It offers greater flexibility for employees and makes them more productive – the work from home revolution, which is being offered by more and more businesses, allows workers to complete their jobs from the comfort of their own home. According to Eurostat, 35% of European businesses currently offer their employees the option of working from home.
Although this percentage is lower in some countries (the EU average is 12%, while in the UK the figure rises to 25%), the trend is clear, and businesses that have yet to embrace it do so for fears over security.
If employees manipulate information from their homes, the companies don’t have any control over the security that is in place, which leads to fears over the loss or theft of data.
The fear is logical as a home environment could be much more vulnerable than a corporate one, where the software of the servers offers greater security guarantees.
The existing risks are, in reality, quite varied and extensive. Data loss can arise in various different forms such as a failure in the system that deletes files that haven’t got a secure copy, the theft of a password, or even the computer itself. This could all result in a thief getting is hands on your company’s confidential information.
That said, working from home doesn’t have to be synonymous with danger. For employers to permit their staff to work from home, they first need to put in place a protocol that establishes rules for working from home or outside of the office.

However, there are some measure that workers can take to avoid any shocks. To start with, the use of remote desktops is a possible solution. With them, it is possible to avoid information theft as they allow the employee to connect directly to the company’s server where the information is stored and where there are automatic security copies made.
Passwords and encryptions
Another key point for making working from home safe is the concern over passwords. The theft of that which the employees uses for accessing the company’s network while working out of the office could end up being disastrous, practically handing a huge amount of data to a cybercriminal.
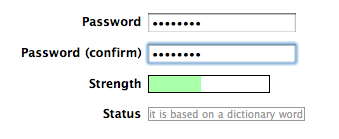
Beyond the corporate server’s passwords, teleworkers that carry out their tasks from home should keep in mind that, when using services and tools on the cloud, that they follow certain steps in creating secure passwords. These including avoiding the use of the same password over and over, making sure to change it frequently, and using a password manager.
That said, passwords aren’t always enough. Although a remote desktop is useful for avoiding the storage of corporate information on a home computer, sometimes it is unavoidable.
In this case, apart from using a safe password, it is important to encrypt confidential information. This way you can avoid a laptop theft resulting in the theft of information. Encrypting archives via the operating system or encrypting the hard drive removes all of this risk.
One way or another, working from home is growing at an unstoppable rate thanks to technology, but it should mean that security has to suffer – the correct technology offers tools so that information isn’t at risk while workers complete their jobs from home.
The post The security risks posed by working from home appeared first on MediaCenter Panda Security.