Gmail recently announced that they have approximately one billion active users per month. That has made it possible for their other services like Android, Maps, YouTube, Chrome, and WhatsApp (owned by Facebook) to become widely popular.
Gmail recently announced that they have approximately one billion active users per month. That has made it possible for their other services like Android, Maps, YouTube, Chrome, and WhatsApp (owned by Facebook) to become widely popular.
Now, Google has another purpose: to make our emails safer. Google, Microsoft, Yahoo, LinkedIn, 1 & 1 Mail and Comcast (the leading provider of cable television in the United States) have joined forces to develop a new email protocol.
These companies have submitted a proposal to improve email security for the Internet Engineering Task Force (IETF), an organization that ensures that the network functions properly. The group of experts from these companies has proposed a new protocol, SMTP STS (Strict Transport Security). But what’s the benefit of making it a standard?
In 1982, the world began using the Simple Mail Transfer Protocol (SMTP). This protocol sent all messages in plain text and did not include measures to prevent a cyber-criminal from intercepting emails. In 2003 they presented SMTP STARTTLS to help improve security. Using this, the SMTP connections are secured by utilizing TLS protocol (Transport Layer Security) to encrypt messages, however, STARTTLS presents a security flaw: this protocol allows messages to be sent even though the server’s identity cannot be verified.
STARTTLS is vulnerable, especially with “man-in-the-middle” attacks, where the cyber-criminal is able to spy on messages sent between the mail’s sender and receiver without them knowing. For example, an attacker could convince the client that the server does not use SSL or could present a fake digital certificate, and by doing so, they could intercept emails.

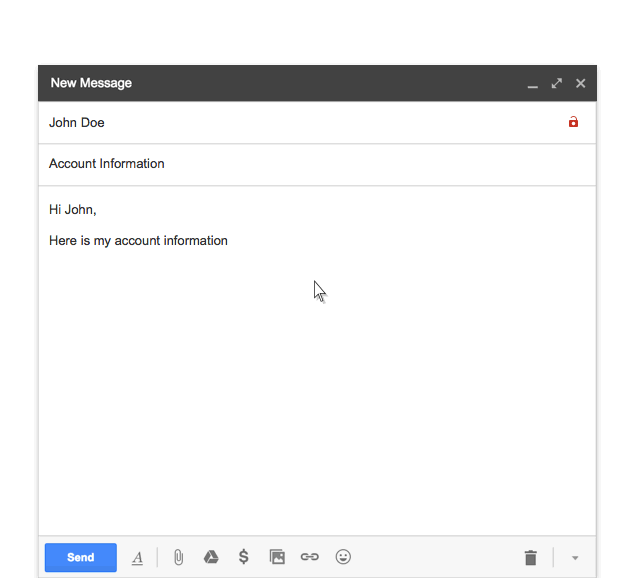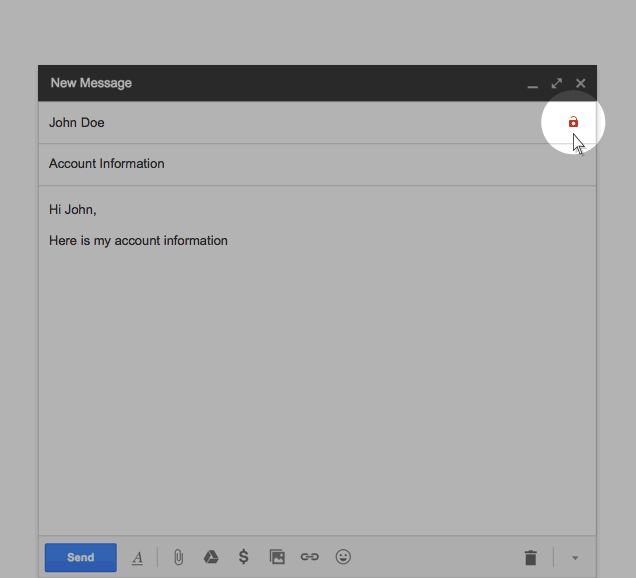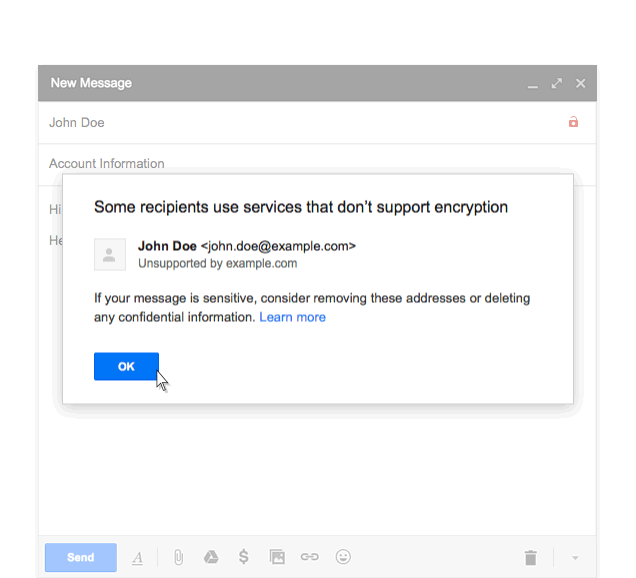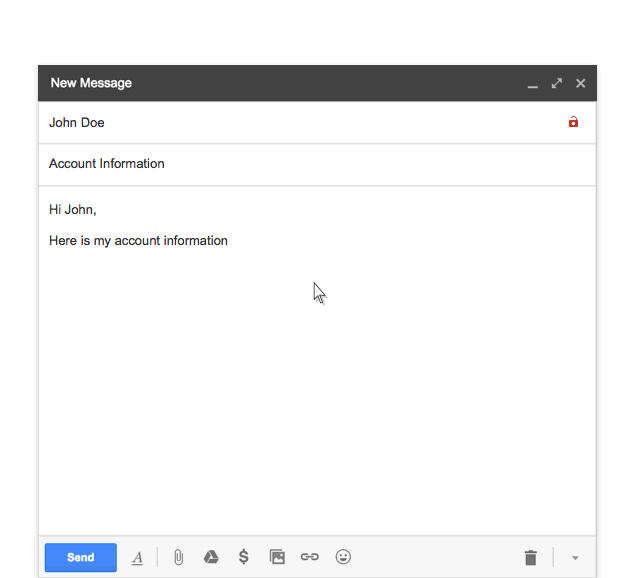
Google just launched the new SMTP STS standard to prevent a cyber-attacker from committing these crimes. With this, all emails are encrypted when sent and no cyber-criminals can spy on the communications channel. This protocol is similar to HTTP Strict Transport Security (HSTS), designed for the server and the web browser to interact using only secure communications.
The new system checks if the recipient uses SMTP STS and if they have a valid and updated certificate of encryption. This ensures that the email is being sent through a secure server. If there is a flaw, it will be detected before the email is even out of the box. In the case of a flaw, the email will not be sent and the sender will be informed why. Using this protocol, we can prevent a cyber-attacker from spying on us.
According to Google’s latest data, 83% of the messages sent from Gmail to other providers, and 70% of those sent from other providers to another service, are already encrypted using TLS. The protocol aims to increase the privacy of our emails. But for now, the new SMTP STS is only a proposal that the IETF has six months to test. The fact that these tech giants have already developed this project suggests that it may be a reality soon.
At the very least, it is always advisable to have some service that protects your company’s mailbox traffic against “malware” and “spam”. Especially since emails contain a large amount of confidential data, even more in the corporate field, making email privacy extremely important.
The post Internet giants join forces to reinforce email security with a new protocol appeared first on Panda Security Mediacenter.
 Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently,
Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently,