Hospitals are on the IoT device vanguard revolutionizing patient care, but they are also huge targets for hackers targeting unsecure IoT medical devices.
Tag Archives: Malware
Downloading Pokémon GO Game for Android? Beware! It Could be Malicious…
“Pokémon Go” has become the hottest iPhone and Android game to hit the market in forever with enormous popularity and massive social impact. The app has taken the world by storm since its launch this week.
Nintendo’s new location-based augmented reality game allows players to catch Pokémon in the real life using their device’s camera and is currently only officially available in the United
![]()
Dropping Elephant APT Targets Old Windows Flaws
Dropping Elephant, an advanced persistent threat group, is using old exploits to target unpatched version of Windows in highly effective cyber espionage campaign.
Over 1000 Wendy's Restaurants Hit by Credit Card Hackers
The Popular fast-food restaurant chain Wendy’s on Thursday admitted that a massive cyber attack had hit more than 1,000 of its restaurants across the country.
The burger chain did not speculate how many people may have been affected, though it did confirm that the hackers were able to steal its customers’ credit and debit card information.
The data breach is more than three times bigger
![]()
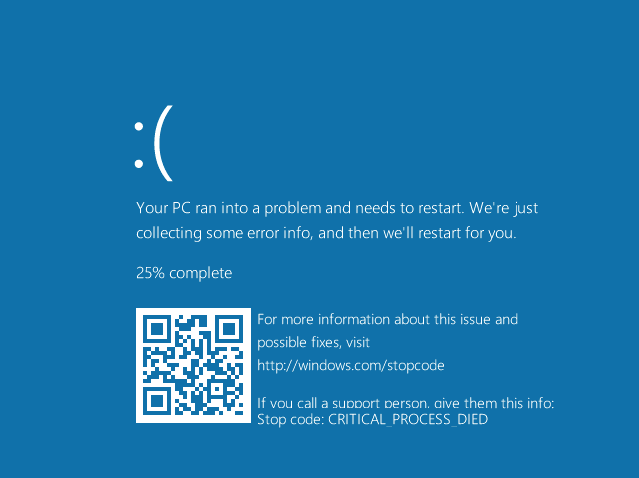
The Blue Screen of Death Gets a New Look
What a terrible feeling we have when the blue screen of death pops up. Dotted with white letters, this uh oh screen can show up unexpectedly on any old Windows-using computer. Seeing this screen will make anyone think, did my computer just DIE?
To fix the problem, the infamous screen of death reads that we should close all programs that could have provoked the issue or restart the computer altogether (using Ctrl+Alt+Supr). If we are lucky, the issue will go away after following these steps, but most of the time it won’t be that easy.
Now, this oh-so-hated blue screen of Windows has had a face-lift, making it just as terrible but a little nicer to look at. The newest version on Windows 10 (out this summer) will display a sad emoticon and a QR code that will send you to a help area once it is scanned.
The bad news is that these two-dimensional codes, or more precisely the links they contain, can be very powerful tools for cybercriminals.
First, a cybercriminal could simulate that your computer has an error, and send your computer a fake “blue screen of death”. Then the criminal could add a QR code with a link that will take you to an unexpected and malicious website that will install drive-by malware on your computer.
If the cybercriminal wants to be very sly, they could design an entire website that looks like an official Microsoft one and use it to phish for log-in information and personal data. Uneducated computer users are the easiest victims for this type of trap.
The QR code that appears on the Screen of Death can be used for phishing or downloading malware onto your computer
But using QR codes to camouflage links is nothing new. The best way to protect yourself from this type of attack is to keep your guard up. Don’t scan a two-dimensional code without knowing where it will take you and if that website is a safe place.
To defend yourself against these kind of attacks, it is essential to have a good antivirus that will detect any kind of phishing or malware that is attempting to download on your computer.
The post The Blue Screen of Death Gets a New Look appeared first on Panda Security Mediacenter.
Over 1000 Wendy’s restaurants hacked – customers’ credit card details stolen
Fast food giant Wendy’s says that it now believes that more than 1000 of its restaurants across the United States have fallen victim to a hacking gang, who used malware to steal customers’ credit and debit card information.
The post Over 1000 Wendy’s restaurants hacked – customers’ credit card details stolen appeared first on We Live Security.
![]()
APT Group ‘Patchwork’ Cuts-and-Pastes a Potent Attack
Researchers discover APT attackers that rummage dark web, GitHub and hidden criminal forums to patch together a high-impact APT.
New OSX/Keydnap malware is hungry for credentials
For the last few weeks, ESET has been investigating OSX/Keydnap, a malware that steals the content of the keychain while maintaining a permanent backdoor.
The post New OSX/Keydnap malware is hungry for credentials appeared first on We Live Security.
![]()
Most Post-Intrusion Cyber Attacks Involve Everyday Admin Tools
Ninety-nine percent of post-intrusion cyberattack activities leverage standard networking, IT administration and other tools as opposed to malware.
Oops! TP-Link forgets to Renew and Loses its Domains Used to Configure Router Settings
To make the configuration of routers easier, hardware vendors instruct users to browse to a domain name rather than numeric IP addresses.
Networking equipment vendor TP-LINK uses either tplinklogin.net or tplinkextender.net for its routers configuration. Although users can also access their router administration panel through local IP address (i.e. 192.168.1.1).
The first domain offered by
![]()