A culture of cybersecurity is essential in today’s organizations to help ensure that they are able to successfully fend off cyberattacks.
The post Organizations advised to invest in a culture of cybersecurity appeared first on WeLiveSecurity.
![]()
A culture of cybersecurity is essential in today’s organizations to help ensure that they are able to successfully fend off cyberattacks.
The post Organizations advised to invest in a culture of cybersecurity appeared first on WeLiveSecurity.
![]()
 How can you prevent a manufacturing sabotage from becoming an IT disaster? Securing your company’s network with the right protection measures isn’t always enough. Of course you should install an adequate protection system and ensure that your employees use robust passwords. However, there is something that we cannot control: the manufacturing process.
How can you prevent a manufacturing sabotage from becoming an IT disaster? Securing your company’s network with the right protection measures isn’t always enough. Of course you should install an adequate protection system and ensure that your employees use robust passwords. However, there is something that we cannot control: the manufacturing process.
Did you know that your business’s computers can be manipulated during the manufacturing process? A cybercriminal’s network is very sophisticated. In fact, these hackers have accomplices allover the world, including in factories where parts are produced (like microchips). Since the products are tampered with before the computer is finished, no one really suspects that the pieces are infected after they’re installed.
Luckily, manufacturers have discovered a complex solution that can beat this scheme. A new system was proposed by Siddhard Garg, a computer engineering professor at NYU. He believes that for the tightest security the microchips should be strategically manufactured in different phases.
Garg’s proposal makes it so that cybercriminals never know exactly where the piece will be created, making it difficult or impossible to carry out their plans.
Garg’s proposal isn’t a new one. In fact, this idea of distributing the manufacturing process to various factories is already being practiced. However, this professor has gone a step further; his method requires advanced mathematics. Instead of randomly distributing the microchip production, this will ensure the greatest security without heavily increasing the production costs. Garg’s system doesn’t just aim to prevent microchip tampering, it will also stop the production of counterfeit parts that affects both manufacturers and buyers.
With this method, since you aren’t building an entire chip in a same factory, there is no finished design to steal and copy.
The post Can we trust our computers? Many have been tampered with during the manufacturing process. appeared first on Panda Security Mediacenter.
Vera Bradley has notified its customers of a data breach, explaining that it had launched an investigation last month into a “payment card incident”.
The post Vera Bradley alerts customers to data breach appeared first on WeLiveSecurity.
![]()
NHS hospitals in England are increasingly being targeted with ransomware attacks, according to an investigation by the i newspaper
The post NHS increasingly being targeted by ransomware attacks appeared first on WeLiveSecurity.
![]()

This ransomware’s initial infection vector occurs when it’s sent/received through Phishing campaigns.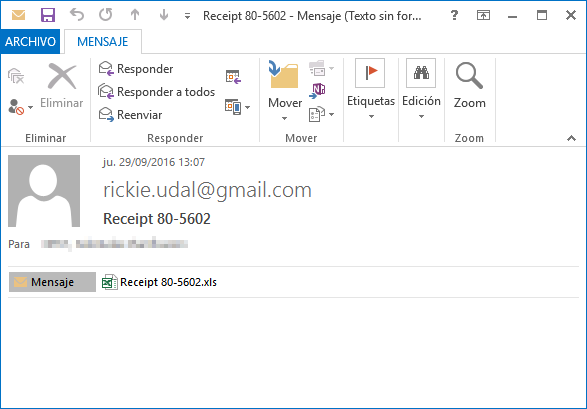
First, the user receives an email with the malicious file in zip format, giving the illusion it is a zip, but in this case, the user also receives some type of invoice; this varies depending on the message received or the name of the file. On this occasion, the received file has the following name: Receipt 80-5602.zip, as seen in the screen capture.
In this compromised file you will find a Microsoft Office document, or more specifically, an Excel with the extension “.xls” containing macros (codes are in Visual Basic Script)
By defect, unless we have the macro execution forced in Excel, the damaged code will not automatically run, unless, an advertisement appears indicating that the document contains macros, as demonstrated in the second screen capture.
The basic feature of this macro is to use the “dropper”, what we mean is, download and execute the other binary file, in this case a file encrypter or ransomware; although it could have been another malicious program like RATs, backdoors, bots, etc.
In this case, as with droppers, the file (or payload) runs on a remote server when executed.
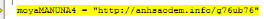
Once the macro is executed, it is now in charge of taking the next steps: downloading and deciphering the remote file that is encrypted, and afterwards, ejecting it.
If we look at the name of the file running from the macro, or its command-line execution, we will see that the ransomware comes by DLL format; this has become increasingly more common. In addition, it requires that an export is indicated to operate, in this case “qwerty”, as shown in the following screen shot:
Why do it this way? Simply because a lot of systems that update the malware analysis (sandboxes) have problems when they execute programs/codes/libraries that require parameters, that are sometimes unknown.
Once encrypted, this library’s MD5: 586aaaaf464be3a4598905b5f0587590
Finally, from PandaLabs we would like to give you the following advice: if you don’t want to have an unwanted surprise, when you receive Office documents from unknown senders do not click the button that says “activate macros”. Lastly, make sure your antivirus solutions and systems are always up-to-date!
The post Tales from Ransomwhere: Macros & Ransomware(s) appeared first on Panda Security Mediacenter.
Individuals are demonstrating security fatigue when it comes to protecting themselves online, increasing their risk of being compromised by a cyberattack.
The post Security fatigue is preventing us from being safe online appeared first on WeLiveSecurity.
![]()
 There is a growing awareness of cybersecurity within companies, but are these companies taking action to improve their security? As seen in a recent study, 750 IT security decision-makers worldwide were surveyed to see whether they are “learning and applying lessons from high-profile cyber-attacks”, and if it influences their security priorities and decisions.
There is a growing awareness of cybersecurity within companies, but are these companies taking action to improve their security? As seen in a recent study, 750 IT security decision-makers worldwide were surveyed to see whether they are “learning and applying lessons from high-profile cyber-attacks”, and if it influences their security priorities and decisions.
The study examined the contradictory situation that is currently present in a number of global businesses. On a positive note, 79% of those surveyed said that they learned their lesson after seeing cyberattacks jeopardize the IT security in other companies, and 55% confirmed that they have changed the way they manage corporate accounts in order to adapt to the current cybersecurity climate and avoid unnecessary risks.
Nevertheless, the survey also exposes a very different reality. Far different from those who are complying with security procedures, 40% of the survey’s participants stated that they just use a Word document or worksheet to manage their company’s credentials and 28% stated that they use a shared server or a USB stick, for the same purpose. What is obvious is that IT security is absent in almost half of the 750 businesses in the survey.
Of course the previously mentioned storage methods are all susceptible of suffering a cyberattack, especially if they fall into the hands of someone with the right know-how, but they can also be leaked by the company’s own employees. A Word document makes private information accessible for any employee in the company.
To ensure that employees only use their own password, companies should use a password manager that will also protect their company’s devices. This will also help keep documents and devices, like a Word document or USB memory stick that stores passwords, safe from a cyberattack or infection.
In terms of cybersecurity, there is still a long way to go in the business environment. IT security should be a priority. Although, 95% of these organizations have a plan in place in case of IT emergencies, only 45% of them periodically check that they are functioning properly.
Despite their carelessness, 68 % of those surveyed claim that their greatest concern and challenge is the data theft of their customers (but this percentage does not correspond with the cybersecurity mechanisms implemented by IT security heads).
The post Almost half of companies save employee passwords in Word documents appeared first on Panda Security Mediacenter.
The UK’s Information Commissioner’s Office (ICO) hits TalkTalk with record fine for failing to take basic security measures to protect customer information.
The post TalkTalk receives record fine for security failings that resulted in 2015 cyberattack appeared first on WeLiveSecurity.
![]()
Some users of the ad-supported music streaming service Spotify Free got more hits than they bargained for, according to numerous reports.
The post Spotify Free hits sour note with infected ads appeared first on WeLiveSecurity.
![]()
Consistent and relentless DDoS attacks are causing “real damage” to organizations around the world, with the number of affected enterprises on the rise.
The post DDoS attacks ‘consistent, relentless and damaging’ to organizations appeared first on WeLiveSecurity.
![]()