When Malaysia Airlines Flight 17 (MH17) was shot down in Ukrainian airspace in July of this year, the world was understandably shocked.
The news of an civilian passenger flight from Amsterdam to Kuala Lumpur being possibly downed by a surface-to-air missile was horrifying enough, but coming just months after the loss of another Malaysian Airlines flight (MH370) in mysterious circumstances made the headlines seemed even harder to believe.
As we have previously documented on We Live Security, the earlier lost aircraft has been the subject of various scams including a fraudulent message that spread on Facebook claiming it had been found, a fake video of the supposed rescue of its passengers, as well as claims that hackers had stolen secret classified documents held by Malaysian government officials.
Now it appears, the cold-hearted scammers are exploiting the tragic events that befell MH17 over Ukraine too.
Part of the spammed out message reads as follows:
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
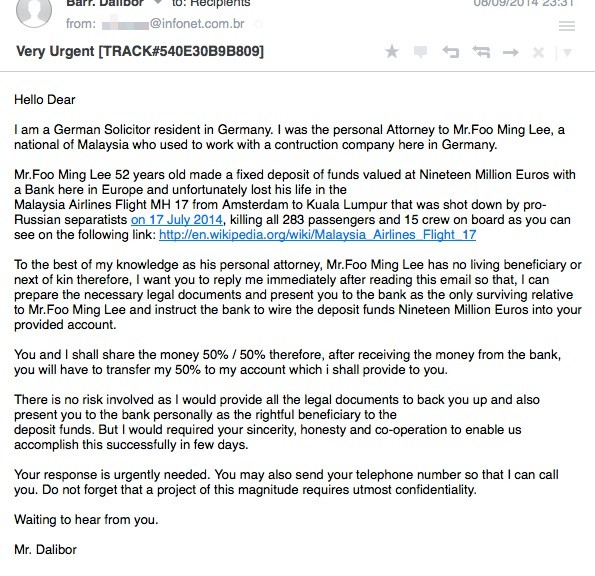
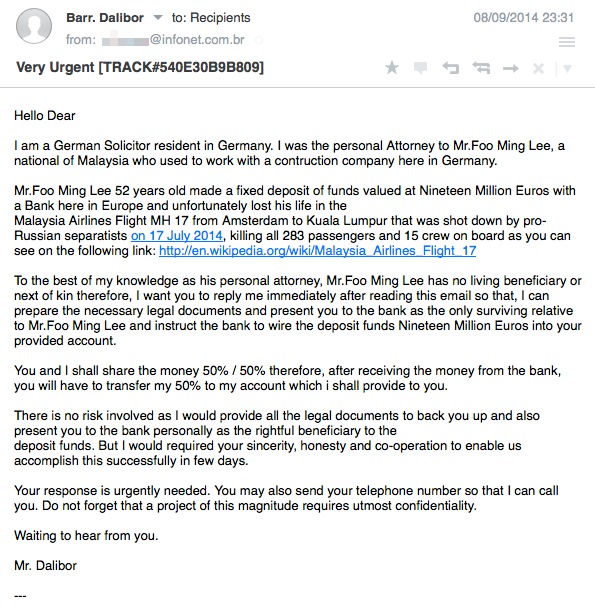
I am a German Solicitor resident in Germany. I was the personal Attorney to Mr.Foo Ming Lee, a national of Malaysia who used to work with a contruction company here in Germany.
Mr.Foo Ming Lee 52 years old made a fixed deposit of funds valued at Nineteen Million Euros with a Bank here in Europe and unfortunately lost his life in the
Malaysia Airlines Flight MH 17 from Amsterdam to Kuala Lumpur that was shot down by pro-Russian separatists on 17 July 2014, killing all 283 passengers and 15 crew on board as you can see on the following link: http://en.wikipedia.org/wiki/Malaysia_Airlines_Flight_17
To the best of my knowledge as his personal attorney, Mr.Foo Ming Lee has no living beneficiary or next of kin therefore, I want you to reply me immediately after reading this email so that, I can prepare the necessary legal documents and present you to the bank as the only surviving relative to Mr.Foo Ming Lee and instruct the bank to wire the deposit funds Nineteen Million Euros into your provided account.
Yes, it’s “yet another 419 scam”.
Also commonly known as “Letters from Nigeria” or “Advanced Fee Fraud”, the scams typically involve the promise of a vast fortune – but sooner or later (once you have begun to be sucked in and lost all wariness) you will be told that you need to advance an amount of money for logistical reasons, or share sensitive information such as your passport or banking details.
You might not fool for a scam like this, but unfortunately there are plenty of vulnerable people out there who do. And it only requires one person to fool for the scam for it to be worthwhile to the fraudsters, who have typically spammed it out to thousands.
But what makes this scam particularly sick is that it uses the name of a genuine victim of the MH17 tragedy.
As media reports confirm, Foo Ming Lee, who lived in Geneva and was a sales and marketing chief for a Japanese tobacco company, was indeed a passenger on MH17 and was amongst the 43 Malaysians who perished in the downing of MH17 over Ukraine.
It’s clear that whoever is behind this scam has scooped up the name of a victim from media reports, and exploited it in an attempt to defraud the unwary.
After all, anyone who was dubious about the unsolicited message might Google some of the details in an attempt to confirm if any elements of it could be confirmed to be true or not.
Yes, the plane crash happened on the date the scam claims, and Mr Foo Ming Lee was amongst the victims.
What is not true, however, is the claim that he had no next of kin. Another news report confirms that his widow, son and daughter laid his ashes to rest at Nirwana Memorial Park on August 24th.
If scammers had any conscience, they wouldn’t compound the misery of those who have been left bereaved and heartbroken by using the names of victims and details of horrendous accidents and tragedies in their money-making plots.
But the sad truth is that the scammers and fraudsters don’t have any conscience, and are prepared to do anything if it might net them a rich reward.
Hat-tip: Thanks to ESET researcher Pierre-Marc Bureau for bringing this scam to my attention.
The post MH17 plane crash victims exploited by cold-hearted scammers appeared first on We Live Security.