How does MW get into systems?
This ransomware’s initial infection vector occurs when it’s sent/received through Phishing campaigns.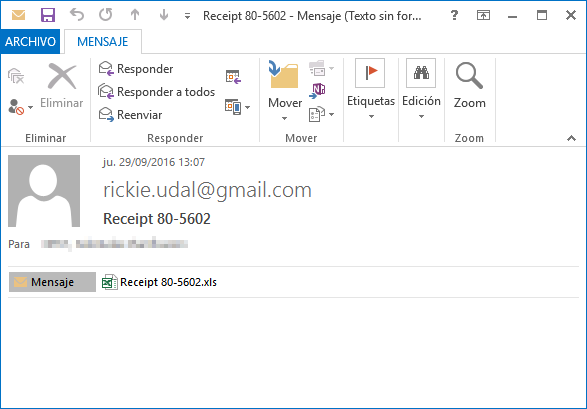
First, the user receives an email with the malicious file in zip format, giving the illusion it is a zip, but in this case, the user also receives some type of invoice; this varies depending on the message received or the name of the file. On this occasion, the received file has the following name: Receipt 80-5602.zip, as seen in the screen capture.
In this compromised file you will find a Microsoft Office document, or more specifically, an Excel with the extension “.xls” containing macros (codes are in Visual Basic Script)
How is this Code/Macro Executed?
By defect, unless we have the macro execution forced in Excel, the damaged code will not automatically run, unless, an advertisement appears indicating that the document contains macros, as demonstrated in the second screen capture.
And…What is this Macro?
The basic feature of this macro is to use the “dropper”, what we mean is, download and execute the other binary file, in this case a file encrypter or ransomware; although it could have been another malicious program like RATs, backdoors, bots, etc.
In this case, as with droppers, the file (or payload) runs on a remote server when executed.
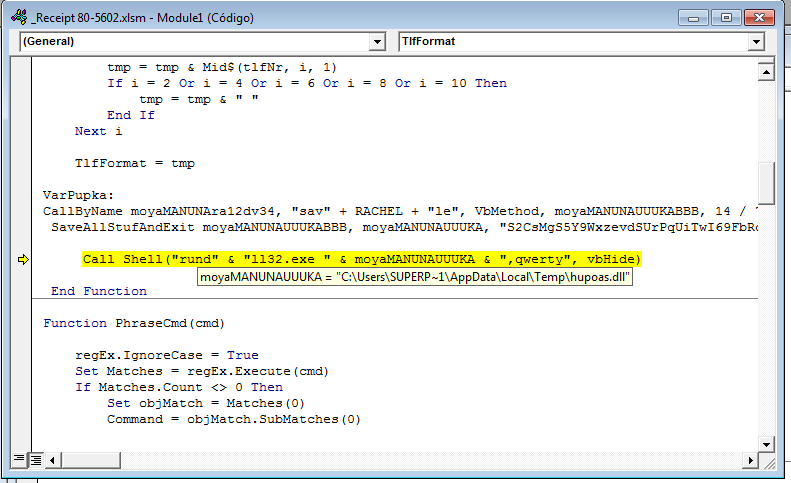
Once the macro is executed, it is now in charge of taking the next steps: downloading and deciphering the remote file that is encrypted, and afterwards, ejecting it.
If we look at the name of the file running from the macro, or its command-line execution, we will see that the ransomware comes by DLL format; this has become increasingly more common. In addition, it requires that an export is indicated to operate, in this case “qwerty”, as shown in the following screen shot:
Why do it this way? Simply because a lot of systems that update the malware analysis (sandboxes) have problems when they execute programs/codes/libraries that require parameters, that are sometimes unknown.
Once encrypted, this library’s MD5: 586aaaaf464be3a4598905b5f0587590
Finally, from PandaLabs we would like to give you the following advice: if you don’t want to have an unwanted surprise, when you receive Office documents from unknown senders do not click the button that says “activate macros”. Lastly, make sure your antivirus solutions and systems are always up-to-date!
The post Tales from Ransomwhere: Macros & Ransomware(s) appeared first on Panda Security Mediacenter.