Monthly Archives: September 2014
Report: Businesses at Risk from Unreported Mobile Device Theft
Marketing Best Practices In The Digital Era
Security Concerns Over Online Financial Services Grow
Researchers Observe More than a Hundred Connections to 'Backoff' Sinkhole
VPN for beginners
Virtual private networks use a public network, usually the internet, to connect remote users together. Here, we take a closer looks at VPNS and help you choose the right one for your needs.Â
The post VPN for beginners appeared first on We Live Security.
![]()
Scareware: How to tell if a threat isn’t real
Scareware is a strategy that Cybercriminals use to trick users into buying and downloading unnecessary and potentially dangerous software. Listen to our top tips to identify whether a threat is real or not.
The post Scareware: How to tell if a threat isn’t real appeared first on We Live Security.
![]()
Bank security – Barclays to offer vein-scanner to big accounts
Barclays Bank is to allow remote log-ons using a hi-tech vein-scanning biometric bank security system for large corporate accounts, according to Engineering and Technology magazine. The bank security system, using Hitachi’s VeinHD scanner, will be available to corporate customers from next year.
The bank security scanner uses infrared light to capture an image of the veins of the customer’s index finger, and compares this against a pattern stored on a smart card (similar to the cards used to store details for Chip and PIN transactions).
Biometric finger vein scanning technology for authenticating online banking transactions will be available to Barclays’ corporate customers from next year, according to Reuters.
Bank security: Scanner ‘requires live finger’
The Telegraph reports that the technology will be available to Barclays Corporate Banking clients from next year, and says that the bank emphasized that the biometric scanner was one of the most secure on the market.
The paper says that a bank spokesperson said that the finger to be scanned, “must be attached to a live human body in order for the veins in the finger to be authenticated”.
Engineering and Technology points out that a finger vein pattern is nearly impossible to fake, unlike other common biometric identifiers, where fakes are produced with relative ease.
Hackers have “fooled†the scanners in both Samsung’s Galaxy S5 and iPhone 5S with fake fingerprints made from latex.
‘About the highest security you can get’
“If it had any known issues we would never ask our clients to go down that path. The security in finger vein scanning is about the highest you can get and that’s why we feel so confident in it,â€said Ashok Vaswani, chief executive of Barclays personal and corporate banking.
“Biometrics is the way to go in the future. We have no doubt about that, we are committed to it,” Ashwani.told Reuters in an interview. He said that fraudsters were constantly seeking new technologies to steal from the bank.
“You can’t let these guys create a breach in the dam. You’ve got to constantly stay ahead of the game.â€
Barclays said it expected strong take-up for the technology from its 30,000 corporate clients.
Reuters describes the scanner as “looking like a mini Star Wars stormtroooper helmetâ€, and that the pattern is matched with one stored on a smart card, signaling the bank to send an encrypted authorization code to the PC.
TechCrunch points out that vein recognition technology is already used to secure high-value banking transactions in countries such as Japan, but only as a secondary “layer†of security where other methods of authentication are also used.
At 15 payment machines dotted around the Swedish city of Lund, people can buy items using a similar vein scanner, and without a debit or credit card.
Engineering graduate Frederik Leifland says, “I got the idea when I was in line at the supermarket and I saw how complex a process paying is. It takes a lot of time, so I thought there must be an easier and quicker way to pay and that was the start of Quixter.â€
In a new interview with science website Humans Invent, Leifland explains how he hopes that his start-up may lead to payments without any authentication device. The pattern of veins in a human hand is unique – Leifland’s system uses infrared scans to identify the unique pattern in a finger.
BioMetrics sales site FindBiometrics says that the technology is relatively new, and currently used in high security institutions, saying, “Vein recognition is a fairly recent technological advance in the field of biometrics. It is used in hospitals, law enforcement, military facilities and other applications that require very high levels of security.â€
The post Bank security – Barclays to offer vein-scanner to big accounts appeared first on We Live Security.
![]()
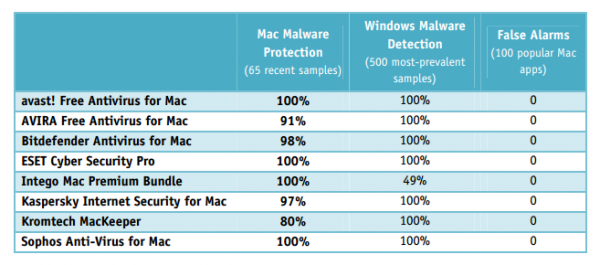
Avast! Free Antivirus for Mac outperformed competitor products in the independent tests!
Compared to Windows users, Mac users have been relatively unaffected by malware attacks. Cybercrooks, however, are just as aware as antivirus vendors are about Mac vulnerabilities. With the growing number of Mac users, cybercrooks see more potential for malicious activities, especially as Mac users tend to have a false sense of security and not usesecurity software. You only have to read this blog to learn that cybercrooks are adapting Windows malware to target their Mac counterparts.
We should never underestimate Mac security. Avast! Free Antivirus for Mac offers free protection against the latest malware designed to attack Mac operating systems. As all other Avast security products, the Mac version participates in frequent, independent tests. Recently avast! Free Antivirus for Mac was not only certified by AV-TEST but it also received 100% in the latest Mac Security Test & Review conducted by AV-Comparatives in July-August.
We are proud to share the results with you!
More about AVAST’s performance in both tests.
AV-TEST GmbH is a leading worldwide operating service provider for IT security testing services. The latest test was focused on Mac OS X security products and took place in July and August 2014. Eighteen AV products participated, and the tested platform was MacOSX 10.9.4. The results can be found here.
The new version 9 of avast! Free Antivirus for Mac has easily outperformed competitor products. The security software offered high malware detection rates, does not decrease Mac performance and did not cause false positives in our tests. ~ Andreas Marx, CEO of AV-TEST
Below is a short summary of AVAST’s performance!
Q:Â Which product was tested?
A: avast! Free Antivirus for Mac
Q: Which version was tested?
A:Â ’9.0 (41877)
Q: How did avast perform in the detection on-demand test?
A: Â avast! Free Antivirus for Mac received a scored of nearly 97.5%
Q: How did avast perform in the on-access detection test?
A:  avast! Free Antivirus for Mac scored 100%
Q: How many false positives were recorded in the on-demand and on-access tests?
A: None; avast  didn’t make any mistakes and recognized all malware correctly!
AV-Comparatives is an independent not-for-profit organization offering systematic security tests of antivirus products for PC and Mac, as well as mobile security solutions. The test conducted in July and August 2014 reviewed the performance of eight security software for OS X 10.9 Mavericks.
We found Avast’s phishing and malware alerts to be very good. The pop-up messages make it clear that the threat has been blocked and provide useful information for advanced users, such as the URL or file path (…) avast! Free Antivirus for Mac identified 100% of samples in both Mac malware and Windows malware tests and has a largely very straightforward program interface, albeit with the odd quirk.  ~ AV-Comparatives said in its report
Below, find the overview of avast’s performance versus its competitors
Last but not least, a picture is worth a thousand words, and we believe your Mac is worth it! Download it here.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter, Google+ andInstagram. Business owners – check out our business products.
Hackers in Hollywood, and Beyond
Many celebrities got an unpleasant shock this past weekend. You may have heard that up to 100 celebrities – film stars, etc. – had nude photos hacked and leaked on renegade Web site 4chan.org. Many of the photos were apparently genuine.
Now that the FBI is investigating how these photos were hacked and posted, it’s an unfortunate reminder of the difficulties of maintaining our privacy in this digital age.
I won’t name the celebrities involved, but it’s safe to say it’s a huge invasion of privacy. Some experts are theorizing that the hacker or hackers exploited weaknesses in Apple’s iCloud platform. Apple is now investigating, according to reports and released this statement. Here’s an excerpt: “After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud or Find my iPhone. We are continuing to work with law enforcement to help identify the criminals involved.â€
As a major player in the data security business, we think that this is just a reminder to everyone that when data goes digital, there are security risks involved. It’s a hard lesson.
As British actress Emma Watson (who was not targeted in the hacking) wrote on Twitter: “Even worse than seeing women’s privacy violated on social media is reading the accompanying comments that show such a lack of empathy.â€
Protecting yourself
How to protect yourself, even when you’re not a celebrity? Here are some tips, which we’ve stressed before but can’t stress enough:
- Create difficult passwords. Besides the speculation that iCloud was the victim, it has been suggested the hacker or hackers exploited each of the 100+ accounts’ passwords. As I’ve mentioned before, don’t use your birthday, and create multiple passwords for multiple accounts!
- Consider switching off automatic Cloud photo sharing and backups/Photo Stream. This is a convenience tradeoff. To turn off automatic iCloud sharing, go into your Settings, then iCloud, then scroll down to photos and slide the option to Off.
- Use encryption. Here I will proudly put in a plug for our own mobile phone encryption software, which protects your data against intrusion by encrypting your documents. This is a must for anyone storing private personal or important business intelligence on their phones.
- Think about using a USB drive. If you want to share personal information or photos with a specific person, just use a USB.
As celebrities, Apple, and the FBI come to grips with this specific hacking instance, it’s important to realize everyone’s information is at stake these days – celebrity or not –
And an excellent reminder that we need to actively protect ours.
![]()
![]()