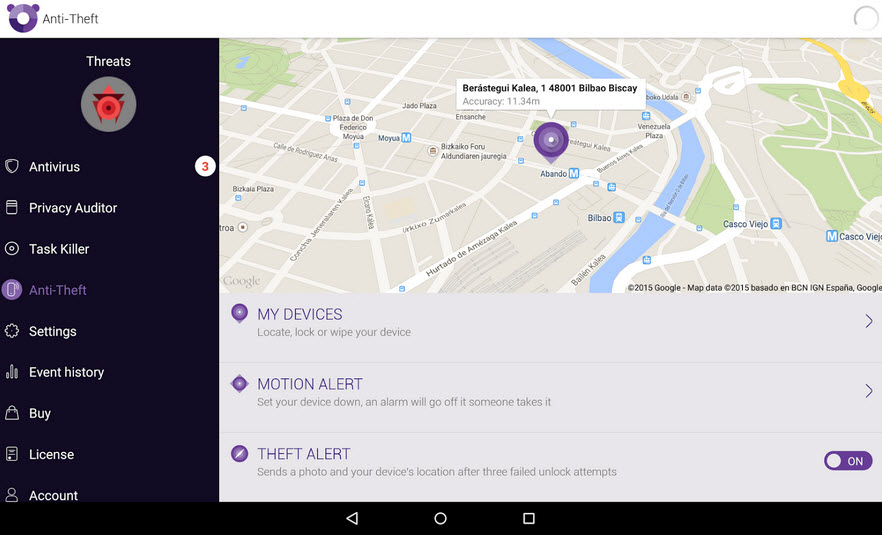
In addition, our service has an antitheft application that protects the user and ensures the phone’s safety. Panda Mobile Security makes a picture of the user and sends it via email together with the device’s location every time the user fails to enter the password.
If the device runs out of battery, Panda Mobile Security will geo-locate it and save this information, so it can be used later if necessary.
You can also use Google…
To find your Android phone or tablet with Google, you must do it through the site in English, since this feature it is only available in this language.
Once you are in the web site you will only need these three magic words: ‘Find my phone’. This Google search will result in a map, which will display your phone’s location with a precision that may vary a few meters, as the service informs.
In addition, if it is nearby but you still can’t find it, Google can make it ring, even if the device is in silence.
And if you have an Apple device: Find my iPhone
If you are an Apple user and you have lost any of your devices, don’t worry! You can find them with iCloud. Don’t know how, just follow this few steps:
- Access your iCloud account or use the Find my iPhone app in another device to locate your iPhone, iPad, iPod touch or Mac on a map.
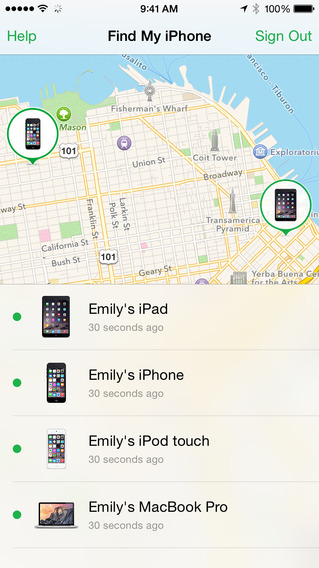
- Using Lost Mode you can track your phone, see where it is and where it has been.
- Once you locate it, you can lock it and send a message with your contact number. So, whoever finds it can call you but can’t access the rest of your information.
- If you think your device has fallen into the wrong hands, you can remotely erase it and restore your iPhone, iPad, iPod touch or Mac to its original settings.
And last but not least…
Phone locators
When we wrote this article we found lots of webs that offer a series of services which they call ‘phone locators’. But what they actually do is take advantage of those users who have lost their phone or tablet.
So, if we use these web pages, in addition to not finding our cell phone, we will waste our time and money. That is why, we recommend you not to trust any web if it asks you for any kind of financial compensation or personal information!
The best thing you can do to find your cell phone is to use official services like iCloud, Google or the feature included in our antivirus for Android.
The post How to find your phone – 3 alternatives to the rescue appeared first on MediaCenter Panda Security.