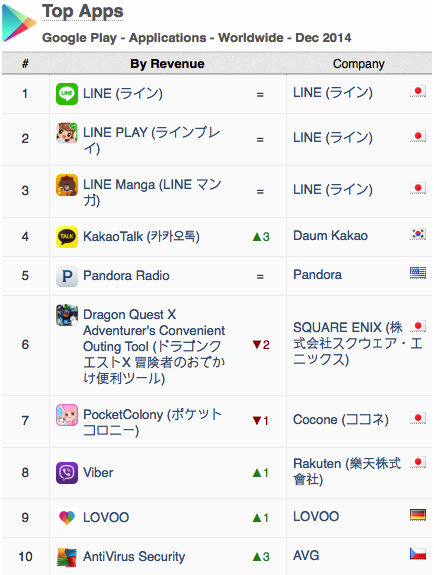
AVG’s position in the Top 10 chart is according to the App Annie Index for December 2014, produced by mobile app analytics company App Annie. The report, which analyzes trends and downloads for apps across all the major app stores, looks at both the popularity of apps and the revenue they drive.
In the report, App Annie details the incredible growth that they have tracked in security apps. And one year after climbing into the top ten apps for downloads, AVG AntiVirus PRO Android Security – referred to AntiVirus Security on Google Play – has become the first security app to enter the Top 10 Revenue Chart (excluding games) on the Google Play Store.
Proven demand
Increased demand comes after a busy 2014 for cybersecurity events and suggests consumers are more security conscious as a result.
There is demand for security apps – the continued popularity of AVG AntiVirus Security FREE, which was the first security app to exceed 100m downloads on Google Play, shows this. People, however, are not only protecting their devices with free security apps but are willing to invest in the solutions that they trust.
This is echoed in the recent MEF Global Consumer Trust Report where 64% of those studied use software or apps to guard passwords and protect against malware and only one in ten (11%) take no steps to protect their device.
Highly Rated
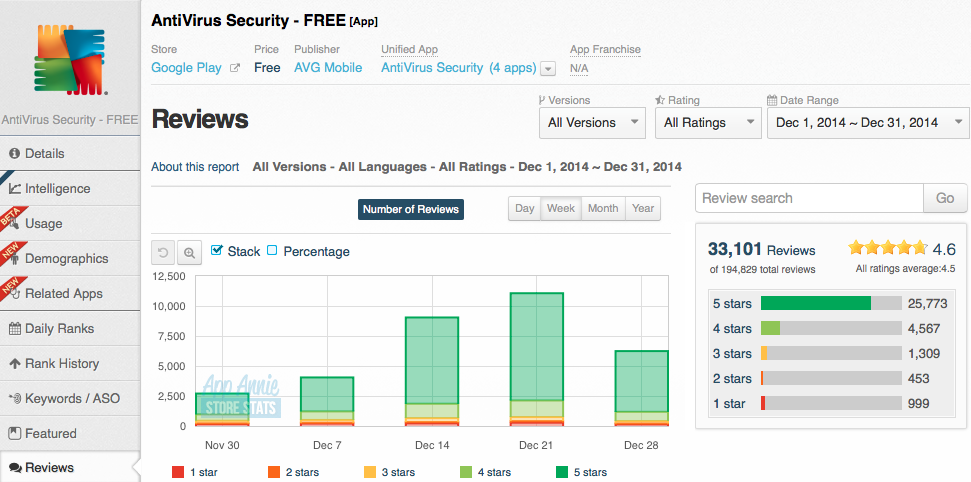
AppAnnie’s report also highlighted that AVG AntiVirus Security FREE is receiving overwhelmingly positive reviews from the public.
During December, AVG’s AntiVirus Security FREE received an average rating of 4.6 from over 33,000 reviews, with 77% of all users awarding us a maximum score of five stars.
The future is bright
At AVG, we’re already looking ahead to a world where mobile devices are not just secured, but integrated across the Internet of Things. Through AVG Zen, we deliver a single dashboard from which a customer can manage the security, privacy and performance of all their devices and those of their family, all in one place.