Encrypted email service ProtonMail announced early Thursday that it had added its own Tor hidden service.
Tag Archives: Tor
Alpha Version of Sandboxed Tor Browser Released
A sandboxed alpha version of the Tor Browser was released over the weekend and while there are still some rough edges and bugs, it could be a step toward protecting Tor users from recent de-anonymization exploits.
Hackers Gamify DDoS Attacks With Collaborative Platform
A hacking group is luring participants to use a DDoS platform where they can compete with peers to earn redeemable points exchangeable for hacking tools and click-fraud software.
Mozilla Patches Firefox Zero Day Used to Unmask Tor Browser Users
Mozilla released a new version of Firefox on Wednesday to address a zero day vulnerability that was actively being exploited to de-anonymize Tor Browser users.
New Cerber Variant Leverages Tor2Web Proxies, Google Redirects
Researchers have discovered that criminals behind the latest Cerber ransomware variant are leveraging Google redirects and Tor2Web proxies in a new and novel way to evade detection.
Tor Update Fixes ReachableAddresses Problem
Tor updated its software to 0.2.8.7 and fixed a number of issues, including a bug in the ReachableAddresses option that possibly degrades anonymity.
Threatpost News Wrap, July 29, 2016
Mike Mimoso and Chris Brook discuss the news of the week, including a wireless keyboard vulnerability – KeySniffer, NIST’s statement on 2FA, a LastPass remote compromise bug, and a new Tor paper.
Core Tor Contributor Leaves Project; Shutting Down Important Tor Nodes
Another blow to the Tor Project: One of the Tor Project’s earliest contributors has decided to quit the project and shut down all of the important Tor nodes under his administration.
Lucky Green was part of the Tor Project before the anonymity network was known as TOR. He probably ran one of the first 5 nodes in the TOR network at its inception and managed special nodes inside the anonymity
![]()
Selfrando Technique Mitigates Attacks Unmasking Tor Users
A team of academics and researchers has developed a technique called selfrando that it says can defend against attacks that unmask users of the Tor Network.
Tor and the Deep Web: Secrets from the Dark Side of the Internet
The “Deep Web” or “Invisible Web” is on the rise. Humans are curious by nature, and more and more internet users are going to the dark side. Everyone knows that the internet is a never-ending source of information, and search engines like Google, Yahoo and Bing can quench our thirst for information using just a few key words, with lists of information within seconds. But, are you aware that most of us are only accessing a mere 4% of the World Wide Web?
To understand this concept, you must imagine the entire Internet as an Iceberg.
We only know the tip of the Iceberg: The Deep Web’s Structure.
Like we stated in the previous paragraph, to better understand the Deep Web, it’s imperative to think of the entire internet as an iceberg that is divided into five parts, with each part more submerged than the previous.
Level 1. At the tip of the iceberg we will find all pages that we are able to access using search engines. This part is visible and accessible for “simple mortals” and the information is completely traceable.
Level 2. Below the surface of the water, we will find pages or sites that are not indexed (in other words, sites that aren’t visible) using traditional search engines (like Google or Yahoo). Therefore, they are only accessible to those who are “qualified”.
Level 3. If we dive even deeper into the cold water surrounding our iceberg we will begin to see very hard to find—and mostly illegal—information.
Level 4. As we grow closer to the most submerged point of our iceberg we will be able to find every type of illegal website. Most of them are monitored by the United States government (for example, child pornography websites).
Level 5. Once we have passed the four levels in the Deep Web we will reach the most hidden part of the internet, known as “The Dark Net”. A hacker’s paradise, this part of the web is built on a series of private networks that can only be accessed by “trusted” users. This is the darkest part of the web: it is not governed under the standard protocols and there is no security.
Tor: How to Access it in the Deep Web
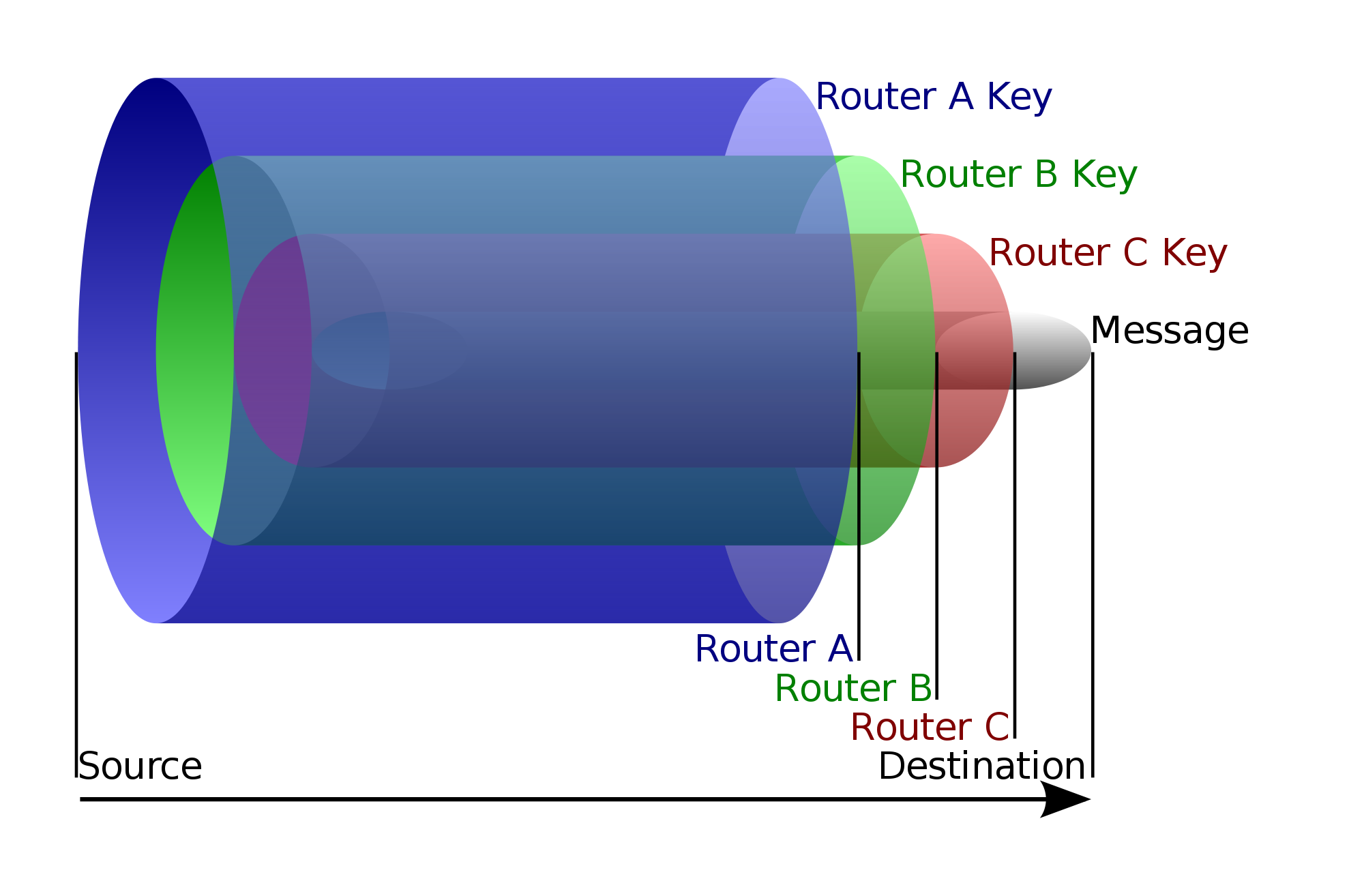
Everyone is capable of accessing the deepest parts of the web, but to do so you have to use alternative search engines. Tor (The Onion Router) is a free software program that was designed by the United States Naval Research in the mid-90s to protect US Intelligence communications online.
Tor has a layered structure (hence, its name) that enables the user to navigate by jumping from one layer to another, ensuring that the user is protected by a cypher that prevents them from seeing your IP address. One of the Deep Web’s main characteristics is user anonymity.
Is it really possible browse the web anonymously?
Industry experts say that connecting through Tor can be risky. Tor does not allow the user to control which proxy they connect to, which could lead to threats like man-in-the-middle attacks and JavaScript infections, which violate user privacy.
The best way to avoid these type of attacks is to control the parts you can, like: the kind of operating system (Windows, Linux, etc.), the origin of the connection, the trustworthiness of the information that we share, etc. Organized gangs remain anonymous in the “Deep Web” thanks to their skill and organization in each of these areas.
Although the world of the Deep Web seems very fascinating, we must consider the enormous dangers that we might find. Panda will not accompany you on this journey!
The post Tor and the Deep Web: Secrets from the Dark Side of the Internet appeared first on Panda Security Mediacenter.