Virtualization aims to totally change how we think of IT altogether. Against the backdrop of VMworld, we take a closer look at the key details.
The post VMworld: When IT grows up appeared first on We Live Security.
![]()
Virtualization aims to totally change how we think of IT altogether. Against the backdrop of VMworld, we take a closer look at the key details.
The post VMworld: When IT grows up appeared first on We Live Security.
![]()
New variants of the notorious Carbanak Trojan have surfaced in Europe and the United States, and researchers say that the malware now has its own proprietary communications protocol and the samples seen so far have been digitally signed. Carbanak has been in use for several years, and researchers at Kaspersky Lab earlier this year revealed the […]
Tiny Banker aka Tinba Trojan made a name for itself targeting banking customers worldwide. The Avast Virus Lab first analyzed the malware found in the Czech Republic reported in this blog post, Tinybanker Trojan targets banking customers. It didn’t take long for the malware to spread globally attacking customers from various banking behemoths such as Bank of America, Wells Fargo, and RBC Royal Bank, which we wrote about in Tiny Banker Trojan targets customers of major banks worldwide.
This time we will write about a campaign targeting customers of Polish financial institutions. The Trojan is spread by email attachments pretending to be pictures. The examples of email headers are shown in the following image.
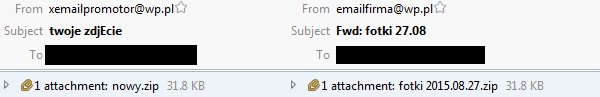
In fact, there are executable files in the zip attachments – IMG-0084(JPEG).JPEG.exe, fotka 1.jpeg.exe. The interesting thing is that the binary looks almost like regular WinObj tool from Systernals, however there are differences: The original version of WinObj has a valid digital signature. The malware doesn’t have any.
The most significant difference is in the payload that replaced the original code. It is the same until a VA 0×414923 is reached where the original code is replaced by a malicious one, as you can see on the following image.
There are some modifications in Tiny Banker including anti-debug tricks, however the encryption remains the same RC4 with a hard-coded password.
Using the RC4 algorithm with the hard-coded password we were able to get the configuration file for the Banker.
The configuration file provided us with information about the targeted financial institutions in Poland.
SHA256
C49EEF5967E6A4A76AEA1950FD298206371B12CD2E00D478270F44B49BB5F157
FA394A41F1BB686AF7D71E9983E1C3C3340FDE70E0D9752D9927DA809B93C920
Avast customers are protected by the following detections:
Win32:Kryptik-PMD [Trj]
Win32:Kryptik-PME [Trj]
Malware spreading by email scams is pretty common. Malware authors use Tiny Banker to target multiple customers of financial institutions around the world. They used a regular binary this time and replaced original code with their payload.
Acknowledgement
This analysis was done collaboratively by David Fiser and Jaromir Horejsi.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()

Chinese jailbroken iPhone users targeted
In what has been called the biggest iPhone hack ever, 250,000 Apple accounts were hijacked. That’s the bad news.
The good news is that most Apple device users are safe. Why? Because the malware dubbed KeyRaider by researchers at Palo Alto Networks, only infects “jailbroken” iOS devices. (there’s that bad news again)
When you jailbreak a device like an iPhone or iPad, it unlocks the device so you can do more with it like customize the look and ringtones, install apps the Apple normally would not allow, and even switch carriers!
The KeyRaider malware entered the jailbroken iPhones and iPads via Cydia, a compatible but unauthorized app store, which allows people to download apps that didn’t meet Apple’s content guidelines onto their devices. The malware intercepts iTunes traffic on the device to steal data like Apple passwords, usernames, and device GUID (“Globally Unique Identifier” which is your ID number similar to your car’s VIN). Users reported that hackers used their stolen Apple accounts to download applications from the official App Store and make in-app purchases without paying. At least one incident of ransomware was reported.
Chinese iPhone users with jailbroken phones where the primary attack target, but researchers also found incidents in 17 other countries including the United States, France, and Russia.
The best way to protect yourself from KeyRaider and similar malware is to keep your iPhone or iPad the way it was intended, that means never jailbreaking your device.
The researchers who discovered this malware offer a service on their website to query whether your Apple account was stolen.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
If you have a ton of VMs sprawling the globe, how do you make them all fast? That’s the subject floating around the show floor at VMworld in SFO this year.
The post VMworld: VM acceleration – how do we get there? appeared first on We Live Security.
![]()
Last week I received an email from our IT Crowd reminding me (and others) to please update our iPhones to the new iOS version 8.4.1 immediately, for security reasons. Apparently, a zero-day sandbox violation from earlier in the year was finally being fixed by Apple with this update – yet Apple’s notification said only “improvements and fixes to Apple Music.”
The post Why Apple security myths pervade appeared first on Avira Blog.
This year VMworld tackles what happens when your VM farm grows up and spawns hundreds or thousands of baby VMs
The post VMworld – Got a ton of VMs? Now what? appeared first on We Live Security.
![]()
CoreBot is new information-stealing malware in the wild with a modular design that could turn the credential-stealing malware into something much worse.
If you own an iPhone and it’s jailbroken you might want to be extra careful when it comes to where you download your apps or the KeyRaider malware might get you. Or your credentials for that matter.
The post KeyRaider Steals More Than 225.000 Apple Accounts appeared first on Avira Blog.
An attack that uses the same path names, Java payloads, and Java exploit as one earlier this summer was found leveraging a fake EFF site.