Turning Security Intelligence into Protection: Kaspersky Lab Launches Anti Targeted Attack Platform and New Security Services
Tag Archives: Press Releases
Kaspersky Lab Announces its Advanced Solution to Detect Targeted Attacks and a New Range of Security Intelligence Services
Kaspersky Lab Announces its Advanced Solution to Detect Targeted Attacks and a New Range of Security Intelligence Services
Panda Security launches its Practical Security Guide for avoiding cyberextortion in businesses

Security in large companies is one of the most important factors in avoiding extortion on the corporate network by cybercriminals.
This is why Panda Security has launched its Practical Security Guide for avoiding cyberextortion, in which it states that Spanish companies are the ones that suffer the highest rate of data theft in Europe. It also states that in the coming year, Spain will become the European country with the highest rate of cyberattacks.
Ciberextortion: a limitless threat
In recent years, the massive growth in cyberattacks has led to companies devoting more time and resources to combatting the problem, and finding a security solution that guarantees greater control of their files.
The majority of attacks that use this type of extortion have different origins: 39% come from insecure or fraudulent websites, 23% from programs downloaded from the Internet, and 19% come from infected emails or attached documents.
The cyberextortion process starts by blackmailing the victim so as they pay up, thus avoiding the kidnapping of their files. Once the user agree, the payment is completed with Bitcoins. Later, the victim receives an email with the code to decrypt the data, although many times payment doesn’t guarantee that the company won’t become a victim again in the future.
Type of malware: How do they affect the companies?
Businesses are considered the main target of this type of malware, as its aim is to cause as much damage as possible:
- Ramsonware, the most common are Cryptolocker, Cryptowall, and CoinVault, which target the integrity of the file stored on the PC
- APT (Advanced Persistent Threat) is a system that manages and controls the security of the computer from inside
- Exploit takes advantage of a security flaw in communication protocols between computers
- Phising, creates a false URL to steal bank details and identity
- Trojan, installs different applications that allow hackers to control the computer
- Worm, is able to infect all computers
Panda Security’s 5 tips for avoiding cyberextortion
- Advise your users: keep them up to date with the risks that are associated with not having a good security solution
- Set out rules for online use at work: assign a series of rules that control the reputation of websites that access is granted to.
- Design a solution to your needs: make sure you have the right solution for your business, and keep it updated.
- Establish protocols: control installation and running of software. Also, examine what applications have been installed periodically.
- Always update: set out an update policy and block certain applications on your computers.
The post Panda Security launches its Practical Security Guide for avoiding cyberextortion in businesses appeared first on MediaCenter Panda Security.
Kaspersky Lab Solutions Triumph in 2015 AV-Test Awards for Performance, Usability and Repair
Kaspersky Lab Solutions Triumph in 2015 AV-Test Awards for Performance, Usability and Repair
Kaspersky Lab Releases New Kaspersky Internet Security for Mac with More Privacy Features
Kaspersky Lab Releases New Kaspersky Internet Security for Mac with More Privacy Features
Kaspersky Lab helps to disrupt the activity of the Lazarus Group responsible for multiple devastating cyber-attacks
Kaspersky Lab helps to disrupt the activity of the Lazarus Group responsible for multiple devastating cyber-attacks
Kaspersky Lab’s Leslie Bois Recognized as CRN 2016 Channel Chief
Kaspersky Lab’s Leslie Bois Recognized as CRN 2016 Channel Chief
Acecard Trojan: Android Users of Over 30 Banking and Payment Apps at Risk
Acecard Trojan: Android Users of Over 30 Banking and Payment Apps at Risk
27% of all recorded malware appeared in 2015

PandaLabs, the laboratory of Panda Security, both detected and neutralized more than 84 million new malware samples throughout 2015. This is nine million more than the year previous, according to the corresponding data. The figure means that there were 230,000 new malware samples produced daily over the course of the year.
Last year saw the greatest number of cyberattacks recorded around the world, with a total of 304 million samples, which means that more than a quarter of all malware samples ever recorded were produced in 2015 (27.63%).
It was also a difficult year for certain multinational companies who suffered large scale data theft and interference on their IT systems.
“We predict that the amount of malware created by cybercriminals will continue to grow”, says Luis Corrons, Technical Director of PandaLabs, “we also can’t forget that the creation of millions of Trojans and other threats corresponds to the cybercriminals’ needs to infect as many users as possible in order to get more money”.
Most powerful malware of 2015: Trojans and PUPs.
In 2015 we saw that Trojans, PUPs (Potentially Unwanted Programs) and distinct families of Cryptolocker spread fear among larger businesses worldwide through massive attacks and the theft of thousands of confidential files.
Trojans continued to be the main source of malware (51.45%), comfortable positioned ahead of the rest of the collected samples: viruses (22.79%), followed by worms (13.22%), PUPs (10.71%), and cases of Spyware (1.83%).
Apart from all harmful Trojans, Cryptolocker (a type of ransomware) was the main protagonist of cyberattacks throughout the year. According to Corrons, “Cryptolocker is the best bet for cybercriminals, as it is one of the easiest ways of getting money. Also, it has shown itself to be very effective, especially in the case of businesses that don’t think twice about paying to recover their stolen information”.
Biggest infections caused by Trojans
Among all types of malware that cause large infections worldwide, it was Trojans that had the greatest rate of infection (60.30%), albeit 5% down on the figure from 2014.
PUPs were also particularly harmful, with nearly a third of infections resorting to trick techniques to fully enter the targeted PCs, far ahead of Adware / Spyware (5.19%), worms (2.98%), and viruses (2.55%).
China remains one of the most infected countries in the world
Last year was notable for being the year with the highest rate of infections caused on computers. On a geographic level, China was the country with the most infected computers (57.24%), a figure that was nearly 30% more than in 2014. Taiwan was next, with an infection rate of 49.15%, followed by Turkey (42.52%). These three countries remain at the top of the infection rate rankings, just as they were in 2014 and 2013.
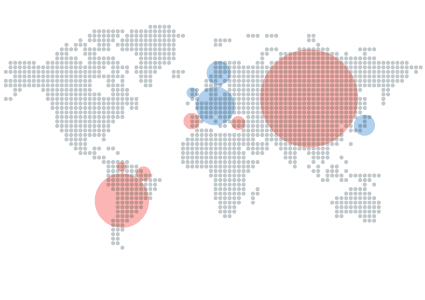
Other countries that registered an infection rate that was above the global average included Colombia (33.17%), Uruguay (32.98%), and Spain (32.15%).
Nordic countries register the lowest rate of infection
According to the information gathered regarding countries with the lowest rates of infection, nine of them were in Europe, with Japan being the only country not located in the continent.
The Nordic countries occupied the top positions: Finland was ahead of the rest, with a rate of 20.32%, followed by Norway (20.51%) and Sweden (20.88).
The post 27% of all recorded malware appeared in 2015 appeared first on MediaCenter Panda Security.
Attacks on Android and large-scale infections are among the main security threats in 2016

Panda Security, global leader in cloud based security solutions, has announced its predictions regarding the main problems that could affect IT security in 2016. The coming year will be filled with threats that could affect private users, small businesses, and large corporations.
The creation and spreading of new malware samples, aimed at infecting users, will continue growing at an exponential rate, just as we have seen in in 2015 where the number of new samples registered daily reached 230,000.
During 2016 there is a predicted increase in infections via JavaScript and a growth in the number of cybercriminals using Powershell, a tool included in Windows 10 that allows scripts with all types of functionalities to be executed, which could be used to attack users.
Large scale and mobile based attacks
Cybercriminals are looking for ways to attack the greatest number of users and businesses, while achieving the greatest possible profit.
Because of this, they will continue to use tools such as Exploit Kits, as many current solutions aren’t capable of combatting this type of attack effectively, which means its rate of infection is very high. For the same reason, malware on mobiles will also increase, especially for Android, which is the most popular operating system on the market.
“Although Android attacks have been commonplace in recent years, the news for 2016 is the manner in which mobiles will be infected. We will see more threats that root the device, which makes eliminating it a near impossible task for an antivirus, except for those that come installed from the factory”, says Luis Corrons, Technical Director of PandaLabs.
There will also be an increase in direct attacks through rootkit techniques, which allow the hackers to hide themselves from the operating system and security solutions.
Internet of Things and mobile payment
2016 will be the year in which the Internet of Things flourishes, with more devices than ever connected to the Internet.
With this in mind, cybercriminals will carry out attacks on these devices, as we have already seen in 2015 in the case of cars whose software is connected to the Internet, which allowed for the remote control of the vehicle.
Payment platforms on mobile devices will be under scrutiny as cybercriminals looks to take advantage of them, as they could be easy ways for criminals to steal money directly.
“If any of the platforms becomes more popular compared to the others, it will be the first one to be looked at by the attackers as they search for weaknesses in its system”, continued Luis Corrons.
Main challenges for security
In the face of the current panorama, where the number of threats is growing exponentially and attacks are becoming more sophisticated, users and businesses will have to adopt extra security measures to remain protected against the dangers of the Internet in 2016.
What’s more, for businesses there are also threats that could seriously damage both their reputation and finances. Cybercriminals will make it their goal to steal confidential information relating to the company (financial data, strategic plans, etc.), and even information belonging to their customers. Once they have it, they will try to blackmail the company into paying a ransom to get the information back, a method known as Cryptolocker.
To face the complexity of these attacks, and those that await us in 2016, it will be necessary for users and businesses to have security tools and solutions that analyze and classify the behavior of all executables, and that also offer advanced protection to prevent and act against security threats.
The post Attacks on Android and large-scale infections are among the main security threats in 2016 appeared first on MediaCenter Panda Security.

