Security researchers have identified a serious vulnerability in an open-source library of code that is known as GNU C Library (glibc).
The post Major vulnerability found in GNU C Library appeared first on We Live Security.
![]()
Security researchers have identified a serious vulnerability in an open-source library of code that is known as GNU C Library (glibc).
The post Major vulnerability found in GNU C Library appeared first on We Live Security.
![]()
The hacktivist group Anonymous has released close to 18GB worth of sensitive data from Turkey’s national police database, according to reports.
The post Anonymous leaks 18GB worth of data belonging to Turkey’s national police force appeared first on We Live Security.
![]()
If you see this ad and suddenly want to take your iPhone back in time to January 1, 1970… don’t do it!
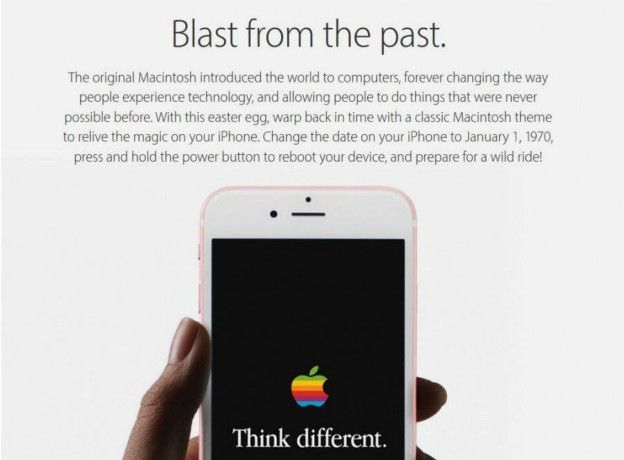
The website 4chan, known for its memes, has shared a joke which claims that if you change the date on your iPhone to January 1, 1970 that the device’s interface will change to Apple’s vintage style. As you can imagine, this would likely render your iPhone completely unusable.
Apple has also stated, via its technical support team, that “manually changing the date on your iOS device to 1970 or before could make it impossible to restart your device”. Also, the company has promised that this problem will be solved with the next software update.
So, what can you do if you’ve already changed the date? Allow the battery to run out until the phone automatically shuts down, allowing for the phone to return to its normal state.
The post Be careful with 1970! It could shut down your iPhone forever! appeared first on MediaCenter Panda Security.
VTech has relaunched its online service Learning Lodge, but appears to have shirked responsibility regarding future data breaches.
The post VTech warns users that sensitive information ‘may not be secure’ appeared first on We Live Security.
![]()
A hospital in the US is still unable to fully access it computer system, over a week after cybercriminals launched a ransomware attack.
The post US hospital hit with ’random’ ransomware attack appeared first on We Live Security.
![]()

In the past few weeks the website Football leaks has been publishing contracts relating to signings and transfers of football players from the world’s top leagues. While some accuse the people behind this page of hacking and document theft, they themselves have assured that they haven’t, in any moment, hacked anyone and that they actually have their own source who provides them with the information.
What’s certain is that when it comes to stealing information from a company, who has it easier than an employee of said company – they have knowledge of the systems, where information is stored, etc. Keep in mind that the majority of security practices are designed to protect a company from an external attacker, via perimeter protection and with an antivirus on the network’s computers.
Football Leaks and EDR protection
However, it isn’t common that they have more advanced security systems such as EDR (Endpoint Detection and Response), which allows them to have total control of what is running on the network, who is accessing certain documents, at what time, and what they end up doing with them. It is obvious that even though they want to invest in security solutions, nobody can guarantee that in no moment will we be compromised.
For this, EDR are the ideal solution – on one hand they offer a greater protection and control as regards what happens on our network, allowing us to know what is happening in real time, and give us valuable information. For example, if we have vulnerable programs – ones that haven’t been updated – that are running. On the other hand it gives us forensic information which allows us to investigate what happened when there is a security breach. This final point is what is really valuable.
Looking back at the case of Football Leaks, where confidential documents have been leaked, we see that these documents are in the possession of the clubs who make the contracts, the players who sign them, and any intermediary. If the clubs had this type of solution, it would be relatively easy to guess who accessed the documents, from where, and if there were any copies made. They could even know if other documents had been compromised.
The value that it offers is clear, however, the majority of companies focus their security spending on preventative measures. This Football Leaks case may just force businesses in this sector (football teams, federations, official organizations, etc.) to go beyond this and adopt the necessary measures to avoid this happening again, as they will have all of the information available should a similar event occur.
These steps aren’t very different to what businesses who already take their security seriously already do, such as banks and energy companies.
The post Football leaks posing a worry to security for the football world appeared first on MediaCenter Panda Security.
The UK government should make ‘malicious data breaches’ a criminal offence, according to a new report from the Science and Technology Committee.
The post Calls from the UK to make ‘malicious data breaches’ a criminal offence appeared first on We Live Security.
![]()
More and more business decision makers in the UK consider cyberattacks to be the greatest threat to their enterprise, according to a new study.
The post UK business decision makers see cyberattacks as their great nemesis appeared first on We Live Security.
![]()
A new e-learning tool has been launched in the UK to help HR professionals effectively deal with cybersecurity issues in the British workplace.
The post Cybersecurity e-learning course launches in the UK for HR staff appeared first on We Live Security.
![]()
A 17-year-old student in American has been arrested and charged with illegally accessing government computers, months after the data breach took place.
The post Student arrested for grade changing school data breach appeared first on We Live Security.
![]()