Mike Mimoso and Chris Brook discuss the week in news, including the Linux zero day–how it was patched in Android, Twitter users who are still looking for answers, and bot fraud.
Tag Archives: zero day
Mozilla Patches Bug Used in Active Attacks
Mozilla has released a patch for a vulnerability in Firefox that was discovered when a user found it being actively exploited in the wild.
Patches from Adobe, Oracle, and Microsoft released
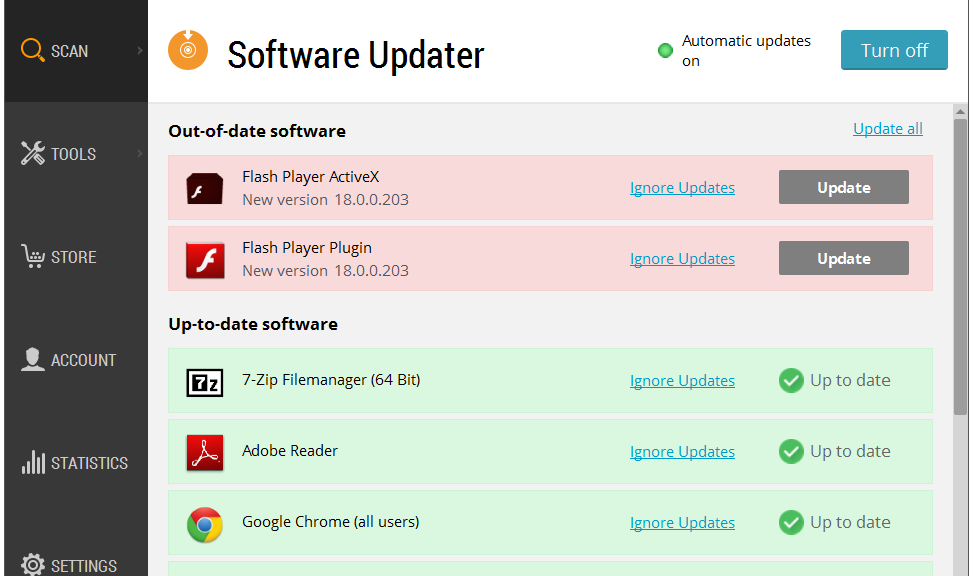
Avast Software Updater helps you apply software updates.
Earlier this week, we told our readers about the three Flash Player zero-day vulnerabilities that were found in stolen files that were leaked from the Hacking Team. We advised Avast users to disable Flash until the bugs are fixed.
It doesn’t look good for Flash. Because of the continuing security problems facing the 20-year old platform, Google and Mozilla each announced this week that their Web browsers will eventually be dropping default support for Adobe Flash, and Facebook’s new security chief wants to kill Flash. For now you can still use it, but the reports of it’s death are not greatly exaggerated…
Adobe has released security patches for Windows, Mac OS X, and Linux. Adobe Flash Player installed with Google Chrome will be automatically updated to the latest Google Chrome version. Users of Internet Explorer 10 and 11 for Windows 8.x will be automatically updated to the latest version.
Another Hacking Team zero-day vulnerability was discovered in Microsoft’s Internet Explorer. Microsoft released a total of 14 security bulletins, 4 ‘critical’ and the remainder ‘important’ in their July Security Bulletin.
And finally, Oracle released a security update to fix the Java zero-day exploit reportedly used to attack military and defense contractors from the U.S. and spy on NATO members. The Critical Patch Update Advisory also includes 193 new security updates; 99 of which could be exploited by remote attackers.
Avast Software Updater can help you with most software updates. To find it, open your Avast user interface. Click Scan on the left side, then choose Scan for outdated software. You an then decide how to proceed.
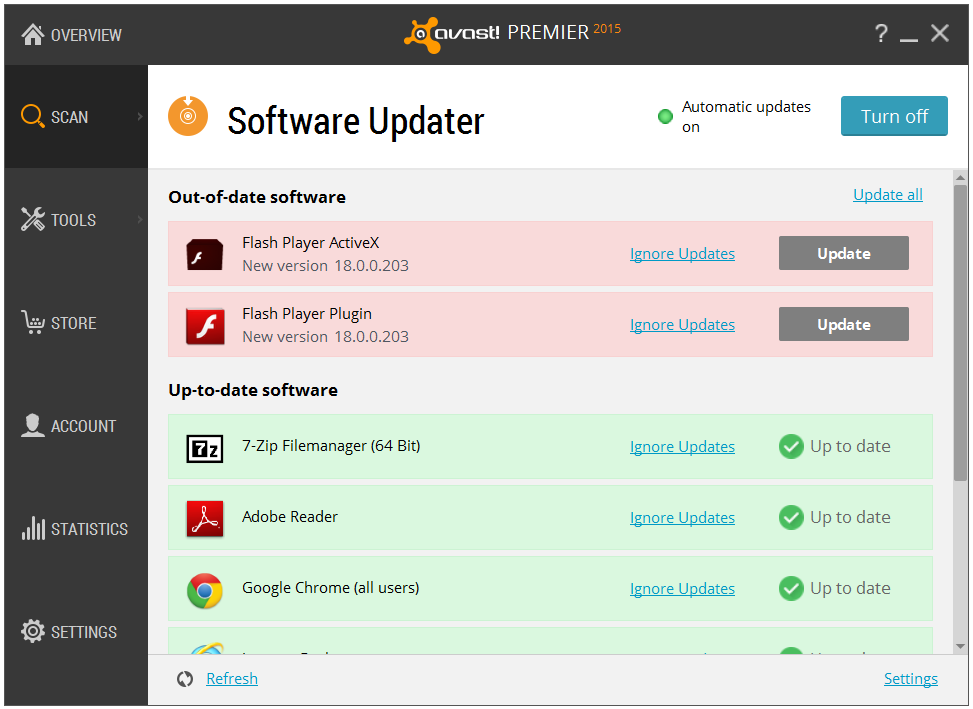
Avast Software Updater shows you an overview of all your outdated software applications
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
Adobe Flash zero-day vulnerabilities threaten your security
Last Friday, Adobe confirmed two new “critical” zero-day flaws in the Adobe Flash Player browser plugin 18.0.0.204 – and earlier versions – for Windows, Mac OS X, and Linux. Today, a third flaw was found. Adobe Flash Player is a widely distributed multimedia and application player used to enhance the user experience when visiting web pages or reading email messages.
We recommend disabling Flash until the bugs are fixed.

Three “critical” Flash zero-day flaws in Adobe Flash Player discovered
Security experts say the two flaws were found in stolen files that were dumped earlier this month from Hacking Team, an Italian security firm that sells communication interception and surveillance software to governments around the world. The third one came from the same documents.
“Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system,” Adobe said in their blog. “Depending on the privileges associated with the user account targeted, an attacker could install programs on the system, alter or delete data, create new accounts with similar user rights, or cause a denial-of-service.”
“Adobe is aware of reports that exploits targeting these vulnerabilities have been published publicly. Adobe expects to make updates available during the week of July 12, 2015,” the blog said.
We recommend you do the following:
- Remove or disable Flash until Adobe sends out a fix.
- Once a patch is released by Adobe, update immediately.
- Run all software as a non-privileged user (one without administrative privileges) to diminish the effects of a successful attack.
- Avoid visiting websites or following links provided by unknown or untrusted sources.
- Avoid clicking on links contained in emails or attachments from unknown sources.
To verify the version of Adobe Flash Player installed on your system, access the About Flash Player page, or right-click on content running in Flash Player and select “About Adobe (or Macromedia) Flash Player” from the menu. If you use multiple browsers, perform the check for each browser you have installed on your system.
Affected systems:
- Adobe Flash Player 18.0.0.203 and earlier for Windows and Macintosh
- Adobe Flash Player 18.0.0.204 and earlier for Linux installed with Google Chrome
- Adobe Flash Player Extended Support Release 13.0.0.302 and earlier for Windows and Macintosh
- Adobe Flash Player Extended Support Release 11.2.202.481 and earlier for Linux
![]()
Adobe to Patch Hacking Team Zero Day in Flash
Adobe is expected tomorrow to patch a Flash zero day vulnerability uncovered among the data stolen in the Hacking Team breach.
US Navy Soliciting Zero Days
A RFP, which has since been taken down, surfaced last week from the Naval Supply Systems Command seeking operational exploits and vulnerability intelligence for commercial software from leading IT vendors.
Bug Bounties in Crosshairs of Proposed US Wassenaar Rules
Bug bounties and rewards programs provide researchers with a measure of income, and if the proposed Wassenaar rules are implemented in the U.S., that initiatives could be adversely impacted.
Will Windows 10 leave enterprises vulnerable to zero-days?
One thing Microsoft has been very public about is Windows 10’s new strategy of releasing patches to update the operating system at different times for consumer and enterprise versions.
The post Will Windows 10 leave enterprises vulnerable to zero-days? appeared first on We Live Security.
Seagate Confirms NAS Zero Day, Won’t Patch Until May
Seagate confirmed a publicly disclosed vulnerability in one of its network attached storage products, but said it won’t have a patch available until May.
Zero-day exploit affects popular WordPress plugin
The Fancybox plugin for WordPress has been hit by a zero-day exploit that allows hackers to inject malicious code into websites, reports ZDNet.
The post Zero-day exploit affects popular WordPress plugin appeared first on We Live Security.