Red Hat Security Advisory 2014-1265-01 – In accordance with the Red Hat OpenShift Enterprise Life Cycle Policy, the two-year life cycle of Production Support for version 1.2 will end on November 27, 2014. In addition, technical support through Red Hat’s Global Support Services will no longer be provided after this date.
Monthly Archives: September 2014
Red Hat Security Advisory 2014-1263-01
Red Hat Security Advisory 2014-1263-01 – Red Hat Storage is software-only, scale-out storage that provides flexible and affordable unstructured data storage for an enterprise. GlusterFS, a key building block of Red Hat Storage, is based on a stackable user-space design and can deliver exceptional performance for diverse workloads. GlusterFS aggregates various storage servers over network interconnections into one large, parallel network file system. A denial of service flaw was found in the way Python’s SSL module implementation performed matching of certain certificate names. A remote attacker able to obtain a valid certificate that contained multiple wildcard characters could use this flaw to issue a request to validate such a certificate, resulting in excessive consumption of CPU.
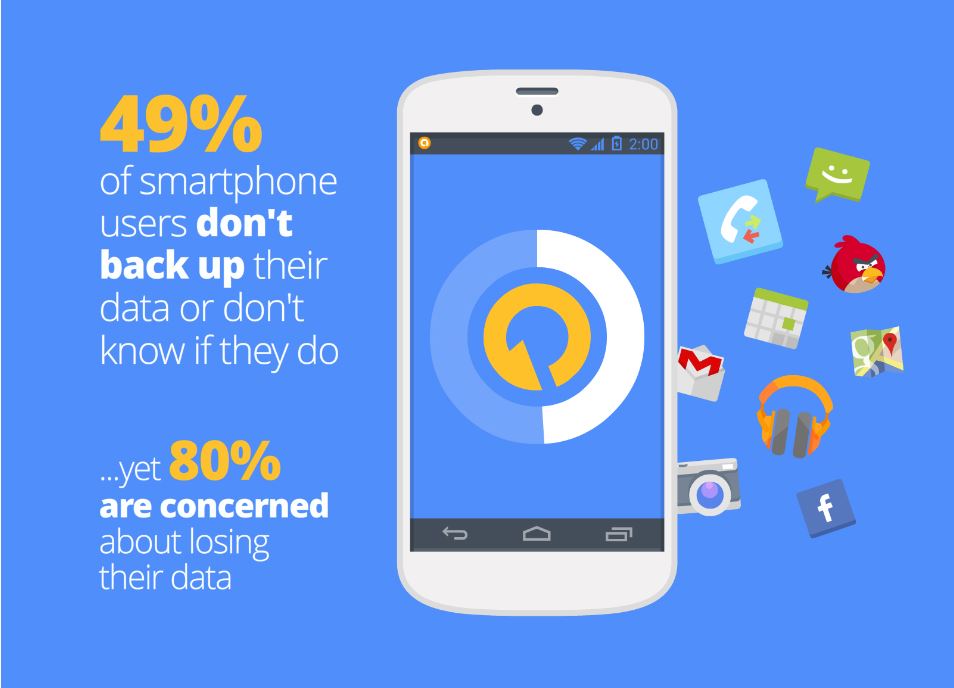
How to make a backup with avast! Mobile Backup & Restore
 Question of the week: I have lots of photos on my phone from summer vacation. How do I back them up so I don’t lose them?
Question of the week: I have lots of photos on my phone from summer vacation. How do I back them up so I don’t lose them?
These days we keep everything from photographs, videos and music to messages and contacts on our mobile devices. This makes losing our phones a big headache. Unfortunately, most people don’t think of this until after their phone goes missing or fails. We asked our users if they back-up their data, and a whopping 49% said they don’t back up or don’t know if they do.
avast! Mobile Backup makes backing up your important data easy for you. In a few easy steps, you can backup all your files from the pictures of your last trip to the contacts and applications you keep in your devices.
Want to know how? Just follow the following steps:
- Install avast! Mobile Backup & Restore from Google Play.
- Once you have installed avast! Mobile Backup, you’ll need to configure your Google Drive. It’s as simple as clicking on the button “Set up Google Drive Account” and follow the simple steps on the screen to access your Google account.

- Once you’ve set up your Google Drive, you can select items for backup. The free version lets you back up contacts, calls and SMS. The Premium version also allows you to back up all the audio and video files and also all your applications. When you finish the selection, click the “Continue” button.
- On the next page, “Important Options”, you can select whether you want the backups to be made only through a WiFi connection in order to save mobile data, and configure the maximum size of the files which you want to perform that backup. Once you’ve configured everything, click Finish.
- You are now ready to perform the backup. Tap the dark square at the top and avast! Mobile Backup will start backing up your files.
If you want to restore your backup when you change your phone, simply reinstall avast! Mobile Backup, click “Browse backup” and then “Restore all.”
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
OWASP Releases Latest App Sec Guide
OWASP published the latest iteration of its Testing Guide, an informational manual designed to teach developers how to build and maintain secure application.
iOS 8. Apple increases user privacy

No doubt if you have an Apple device, you’ll know that the new iOS 8 operating system is now available. What you might not know is that installing it will prevent Apple from accessing users’ devices without their consent.
This has been announced by the company, which says that “unlike their competitors” they will not access users’ systems without their permission. They claim that it is therefore not technically possible for them to comply with government orders to retrieve data from devices running iOS 8.
So how is privacy enhanced with iOS 8? To prevent itself from accessing these devices, Apple has modified its encryption system which is applied automatically when users select their password.
This way, Apple’s new operating system has taken a step forward in increasing privacy, as all the information stored on users’ iPads or iPhones (photos, emails, files, etc.) will be protected not only from Apple, but also from governments.
This is clearly how Apple has responded to accusations of collaboration with the National Security Agency (NSA) by handing over its customers personal data. Similarly, the company has also assured that it only provided the data of “less than 0.00385%” of Apple device users. ”
We remind you that it’s important to scan your iPhone or iPad for malware that could affect the functionality of your device. For your peace of mind, try our antivirus for Mac.
More | Cyber-espionage. Can you avoid it?
The post iOS 8. Apple increases user privacy appeared first on MediaCenter Panda Security.
Comprehensive Guide To Obliterating Web Apps Published
Jihadi Terrorists DIDN'T Encrypt Their Comms Because Of Snowden Leaks
US Military Contractors 'Hit By Chinese Hackers'
Apple Expands Data Encryption Under iOS 8, Making Handover To Cops Moot
The dangerous side of USB convenience
How many USB devices do you own? At this moment, you probably have one or more of them connected to your computer. USB devices are everywhere, and they come in the form of flash drives, webcams, keyboards, and so on. One of the attractive things about a USB connection is that you just plug in a device and it works. That convenience, while nice to have, presents a real danger.
For years, many computer users have just plugged in USB devices without putting much thought into any vulnerabilities they might present, but hackers have found ways to prey on the carefree nature of USB usage. You may remember the Stuxnet worm that targeted nuclear facilities in Iran. USB flash drives were used to initiate the infections, and this brought a lot of attention to how USB devices could play a key role in ITÂ attacks.
Fast-forward a few years to today and USBs are a hot security topic once again because of details revealed by security researchers about an exploit called BadUSB. Essentially, the BadUSB hack makes it possible to reprogram the firmware on USB devices, which means that they can then be used maliciously. Since the majority of USB devices will just accept any firmware update that they’re offered, it’s really difficult to know if the firmware on your device is secure or not.
That said, any malware introduced via USB can be detected, depending on the payload. It is why we can consider #BadUSB as being a means to install malware on a machine rather than being a specific virus or malware itself.
Because of the insidious way in which this hack works, protecting yourself from it is really difficult at this point. One of the most logical things that you can do is to make sure that the USB devices that you use have remained only in your possession. USB flash drives in particular tend to get passed between people on a regular basis, but based on this new information, that’s not always such a good idea.
The post The dangerous side of USB convenience appeared first on Avira Blog.