Monthly Archives: September 2014
Archie Exploit Kit Targets Adobe, Silverlight Vulnerabilities
A relatively new exploit kit that exploits old versions of Adobe Flash, Reader and, Silverlight has begun to make the rounds.
Ubuntu Security Notice USN-2348-1
Ubuntu Security Notice 2348-1 – It was discovered that APT did not re-verify downloaded files when the If-Modified-Since wasn’t met. It was discovered that APT did not invalidate repository data when it switched from an unauthenticated to an authenticated state. It was discovered that the APT Acquire::GzipIndexes option caused APT to skip checksum validation. This issue only applied to Ubuntu 12.04 LTS and Ubuntu 14.04 LTS, and was not enabled by default. Various other issues were also addressed.
Delphi And C++ Builder VCL Library Heap Buffer Overflow
Core Security Technologies Advisory – Applications developed with Delphi and C++ Builder that use the specific integrated graphic library detailed in this advisory are prone to a security vulnerability when processing malformed BMP files.
Cart Engine 3.0 XSS / Open Redirect / SQL Injection
Cart Engine version 3.0 suffers from cross site scripting, open redirection, and remote SQL injection vulnerabilities.
Laravel 2.1 Hash::make() bcrypt Truncation
Laravel version 2.1 fails to check length prior to password hash creation allowing for possible hash collisions for secrets over 72 characters.
Phpwiki Ploticus Remote Code Execution
The Ploticus module in PhpWiki 1.5.0 allows remote attackers to execute arbitrary code via command injection.
Adobe Releases Security Updates for Adobe Reader and Acrobat
Original release date: September 16, 2014
Adobe has released security updates for Adobe Reader and Acrobat for Windows and Macintosh. Exploitation of these vulnerabilities could potentially allow an attacker to take control of the affected system.
US-CERT encourages users and administrators to review Adobe Security Bulletin APSB14-20 and apply the necessary updates.
This product is provided subject to this Notification and this Privacy & Use policy.
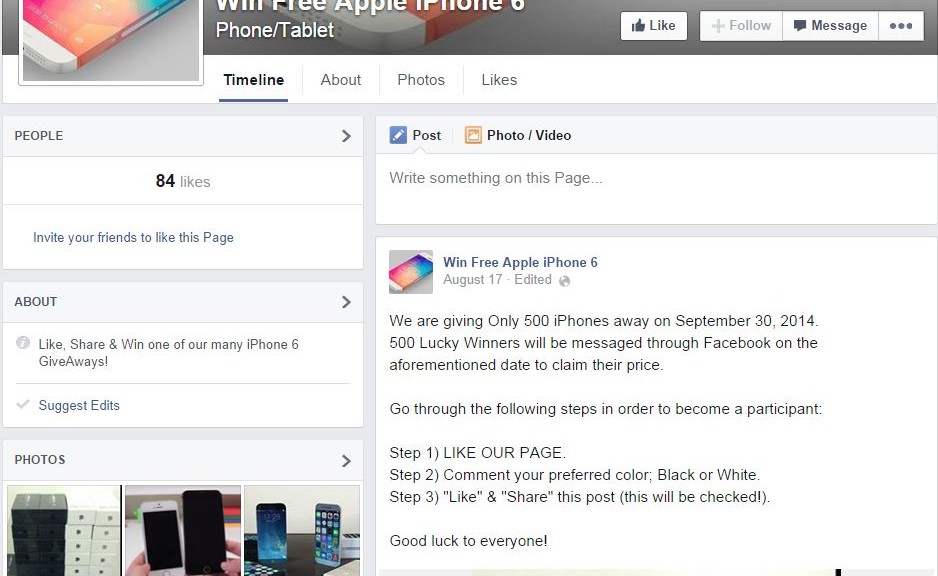
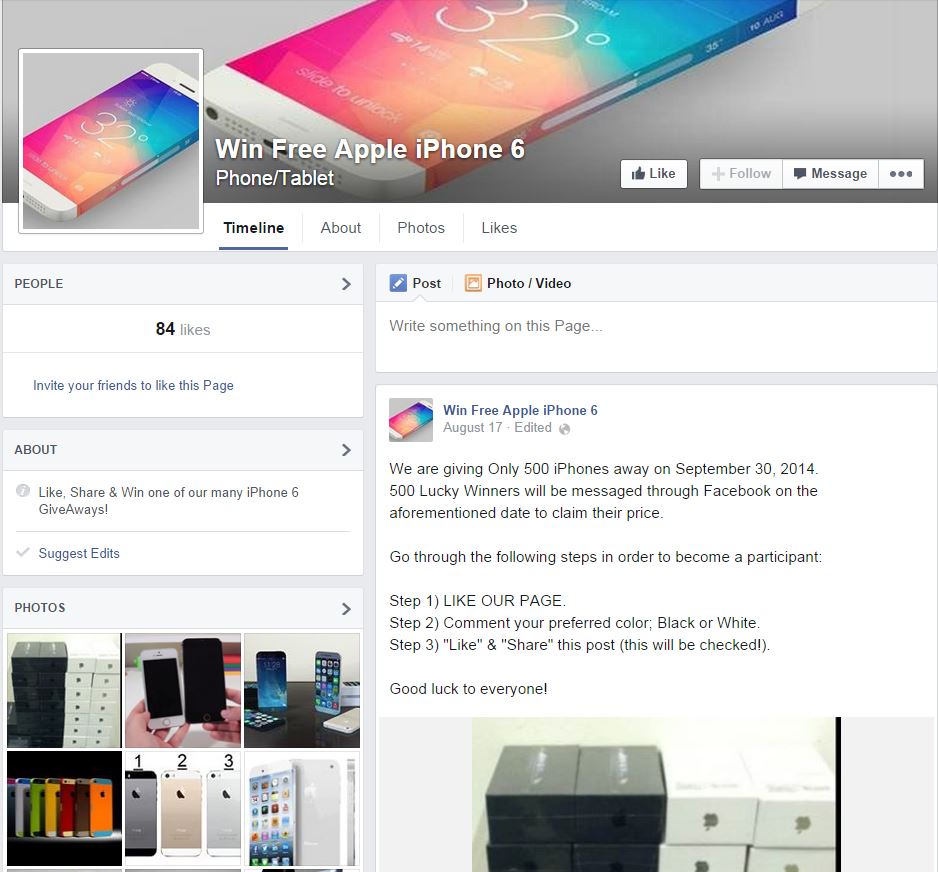
‘Win iPhone 6’ scams fool Facebook users, pad scammers pockets
It only took Apple 24 hours to get 4 million pre-orders of the new iPhone 6, and scammers were right there with them to cash in.
In the newest iteration of a scam used every time a new product is launched with fanfare, Facebook pages have been popping up claiming that people who like, share, and comment on a post can win an iPhone 6.
This type of scam is referred to as like-harvesting. The scammer makes the page popular by collecting likes and then sells the page to other scammers. The offer of a new device, like the iPhone 6, entices people to click the like button then spam their friends with the bogus promotion. Thousands of likes can accumulate within a few hours, making the page quite valuable on the black market. The new owner rebrands it to peddle more questionable products and services with their built-in audience.
A variation on this scam is the Survey Scam. As with like-harvesting, you must first like the Facebook page. The difference is that you need to also share a link with your Facebook friends.
This link takes you to a page where you are instructed to download a “Participation Application.†Generally, a pop-up window leads you to participate in a survey before you can download the application. Some surveys will ask for personal information like your mobile phone number or name and address. If you provide those details, you open yourself up to expensive text-messaging services, annoying phone calls, and junk mail. In some cases, the download contains malicious code. The only thing you can be guaranteed not to get is an iPhone 6! Meanwhile, the scammer earns money for every survey through an affiliate marketing scheme.
What to do if you liked a ‘Win iPhone 6′ page
If you fell for the scam, then learn from it and don’t do it again! Make sure you unlike the page, delete comments that you made, and remove the post from your news feed. You may also want to alert your friends to the scams, so they don’t fall for it.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
Is your business prepared to continue? Watch now and get started with BCM
Business continuity is a term that can sound strange the first time you hear it; after all, you probably have every intention of being in business for the long haul. Right now you may be preparing the 2015 sales forecast and budget, with hopes for a great year ahead. But in your planning, have you thought about how your business would handle the bad things that can happen, from a computer virus outbreak to a biological virus outbreak, and all the other perils in-between, like fires, floods, tornadoes, hurricanes, earthquakes, and tsunamis?
Putting a plan in place to survive such “adverse events” is the goal of business continuity management or BCM, and it could well be the key to securing your digital future. Here is a 50 minute webinar that I recorded on this topic earlier this year. If you want to get a handle on planning for the future of your business, take a listen:
The post Is your business prepared to continue? Watch now and get started with BCM appeared first on We Live Security.
![]()