Debian Linux Security Advisory 3029-1 – Antoine Delignat-Lavaud and Karthikeyan Bhargavan discovered that it was possible to reuse cached SSL sessions in unrelated contexts, allowing virtual host confusion attacks in some configurations by an attacker in a privileged network position.
Monthly Archives: September 2014
Debian Security Advisory 3030-1
Debian Linux Security Advisory 3030-1 – Multiple SQL injection vulnerabilities have been discovered in the Mantis bug tracking system.
Ubuntu Security Notice USN-2350-1
Ubuntu Security Notice 2350-1 – The NSS package contained outdated CA certificates. This update refreshes the NSS package to version 3.17 which includes the latest CA certificate bundle.
Ubuntu Security Notice USN-2351-1
Ubuntu Security Notice 2351-1 – Antoine Delignat-Lavaud and Karthikeyan Bhargavan discovered that nginx incorrectly reused cached SSL sessions. An attacker could possibly use this issue in certain configurations to obtain access to information from a different virtual host.
Ubuntu Security Notice USN-2352-1
Ubuntu Security Notice 2352-1 – Simon McVittie discovered that DBus incorrectly handled the file descriptors message limit. A local attacker could use this issue to cause DBus to crash, resulting in a denial of service, or possibly execute arbitrary code. This issue only applied to Ubuntu 12.04 LTS and Ubuntu 14.04 LTS. Alban Crequy discovered that DBus incorrectly handled a large number of file descriptor messages. A local attacker could use this issue to cause DBus to stop responding, resulting in a denial of service. This issue only applied to Ubuntu 12.04 LTS and Ubuntu 14.04 LTS. Various other issues were also addressed.
Red Hat Security Advisory 2014-1281-01
Red Hat Security Advisory 2014-1281-01 – The kernel packages contain the Linux kernel, the core of any Linux operating system. An out-of-bounds memory access flaw was found in the Linux kernel’s system call auditing implementation. On a system with existing audit rules defined, a local, unprivileged user could use this flaw to leak kernel memory to user space or, potentially, crash the system.
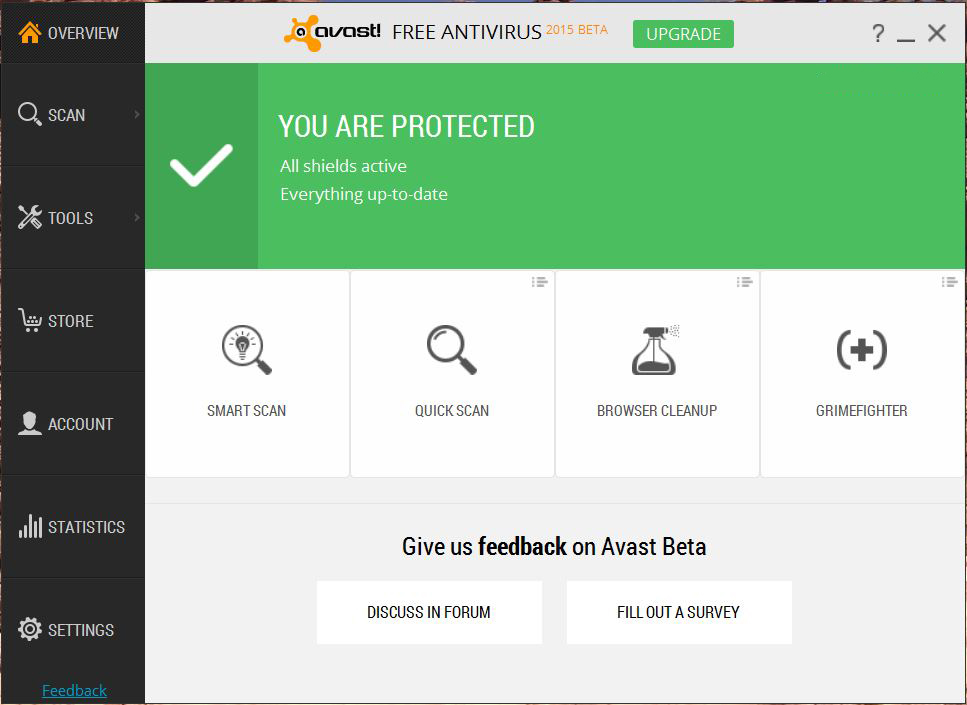
Join the Avast Beta 2015 and share your feedback
The Avast developers invite you to participate in the Avast 2015 beta test.
Your participation gives the team working on the latest versions of the world’s most trusted security products a chance to hear your voice – what’s working for you and what is not, how you like the experience, if you see performance or connectivity problems, etc. There are multiple new low-level functions which impact the whole system, so we need your feedback to tune everything for the final release.
Two new features introduced in Avast Beta 2015
Avast NG
Avast NG is a hardware-based virtualization solution capable of running each Windows process in a standalone, safe, virtualized environment (VM) which is fully integrated to your desktop. Each process is executed in its own instance of VM, which means it’s totally isolated from other applications. This feature is now powering Avast DeepScreen, resulting in better detection. The technology will also power the Sandbox and SafeZone components in the final release.
GrimeFighter Free
GrimeFighter will offer free cleaning of junk files and tuning of system settings. These tasks are performed by our Zilch and Torque minions.
Changes and other new features
- Home Network Security scans your home network for vulnerabilities like WiFi status, connected devices, and router settings.
- HTTPS scanning is able to detect and decrypt TLS/SSL protected traffic in our Web-content filtering component. This feature will protect you against viruses coming through HTTPs traffic as well as adding compatibility for SPDY+HTTPS/ HTTP 2.0 traffic.
- SecureDNS protects against DNS Hijack on router/client including unsecured networks, public ones, etc. This feature is active in the paid versions only.
- Smart Scan integrates all on-demand scans into one scan with different results and recommendations. Includes Antivirus, Browser plugins, Software updates, Home Network, and GrimeFighter.
To learn more about the Avast Beta 2015 , what to test, known issues, and to leave comments, visit the avast! Community forum thread dedicated to the beta test.
Avast Beta 2015 installation links
http://files.avast.com/beta9x/avast_free_antivirus_setup.exe
http://files.avast.com/beta9x/avast_pro_antivirus_setup.exe
http://files.avast.com/beta9x/avast_internet_security_setup.exe
http://files.avast.com/beta9x/avast_premier_antivirus_setup.exe
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
TP-LINK WDR4300 XSS / Denial Of Service
TP-LINK WDR4300 suffers from cross site scripting and denial of service vulnerabilities.
Kyle and Stan Malvertising Network Nine Times Bigger Than First Reported
The Kyle and Stan malvertising network has compromised more than nine times as many domains as originally reported two weeks ago.
[ MDVA-2014:014 ] mediawiki
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Advisory MDVA-2014:014 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : mediawiki Date : September 22, 2014 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: This update provides MediaWiki 1.23.3, which fixes several bugs. _______________________________________________________________________ References: http://advisories.mageia.org/MGAA-2014-0170.html _______________________________________________________________________ Updated Packages: Mandriva Business Server 1/X86_64: a4c54a101474c76abb19b62aa49dc12d mbs1/x86_64/mediawiki-1.23.3-1.mbs1.noarch.rpm 876aa46509eca08888392ea248a669ef mbs1/x86_64/mediawiki-mysql-1.23.3-1.mbs1.noarch.rpm 2418d49bba28fe6dd1b57805e