There are three main different types of antivirus solutions available for PC users: free, premium and default on the operating system. Here is some information we have found useful as you choose what is right for you.
![]()
There are three main different types of antivirus solutions available for PC users: free, premium and default on the operating system. Here is some information we have found useful as you choose what is right for you.
![]()

Shopping online is one of the reasons why we love the internet, but it’s not the only one. Video games are also a major reason. With more than 155 million Americans playing on their PC, game console, smartphone, wireless device or handheld system, gaming is more popular than going to the movies or listening to music.
![]()

![]()

After the massive data breaches of web giants Dropbox, Badoo, MySpace, Tumblr, LinkedIn and Yahoo! in September 2016 (the biggest massive piracy of individual data against a single company never made public), Dailymotion, one of the most visited video platforms in the world has been attacked. The French online video giant remains behind YouTube, bringing in more than 300 million unique visitors per month. More than 85 million accounts are affected by this massive data leak, which still makes it one of the most important attacks of the year.
LeakedSource sounded the alarm this week by acquiring some of the stolen data. According to them, Dailymotion’s database was victim to an intrusion in early October which allowed the hackers to recover the data of more than 85 million users: mainly identifiers, passwords and email addresses.
![]()
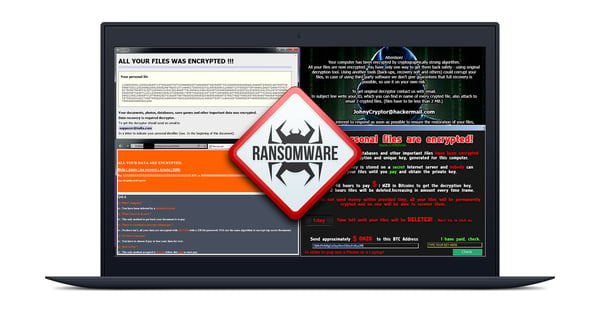
Within the last year, ransomware has risen to become the new “it” malware – we have seen a 105% year over year growth in ransomware attacks. Therefore, we are happy to announce today, that we have released four more ransomware decryption tools for the latest ransomware threats: Alcatraz Locker, CrySiS, Globe, and NoobCrypt. All the decryption tools are available, together with a detailed description of each ransomware strain. We now have tools to help you recover encrypted files if your computer has been infected with one of the following ransomware strains:
![]()
![]()
If your computer’s security relies on Windows BitLocker Hard Drive Encryption software, then Beware! Because anyone with physical access to your PC can still access your files within few seconds.
All an attacker need to do is hold SHIFT+F10 during Windows 10 update procedure.
Security researcher Sami Laiho discovered this simple method of bypassing BitLocker, wherein an attacker can open a
![]()
![]()

Earlier this summer, we told you about our proprietary CyberCapture technology. CyberCapture is a vital component of the Avast Antivirus Nitro Update, providing users with increased speed and a higher level of protection against zero-second attacks. In this post, I’d like to dive deeper into the engineering behind CyberCapture and explain the components that give the feature its technical integrity.
In essence, CyberCapture is a cloud-based smart file scanner. In order to provide immediate analysis, CyberCapture automatically establishes a two-way channel of communication with the Avast Threat Labs while securing suspicious files on the user’s PC until analyses are completed. Once a file has been isolated, our team can clear away all the false code, misdirection, obfuscation, and other stuff malware creators use to mask malware’s true intentions. By doing so, CyberCapture is able to dissect malicious file, observe the binary level instructions inside the malware, and understand the true purpose hidden within it.
![]()
You may have heard names like Cryptolocker or Heartbleed and wondered: Who comes up with these names? Why? The next question you may have is: Do all viruses and vulnerabilities get named?
![]()