After more than a year of legal wrangling, the federal government has agreed to hand over its policy on vulnerability use and disclosure. The government had said that the policy was classified and too sensitive to release, but relented late last week and sent the document to the EFF, albeit a heavily redacted version. Know as […]
Tag Archives: NSA
AT&T Facilitated NSA Surveillance Efforts, Reports
Published reports say that AT&T was the National Security Agency’s primary telecommunications partner and facilitated much of its surveillance efforts around telephone and Internet traffic collection.
NSA Says It Will End Access to 215 Records in November
The National Security Agency says that once its legal authority to conduct Section 215 bulk telephone surveillance ends on Nov. 29, its analysts no longer will be allowed to access the database that holds all of the collected Section 215 records. In May, an appeals court ruled that bulk telephone metadata collection as performed by […]
VUPEN Launches New Zero-Day Acquisition Firm Zerodium
In the weeks since the Hacking Team breach, the spotlight has shone squarely on the small and often shadowy companies that are in the business of buying and selling exploits nd vulnerabilities. One such company, Netragard, this week decided to get out of that business after its dealings with Hacking Team were exposed. But now […]
Weekend wrap-up: Cyber security news from Avast
Here’s your wrap up of security and privacy related news from the June 17 – 27 posts on the Avast blog:
 It’s summertime in the Northern Hemisphere and many people are going on or planning their vacation. Beware of fake vacation packages and beautiful rental properties that are not as they seem. These Vacation scams can ruin your holiday, so read up before you become a victim.
It’s summertime in the Northern Hemisphere and many people are going on or planning their vacation. Beware of fake vacation packages and beautiful rental properties that are not as they seem. These Vacation scams can ruin your holiday, so read up before you become a victim.
 More than 600 million Samsung phones were reported to be at risk because of a vulnerability found in the keyboard app SwiftKey. The best way to protect yourself is to use a virtual private network (VPN) when using an unsecured Wi-Fi hotspot. If you have a Samsung S6, S5, or S4, you need to read Samsung phones vulnerable to hacker attack via keyboard update.
More than 600 million Samsung phones were reported to be at risk because of a vulnerability found in the keyboard app SwiftKey. The best way to protect yourself is to use a virtual private network (VPN) when using an unsecured Wi-Fi hotspot. If you have a Samsung S6, S5, or S4, you need to read Samsung phones vulnerable to hacker attack via keyboard update.
 As we learned from the Hola VPN service revelations, any old VPN service will not do. Hola was selling their users’ bandwidth and installing and running code on their devices without their knowledge or permission. Find out the details in Hola, Hola VPN users, you may have been part of a botnet!, and please share with an Hola user.
As we learned from the Hola VPN service revelations, any old VPN service will not do. Hola was selling their users’ bandwidth and installing and running code on their devices without their knowledge or permission. Find out the details in Hola, Hola VPN users, you may have been part of a botnet!, and please share with an Hola user.
 Mobile developer Martin Banas, attended Apple’s Worldwide Developers Conference in San Francisco. Besides spending lots of time standing in lines, he enjoyed meeting other developers and hearing the latest news about OS X El Capitan and Apple Pay. Weren’t able to attend, bit wish you could have? Martin’s conference report, Looking back at WWDC 2015, describes the event.
Mobile developer Martin Banas, attended Apple’s Worldwide Developers Conference in San Francisco. Besides spending lots of time standing in lines, he enjoyed meeting other developers and hearing the latest news about OS X El Capitan and Apple Pay. Weren’t able to attend, bit wish you could have? Martin’s conference report, Looking back at WWDC 2015, describes the event.

Remember the iCloud celebrity photo hack? There have been many theories bandied about since nude photos of female celebrities were posted on the web. We add our own two cents into the conversation. Avast security researcher Philip Chytry explains what he thinks the origin and motivation behind the hack was in iCloud celebrity photo hack: What’s happening?!

Major cybercrooks taken down
While the cybercrooks behind the iCloud hack have not been discovered, authorities had big wins this past week in other areas. The author and distributor of Blackshades malware was sentenced to nearly five years in a New York prison. A major cybercriminal organization responsible for banking Trojans Zeus and SpyEye was taken down. Read Businessman hackers brought down in USA and Europe.
 More from the Edward Snowden files. It was revealed this week that U.S. and U.K. spy agencies were attempting to reverse engineer major antivirus companies software, including Avast’s. CEO Vince Steckler spoke to RT News about government spying in the computer age. You can read the article, Avast CEO speaks out about U.S. and U.K. spy agencies, and watch the interview here.
More from the Edward Snowden files. It was revealed this week that U.S. and U.K. spy agencies were attempting to reverse engineer major antivirus companies software, including Avast’s. CEO Vince Steckler spoke to RT News about government spying in the computer age. You can read the article, Avast CEO speaks out about U.S. and U.K. spy agencies, and watch the interview here.
 And if the real world of cybercrime is not enough, our favorite new show of the summer Mr. Robot debuted on the USA Network this past week. We excitedly watched the first episode then talked to Avast security expert, Pedram Amini, to find out Are the hacks on Mr. Robot real? or just Hollywood magic.
And if the real world of cybercrime is not enough, our favorite new show of the summer Mr. Robot debuted on the USA Network this past week. We excitedly watched the first episode then talked to Avast security expert, Pedram Amini, to find out Are the hacks on Mr. Robot real? or just Hollywood magic.
![]()
Avast CEO speaks out about U.S. and U.K. spy agencies
For as long as there have been governments, there have been spy agencies, and for as long as there have been spy agencies, they’ve done spying. Spy agencies are always looking for ways to get information. Information is valuable, always has been, always will be. ~Avast CEO Vince Steckler
New documents from the many that were leaked by former US intelligence analyst Edward Snowden were published this week in The Intercept. They reveal that the U.S.’s National Security Agency (NSA) and its British counterpart, Government Communications Headquarters (GCHQ), spied on security companies including Avast, AVG, Kaspersky Lab, and Antiy. The spy agencies seem to be targeting non-American security companies; Avast and AVG are based in Prague, Czech Republic; Kaspersky is based in Moscow, Russia; and Antiy is Chinese. Together, these companies have nearly a billion users. No U.S. or U.K. -based companies were included in the list.
“Geopolitically, it makes sense that the NSA and GCHQ are targeting products that are prevalently used by foreign governments, like Kaspersky in Russia or CheckPoint in Israel,” said Steckler in an interview with RT News. “On the flip side, Russian or Chinese spy agencies may be similarly targeting products that the American government heavily uses, for example Symantec and McAfee. We’re hearing just one side of the story.”
Reportedly, the NSA and GCHQ experts reverse engineered the antivirus software in order to exploit it and prevent detection of their own activities.
“It is difficult to tell if the NSA, the GCHQ, or other government agencies have ever tried to reverse engineer our software,” said Steckler. “Even if they did, they would only be able to do so on the client side, which includes simple pattern detection. However, they could not reverse engineer our backend, which includes our sophisticated machine-learning classification.”
The documents also say that the organizations recommended monitoring customers who reported malware “to see if they’re into more nefarious activity.”
While some companies most likely partner with the governments in their home countries, that’s not something Avast does.
“The fact that the NSA may be targeting us – while some major U.S. and British security companies are left out from their list proves that we don’t work with the NSA and GCHQ,” said Steckler. “Ones not on the list quite likely provide their source code and thus there is no need to reverse engineer. Our commitment to our customers is to provide protection from all forms of spying.”
Mr. Steckler spoke to RT News, a Russian television network, about the new revelations. Watch the interview now,
![]()
NIST Drops Weak Dual_EC RNG From Official Recommendations
NIST officially has removed the controversial and compromised Dual_EC_DRBG from its list of recommended algorithms for generating random numbers.
We Focus on Customers, Others Play Dirty Tricks
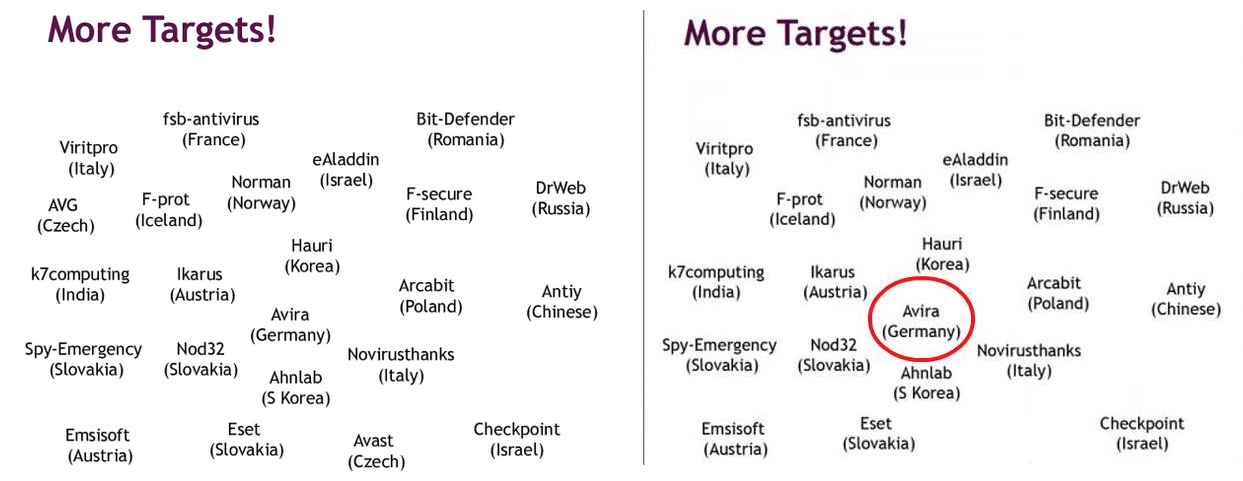
Our blogpost from a few days ago, NSA and GCHQ Have Been Spying on Antivirus Companies, contained our response to recent revelations that the NSA and GCHQ had been targeting antivirus vendors located outside the US and UK. The original story was published by The Intercept, and contained an image from a PowerPoint presentation listing all the potential targets which included Avira, AVAST, and AVG, among others.
We then issued our blog post indicating that our role as a security company is to keep intruders out – even if they might be governments. So far, so good.
Yesterday though, it was brought to our attention that a German website had published an article telling readers that Avira has been attacked by the NSA and that they should instead download AVAST, AVG, or G-Data, because they are more secure. This in itself is not an uncommon tactic and definitely no reason to go ahead and write a blog post – if it would have ended here. Which it didn’t: both AVAST and AVG have been removed from the list of targets (we’re not sure why, but perhaps to give the article more gravitas …)
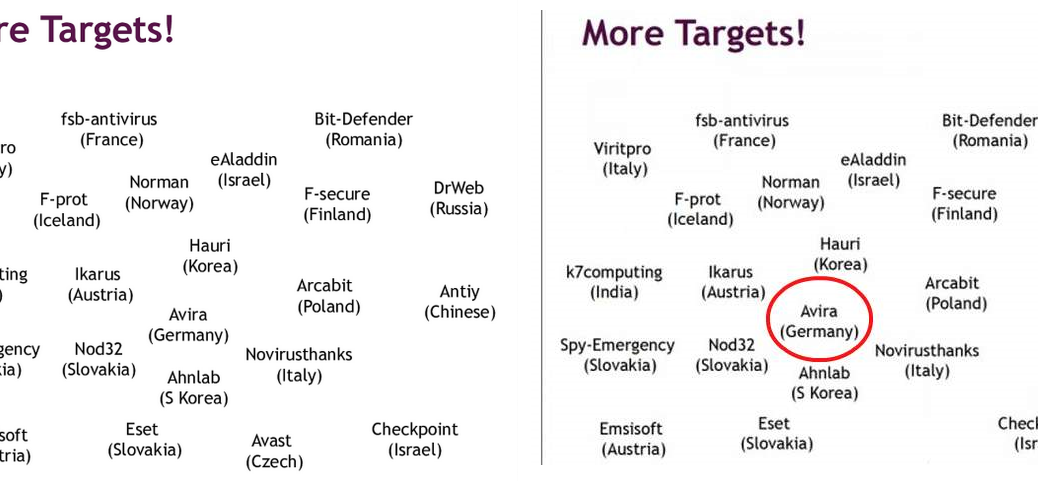
Can you spot the difference?
Original from The Intercept (left) / Falsified image from freeware.de (right)
As you can see in the version reported by freeware.de, only Avira has been carefully encircled, while both AVG and AVAST have been removed.
Who is behind this? We are not sure, but we want our customers to be aware that this information presented is false.
The post We Focus on Customers, Others Play Dirty Tricks appeared first on Avira Blog.
Facebook Hires Ex-Yahoo CISO Alex Stamos
Facebook has hired away the top security executive at Yahoo, Alex Stamos, to become the company’s new CSO. Stamos said Wednesday that he is joining Facebook because he believes the company is in the best position to address some of the large security challenges facing users and companies right now. “There is no company in […]
NSA and GCHQ Have Been Spying on Antivirus Companies
While not the main target of the operation, Avira was nonetheless mentioned together with several other antivirus and security firms as being at least a target of interest (It’s noteworthy that none of the targets were US or UK companies). Since the revelation we have received various requests vis-à-vis our position and capabilities regarding this affair. We are of course more than happy to share our thoughts with you.
“Avira has frequently seen efforts by governments to write malicious software that attempts to prevent, circumvent, or disable our software from protecting our users. The goal is always the same: installing their programs on the computer users’ systems without detection. These tactics are used by malware authors of all kinds, not just governments.
We at Avira are constantly improving our defense and detection mechanisms to avoid such manipulation. We also use various other systems and utilities to detect such efforts, outside of our own products. Whether a government-funded malware writer, mafia, friend or enemy, the exploitation of applications is something that we are determined to prevent from happening,” says Travis Witteveen, Chief Executive Officer of Avira.
Let’s also not forget that Avira is a founding member of IT Security made in Germany and we pride ourselves in committing, among other things, to:
- Exclusively provide IT security solutions no other third party can access (no backdoors!).
- Offer products that do not cause the transmission of crypto keys, parts of keys or access recognition.
- Eliminate vulnerabilities or avoidance methods for access control systems as fast as possible once detected.
Avira will always strive to keep those commitments, be it against your run-of-the-mill malware or attempts by governments to obtain information.
The post NSA and GCHQ Have Been Spying on Antivirus Companies appeared first on Avira Blog.